5 Cyberattacks on the Maritime Sector (Nichols & Malhotra)
Abbreviations
AIS -Automated Information System (Anti-Collision)
APT- Advanced Persistent Threat
C/A – Civilian Acquisition code
CD- Collective Detection
CNO- Chief of Naval Operations
COTS- Commercial off-the-shelf
CPA- Closest Point Approach
CSS-Botnets – A network of interconnected devices that are infected with malware and controlled remotely
DDoS- Distributed Denial of Service
ECD – Eichelberger Collective Detection
GNSS- Global Navigation Satellite System
GPS- Global Position System
INDOPACOM AOR -US Indo-Pacific Command Area of Responsibility
ISMS- Information Security Management System
LOS- Line of Sight to the horizon
MTS-Maritime Transportation Sector
NDM- Navigation Data Modification
OT/IC- Operational Technology / Industrial Control Systems
OWASP- Open World Wide Application Security Project
P(Y) – Precise Signal
RATS- Remote Access Trojans
SIC- Successive Signal Interference Cancellation
SIEM- Security and Information Event Management
SNR – Signal-to-Noise Ratio
SOC- Security Operations Center
SSLT – Seamless Satellite-Lock Takeover
W3C – World Wide Web Consortium
Student Learning Objectives
Cybersecurity is a huge area to research, and it is updated almost daily for both attacks and defenses available to all actors. MTS is also a huge area to defend, as discussed in Chapter 1. We are looking to explore the following areas of interest with specialty threats and countermeasures (Nichols & Ryan, Defending Your Digital Assets Against Hackers, Crackers, Spies, and Thieves, 2000)
- Cyber Environment in the Maritime Transportation Sector
- Attacks via Cyber on the Maritime Transportation Sector
- How are the cyberattacks done?
- What is the most potent anti-spoofing countermeasure? Answer: ECD
- Need for a new cyber defense architecture
Cyber Environment in the Maritime Transportation Sector (MTS)
Let’s think about set theory and draw a large circle that encompasses the global MTS and a second large circle that encompasses all the tools, attacks, defenses, innovations, and actors of the worldwide sector called cybersecurity. The intersection of these two sets encompasses the cyber environment of the MTS. Our wildcat team tracks social media, the dark web, bloggers, and multi-government agencies that publish cyber-related research, documentation, cryptography, breach case studies, and news about current cybersecurity issues and events. It is a daunting task. Figure 5-1 shows the evolution of hacking tools up to 2016. (Adelaide Students Project, 2025)
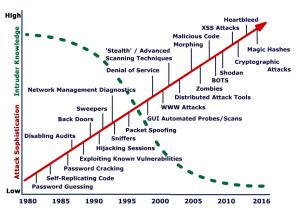
Kessler Figure 2.2 “Evolution of hacking tools and techniques, and the required knowledge of tool users” expands the 2016-2020 period to include Automated DDoS attacks, tools with GUIS, port scanners, APTS, RATS, CSS, Botnets, Hacking as a service, and Ransomware as a service. (Kessler & Shepard, 2022)
LINKEDIN has been a cornucopia of articles and quick reference guides for the MTS-Cybersecurity intersection set. Every day, we find a new checklist that fits the MTS-Cybersecurity intersection set. See Figures 5-2 to 5-10 for examples. [1]
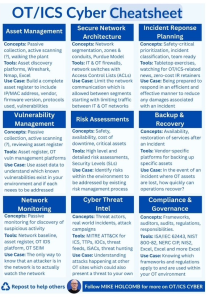


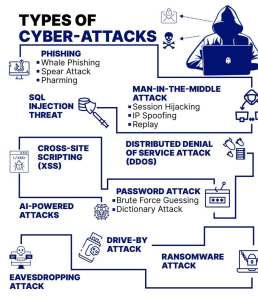



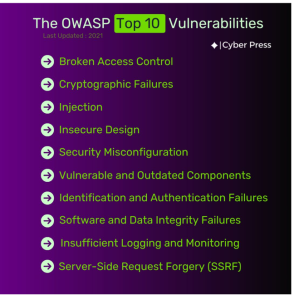
Figure 5-9 OWASP Top 10 Vulnerabilities (ICyber Press, 2025)
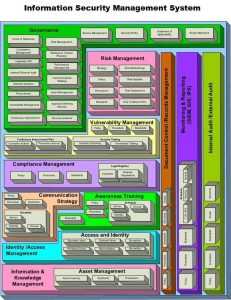
Figures 5-1 to 5-10 show that the MTS-Cybersecurity intersection is a very rich environment. Next, we look at some powerful attacks on the MTS and their effects.
Attacks via Cyber on the Maritime Transportation Sector and Their Execution
The Case and Argument for Early Effective Spoofing in the Pacific Against the US. Capital Ships (GNSS/GPS/AIS)
The author would like to represent somewhat verbatim a spoofing case that was originally published in Chapter 14, Maritime Security (Nichols R. K., et al., Unmanned Vehicle Systems & Operations on Air, Sea, Land, 2020) and various dedications of our textbook series. The case actually was the beginning of my 2017 continuing research into the issue of GPS Spoofing.
US Navy Vessel Collisions in the Pacific
“In 2017, there was a chain of incidents/collisions involving four US Navy warships and one US Navy submarine. On June 17, the destroyer USS Fitzgerald collided with the ACX, a 30,000-ton
container ship, resulting in seven deaths. Records show that the ACX turned sharply to starboard (right) at the time of the collision. The captain of the Philippine-flagged container ship accused the Navy destroyer of failing to heed warning signs before the crash. Those warning signs came from the commercial vessels’ Automated Collision Systems (AIS) on the bridge. On May 9, the guided-missile cruiser USS Lake Champlain collided with a South Korean fishing boat off the coast of Korea.
Peninsula. There were no injuries (Department of the US Navy, Office of Chief of Naval Operations, 2017). On January 31, the guided-missile cruiser USS Antietam ran aground, dumping more than 1000 gallons of oil into Tokyo Bay. On August 18, the ballistic missile submarine USS Louisiana collided with the Navy Offshore Support Vessel in the Strait of Juan de Fuca. There were no injuries.” (Nichols R. K., et al., Unmanned Vehicle Systems & Operations on Air, Sea, Land, (2020))
“On August 20, the guided-missile destroyer USS John S McCain collided with the 600-foot oil and chemical tanker Alnic MC at 0624 JST, resulting in ten dead (Navy Information Office, 2017)”. (Weise, 2017)” (Nichols R. K., et al., Unmanned Vehicle Systems & Operations on Air, Sea, Land, (2020))
“In all five incidents, the US Navy blames its field leadership for not responding appropriately. [2] This response implies that all five Navy vessels’ radar, emergency positioning alert systems, AIS, sonar, and long-range collision avoidance equipment must have been functioning perfectly without catastrophic failure or interference in difficult maneuverable waters or serious traffic. The Navy blames funding, readiness, and training. However, their response may not fully account for the commercial vessel accident data, actions required, or GPS positional data received” (Olson, August 30, 2017). (Nichols et al., Unmanned Aircraft Systems (UAS) in Cyber Domain: Protecting USAs Advanced Air Assets, 2nd Edition, 2019)” (Nichols R. K., et al., Unmanned Vehicle Systems & Operations on Air, Sea, Land, (2020))
The Navy’s Official Reaction regarding the possibility of a Cyber-Weapon or a Cyber-Attack
“The Navy has downplayed the possibility of a Cyber Weapon or Cyber Attack. Prior Chief of Naval Operations (CNO) Admiral John Richardson said in a tweet on Monday, August 23, referring to the USS McCain and USS Fitzgerald collisions, “there was no indication that the possibility of cyber intrusion or sabotage was involved or that the Navy ships were hacked, but the review will consider all possibilities.” (Weise, 2017) The Navy investigators, after inspecting the physical damage to the USS McCain and USS Fitzgerald, agree with the CNO’s conclusions (Olson, August 30, 2017).
“Navy experts in the technology and researchers at the University of Texas at Austin say there are certain scenarios they can imagine in which GPS hacks could have been used to foil ships’ navigation systems, but emphasize there is no evidence such attacks took place in the case of the Navy collisions.” (Weise, 2017) “The technology to jam or misdirect navigational software is readily available, though the Navy uses a much more robust encrypted version of GPS that would be very difficult to disrupt.” (Weise, 2017)
The only way to spoof such a system is a record and replay attack, “where a recording is made of the encrypted location data being sent from GPS satellites to the naval ship. Replaying the recording at a slightly later time could fool a ship into thinking it is somewhere else. This is a very sophisticated and difficult hack that requires multiple recordings of the navigation data stream from multiple angles and then sending the recorded signal from two or more locations.” (Weise, 2017) “To ensure that nearby ships do not also get the false data, it would have to be transmitted from close to the Navy ship being targeted, perhaps using multiple drones.” (Weise, 2017)
However, according to Professor David Lust, former president of the Royal Institute for Navigation in the United Kingdom, “it takes two to Tango…. I think you have to attack the weakest of the pair, which is the commercial vessel.” Commandeering the GPS of the cargo ship to get it to veer off course could cause a collision, and it is a much easier hack.” (Humphreys, 2009)” (Nichols, R. R.K., et al., Unmanned Vehicle Systems & Operations on Air, Sea, Land, 2020)
The Case for a Cyber Weapon
“There appears to be valid evidence to support the theory that at least two of the US Navy Warships, USS John McCain and the USS Fitzgerald, AND/OR the commercial vessels involved, were on the wrong end of a cyberweapon and were receiving incorrect GPS-generated positional information. In agreement with Dr. Lust’s conclusions, the Cyber Weapon may have been deployed by an adversary’s [China PLAN] UAS off a small nearby vessel. The author believes that the subject Cyber-Weapon is an advanced modular entity that can spoof the GPS signals received by all vessels in its range. J.S. Warner & R.G. Johnson established in 2013 that the cybersecurity
of many common automated navigational systems today lacks basic cyber-attack protection; vessels using incorrect data will make wrong decisions in terms of navigation and emergency responses, leading to potential collisions and deaths (Warner & Johnson, 2013).” (Nichols R. K., et al., Unmanned Vehicle Systems & Operations on Air, Sea, Land, (2020))
Surfacing Questions
“Spoofing is the generation of false transmissions masquerading as P(Y) [the encrypted] Precise Signal that makes up the military vessel positioning basis or unencrypted C/A [Civilian Acquisition] code from GPS satellites. In a virtual world, tracking invalid data streams or non-integrity-based data is difficult, especially on three-dimensional vessels moving in time. However, there may be more than one method to spoof a signal, no matter how well it is encrypted. The cargo ships involved could have received unencrypted GPS ranging, a much less complex method than is required for military vessels. Neither ships need to be disabled and/or spoofed. All ships(military, commercial, recreational, and specialized service) in international waters require detailed positional information. GPS systems accurately supply a 3-D position, velocity, and time fix in all types of weather, 24 hours a day. GPS satellite signals are ranging devices that deliver two signals made up of a civilian carrier, C/A code, NAV message, P-Code, and a military carrier. (Nichols et al., Unmanned Aircraft Systems (UAS) in Cyber Domain: Protecting USA’s Advanced Air Assets, 2nd Edition, 2019)” Because of cost, most systems on commercial vessels have legacy GPS systems. In the author’s view, even if the GPS signals of the military vessels were not hacked, the unencrypted C/A – L1 Civilian signal may have been. It is also probable that this spoof is technically feasible on legacy systems. Experiments by Warner and Johnston out of Los Alamos and surveys by Schmidt et al. out of Queensland University clearly support the GPS/GNSS Cyberattack threat vector. (Warner, 2013) In 2013, Humphreys and his students successfully spoofed an $80MM Yacht’s GPS. (Humphreys, 2009)
What the physical damage indicates for the USS McCain and USS Fitzgerald is that both naval vessels appear to have collided on the starboard side. This leads to the theory that the civilian vessels involved in crossing or approaching the US Naval vessels relied on faulty information for their position. Further, the cyber weapon may have been delivered by a small UAS from a nearby fishing or recreational vessel. It would be a perfect delivery vehicle: stealth, quiet, low radar signature, requiring only 1- 25 watts of signal spoofing power. Since the true GPS signal strength reaching the surface of the Earth is about -160dBw (1x 10**-16 Watts), a 1-Watt GPS jamming spoof signal can override C/A code acquisition for more than 620 miles (Line of Sight (LOS) to the horizon.) (Warner, 2013) The starboard side collisions suggest that one of the vessels may have turned port or that the commercial ship tried to avoid a fake collision target received by turning starboard at the wrong time. The USS Fitzgerald report confirms this observation. These are huge vessels. Turning, stopping, or reversing course on a dime is not possible, especially by a large freighter. Decisions must be made well in advance of potential collision alerts. This is also why the delivery of a cyber weapon by UAS is so attractive. It would be a small bird in the glasses while attention was directed to the huge targets closing in on each other. In the chaos, the adversary wins.” (Nichols R. K., et al., Unmanned Vehicle Systems & Operations on Air, Sea, Land, (2020))
How could GPS chaos be achieved against US Vessels?
“The author believes that the spoofing GPS signal theory [targeting a commercial vessel by a cyber weapon to give it a false position and potentially cause a collision with itself or another vessel] is possible. It would require an enemy Unmanned Aircraft System (UAS) to be launched from either a sea-based vessel or a land-based intelligence station in the Spratly Islands. The methodology contemplated consists of three cyber-attack activities:
1) Breaking the existing AIS GPS commercial vessel receiver signal locks,
2) Locking the AIS GPS tracking device onto the GPS Simulator counterfeit signal,
3) Maintaining access by continued broadcasting of the fake GPS signal.” (Nichols R. K., et al., Unmanned Vehicle Systems & Operations on Air, Sea, Land, (2020))
So, the author ends the case for deadly spoofing in the South China Sea by an adversary.
How would you like to be in your living room, looking out your scenic window, when this visitor decides to dock in your backyard? See Figure 5-11. (veluvolu, 2025)

On May 22, 2025, the 135-meter feeder container ship NCL Salten plowed aground in Norway’s Trondheim fjord near Byneset at full speed around 5:30 a.m., stopping just 7 meters from a resident’s house. The sleeping homeowner was woken by a neighbor, finding the massive bow towering just outside his window. No one was injured, and there was no oil spill, but local landslides and structural damage caused significant alarm. (veluvolu, 2025)
Cyber Attacks on Navy Port Supply Operations
Hackers are increasingly targeting ports around the world. Cyber-attacks on the maritime industry’s operational technology (OT) systems have grown by at least 900% over the last 3 years, with some port operations being knocked out for days or even weeks, according to the maritime cybersecurity company Naval Dome. (Jandria Alexander, 2025)
Current cybersecurity measures at Navy-controlled and commercial ports tend to focus on identity and access management, dictating who has access to which systems. While that is critical, it is not enough. Nation-states like China and Russia are increasingly adept at bypassing identity and access controls in sensitive networks, such as with last year’s SolarWinds attack, which came through a routine software update to thousands of customers, including in parts of the Pentagon and other federal agencies. China is accused of an even more massive attack on the US government and business organizations this year, in which hackers exploited vulnerabilities in a Microsoft email service to plant hidden malware. (Jandria Alexander, 2025)
While such attacks have proven hard to prevent, the Navy can take specific steps to strengthen cybersecurity at Navy-controlled and commercial ports in the Pacific and elsewhere. Defending ports against sophisticated cyber-attacks calls for a multifaceted approach—one that combines traditional methods, such as redundancy and manual backups, with advanced technologies such as artificial intelligence (AI)-enabled threat detection. Such an approach focuses not just on protecting the IT and OT systems in ports from malware intrusion, but on keeping them resilient in the face of a successful breach. (Jandria Alexander, 2025)
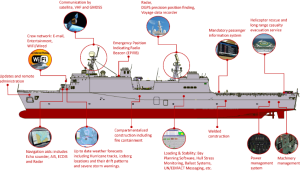
Cyber Vulnerabilities on a Ship
Figure 5-12 shows some of the cyber vulnerabilities on a ship. They revolve around the automation and networks controlling the ship’s operations. (Akpan & et.al., 2022) (Akpan & et.al., 2022) explores the systems available on ships that could be targeted by attackers, their possible vulnerabilities that an attacker could exploit, the consequences if the system is accessed, and actual incidents and potential mitigation actions. (Akpan & et.al., 2022)
A Cyber Vulnerability Assessment of the US Navy in the 21st Century
The CNO ordered a special report on the analysis of cyber vulnerabilities in the Navy. The report is dated, but it does give interesting factors on the anatomy of cyber-attacks and policy and controls necessary to mitigate the 30 million cyber intrusions logged in 2017. (Cruz, 2017)
Navigating the Intersection of Submarine and Cyber Warfare
A recent report discusses the cyber threats against US submarines. The interconnectedness of submarine and cyber warfare represents a pivotal development in modern military strategy. As underwater vessels evolve, so too must their defense mechanisms against an increasingly sophisticated landscape of cyber threats. (Editorial Team, 2024)
Submarines, once the silent predators of the deep, now face a dual challenge: leveraging cyber capabilities to enhance their operations while safeguarding against potential vulnerabilities that cyber warfare presents. Understanding this complex intersection is essential for maintaining maritime security in an era dominated by technology. (Editorial Team, 2024)
Expanding the Navigation Attacks on GNSS/GPS/AIS – a much bigger threat
GPS and AIS Spoofing have evolved in complexity, number of incidents, impact, and exploited vulnerabilities since our initial studies in 2017. The author spent time with the ASSURE44 project as a technical lead. Our concern was finding countermeasures for spoofing and navigation errors in aircraft. However, it was Kessler’s reference (Kessler & Shepard, 2022) that awakened the team to the magnitude of spoofing threats in the MTS against AIS and GPS systems.
It may have started back as early as the US entry into the Vietnam War with the Gulf of Tonkin Resolution, which authorized the US to initiate offensive military actions in Vietnam. (Wikipedia, 2025) Both the USS TURNER JOY and USS MADDOX reported being under attack based on radar images. USS TURNER JOY fired on the radar targets, and fighter aircraft were deployed from the USS TICONDEROGA. No visual confirmation was made on any of the targets. Declassified documents revealed that the ship’s radar was mimicking attack boats. (Paterson, 2008)
In June 2017, 20 vessels were spoofed in the Black Sea. The ATRIA, a 37,500-ton tanker, showed its ship 20 nm away at Gelendzhik Airport. Twenty ships’ CPA alarms sounded that their ships were ready for imminent collisions. (Weise, 2017) The ATRIA was part of a large-scale GNSS interference operation in Russian waters, placing ships at multiple airports, including Sochi, St. Petersburg, and Vladivostok. (Kessler & Shepard, 2022)
Since 2018, MARAD has made numerous reports of GNSS signal interference, signal loss, and reduced position accuracy in the Eastern Mediterranean Sea, affecting Cyprus and the coasts of Egypt, Israel, and Saudi Arabia. (MARAD, 2018-014)
GNSS spoofing was responsible for the seizure of the STENO IMPERIO in the Strait of Hormuz in July 2019 by Iran. (Starr, 2019)
In 2019, the 700-foot container ship MANUKAI was headed for her assigned berth in the Huangpu River. The AIS displayed another vessel moving at 7 knots in the same channel. Then, the other ship disappeared. The pattern repeated at lower speeds and then disappeared. The other vessel was confirmed never to leave its dock. All the MANUKAI GPS receivers failed, and an accurate fix was impossible. At least 300 incidents like this occurred around the Shanghai area. An analysis of data showed that daily spoofing attacks of the Huangpu MSA occurred and that the vessels indicated were in a circle. Smugglers were able to spoof AIS signals from legitimate vessels to escape detection by authorities. 23 collisions or allisions [3]. The Yangtze River in 2018 cost 53 lives. (Center for Advanced Defense Studies (C4ADS). , 2019)
Incidents of GPS and AIS spoofing with potential military conflict consequences. In 2021, two NATO warships- the U.K.’s HMD DEFENDER and the Dutch HNLMS EVERSTSEN arrived at the Ukrainian port of Odesa. GPS data showed them within spitting range (2 nm) of Russia’s Black Sea Fleet HQ. Naturally, the Russians were upset and scrambled their fleet. Real data showed that neither vessel left Odessa. (Harris, 2021)
GFW analyzed AIS data from 800 foreign fishing vessels from 2018 to 2021 and found 6,000 gaps in transmissions that lasted 24 hours, totaling 600,000 missing hours. Hiding fishing vessel locations masks illegal and unregulated fishing and drug or weapons activities. Chinese vessels accounted for 66% of the incidents. (Oceana, 2021)
The next question has to be how we prevent spoofing. There is a really potent answer known as ECD, which is covered in the next section.
ECD (Nichols R. K., 2022) [4] [5]
Definition: Spoofing – A Cyber-weapon attack that generates false signals to replace valid ones. GPS Spoofing is an attack to provide false information to GPS receivers by broadcasting counterfeit signals similar to the original GPS signal or by recording the original GPS signal captured somewhere else at some other time and then retransmitting the signal. The Spoofing attack causes GPS receivers to provide the wrong information about position and time. (Humphreys, 2008) (Tippenhauer, 2011) GPS Spoofed UAS / drones may deliver signals against any target ( CBRN assets included) that requires an accurate position fix or localization.
Ships depend heavily on GPS. They have few reference points to localize themselves apart from GPS. Wrong location indication can strand a ship, cause a collision, push off course into dangerous waters, ground a ship, or turn a ship into a ghost or a missile. Two thousand seventeen incidents in the Black Sea and South China Seas have been documented. (Burgess, 2017) (Nichols R. K., et al., 2019)
While planes and ships suffer spoofing attacks in the location domain, an attacker may also try to change the perceived time of a GPS receiver. Cellular networks rely on accurate time synchronization to exchange data packets between ground antennas and mobile handsets in the same network cell. Also, all neighboring network cells need to be time-synchronized for seamless call handoffs of handsets, switching cells, and coordinating data transmissions in overlapping coverage areas. Since most cellular ground stations get their timing information from GPS, a signal spoofing attacker could decouple cells from the common network time. Overlapping cells might send data simultaneously and frequencies, leading to message collisions and losses. (Anonymous, 2014) Failing communications networks can disrupt emergency services and businesses. (Eichelberger, 2019)
SPOOFING
Threats and weaknesses show that large damages (even fatal or catastrophic) can be caused by transmitting forged GPS signals. False signal generators may cost only a few hundred dollars in software and hardware.
A GPS receiver computing its location wrongly or even failing to estimate any location can have different causes. Wrong localization solutions come from 1) a low signal-to-noise ratio (SNR) of the signal (examples: inside a building or below trees in a canyon), 2) reflected signals in multipath scenarios, or 3) deliberately spoofed signals. (Eichelberger, 2019) discusses mitigating low SNR and multipath reflected signals. Signal spoofing (#3) is the most difficult case since the attacker can freely choose each satellite’s signal power and delay individually. (Eichelberger, 2019)
ECD
Dr. Manuel Eichelberger’s CD – Collective detection maximum likelihood localization approach, his method not only can detect spoofing attacks but also mitigate them! The ECD approach is a robust algorithm to mitigate spoofing. ECD can differentiate closer differences between the correct and spoofed locations than previously known approaches. (Eichelberger, 2019) COTS has a few spoofing-integrated defenses. Military receivers use symmetrically encrypted GPS signals, subject to a “replay” attack with a small delay to confuse receivers.
ECD solves even the toughest type of GPS spoofing attack, consisting of spoofed signals with power levels similar to authentic signals. (Eichelberger, 2019) The ECD approach uses only a few milliseconds’ worth of raw GPS signals, so-called snapshots, for each location fix. This enables the computation to be offloaded into the Cloud, allowing knowledge of observed attacks. Existing spoofing mitigation methods require a constant stream of GPS signals and tracking those signals over time. Computational load increases because fake signals must be detected, removed, or bypassed. (Eichelberger, 2019)
GPS SPOOFING RESEARCH: OUT OF THE BOX BRILLIANCE TO ECD DEFENSE
Three research tracks are most relevant to ECD / CD: Maximum Likelihood Localization, Spoofing Mitigation algorithms, and Successive Signal Interference Cancellation (SIC). Note that historical spoofing research focuses primarily on detecting singular SPS source attacks. The focus on mitigation, correction, and recovery, as well as attending to multiple spoofing signals on multiple satellite attack surfaces, is the hallmark of ECD.
Maximum Likelihood Localization
The CD is a maximum likelihood GPS localization technique. It was proposed in 1996, but considered computationally infeasible at that time. (Spilker, 1996)The CD was first implemented by Axelrad et al. in 2011. (Axelrod, 2011) The search space contained millions or more location hypotheses. Improvements in the computational burden were found using various heuristics. (Cheong, 2011) A breakthrough came with the proposal of a branch-and-bound algorithm that finds the optimal solution within ten seconds when running on a single CPU thread. (Bissig, 2017)
Spoofing Mitigation
GPS spoofing defenses have been intensively studied. Most of them focus on detecting spoofing attacks. There is a paucity of prior research on spoofing mitigation and recovering from successful attacks by finding and authenticating the correct signals. (M.L. Psiaki & Humphreys, 2016) In contrast to the extensive research on GPS spoofing, there is a lack of commercial, civil receivers with anti-spoofing capabilities. (Eichelberger, 2019) ECD inherently mitigates spoofing attacks.
Spoofing hardware performing a sophisticated, seamless satellite-lock takeover attack has been built. (Humphreys et al., 2008) Challenges associated with spoofing are matching the spoofed and accurate signals ‘ amplitudes at the receiver, which might not be in LOS and may be moving. (Schmidt & al, 2016) It is feasible for a spoofer to erase the authentic signals at a 180-degree phase offset. (M.L. Psiaki & Humphreys, 2016) This is one of the strongest attacks that can only be detected with multiple receiver antennas or a moving receiver. (M.L. Psiaki & Humphreys, 2016) The spoofer needs to know the receiver location more accurately than the GPS L1 wavelength, 19 cm, for signal erasure to be feasible. Receivers with only a single antenna cannot withstand such an erasure attack. ECD targets single-antenna receivers and does not deal with signal erasure. (Eichelberger, 2019) The original signals are still present in all other spoofing attacks, including signal replay and multiple transmission antenna implementations, and ECD remains robust. (Eichelberger, 2019) Detecting multi-antenna receivers and differentiating signal timing consistencies are covered (Tippenhauer, 2011)
The GPS anti-spoofing work most relevant to ECD is based on the joint processing of satellite signals and the maximum likelihood of localization. One method can mitigate a limited number of spoofed signals by vector tracking of all satellite signals. (Jafarnia-Jahromi, 2012) A similar technique is shown to be robust against jamming and signal replay. (Y. Ng & Gao, 2016)
Successive Signal Interference Cancellation
ECD uses an iterative signal-damping technique with spoofing signals similar to SIC. SIC removes the strongest received signals to find the weaker signals and has been used with GPS signals before. (Lopez-Risueno & Seco-Granados, 2005) That work is based on a classical receiver architecture, which only keeps a signal’s timing, amplitude, and phase. The ECD has a snapshot receiver based on CD, which directly operates in the localization domain and does not identify individual signals in an intermediate stage. It is impossible to differentiate between authentic and spoofed signals; a priori, ECD does not remove signals from the sample data. Otherwise, the localization algorithm might lose the information from authentic signals/ Instead, ECD dampens strong signals by 60% to reveal weaker signals. This can reveal localization solutions with lower CD likelihood. (Eichelberger, 2019)
GPS Signal Jamming
The easiest way to prevent a receiver from finding a GPS location is by jamming the GPS frequency band. GPS signals are weak and require sophisticated processing to be found. Satellite signal jamming considerably worsens the signal-to-noise ratio (SNR) of satellite signal acquisition results. ECD algorithms achieve a better SNR than classical receivers and tolerate more noise or stronger jamming. (Eichelberger, 2019)
A jammed receiver is less likely to detect spoofing since the original signals cannot be accurately determined. The receiver tries to acquire any satellite signals it can find. The attacker only needs to send a set of valid GPS satellite signals that are stronger than the noise floor without synchronizing with authentic signals. (Eichelberger, 2019)
There is a more powerful and subtle attack on top of the jammed signal. The spoofer can send a set of satellite signals with adjusted power levels and synchronize them with authentic signals to spoof the receiver successfully. Even if the receiver has countermeasures to differentiate the jamming, the spoofer signals will be accepted as authentic. (Nichols R., Chapter 14 Maritime Cybersecurity, 2020)
Two Robust GPS Signal Spoofing Attacks and ECD
Two of the most powerful GPS signal spoofing attacks are Seamless Satellite-Lock Takeover (SSLT) and Navigation Data Modification (NDM). How does ECD perform against these?
Seamless Satellite-Lock Takeover (SSLT)
The most powerful attack is a seamless satellite-lock takeover. The original and counterfeit signals are nearly identical in such an attack concerning the satellite code, navigation data, code phase, transmission frequency, and received power. This requires the attacker to know the location of the spoofed device precisely so that ToF and power losses over a distance can be factored in. After matching the spoofed signals with the authentic ones, the spoofer can send its signals with a small power advantage to trick the receiver into tracking those instead of the authentic signals. A classical receiver without spoofing countermeasures, like tracking multiple peaks, cannot mitigate or detect the SSLT attack, and there is no indication of interruption of the receiver’s signal tracking. (Eichelberger, 2019)
Navigation Data Modification (NDM)
An attacker has two attack vectors: modifying the signal’s code phase or altering the navigation data—the former changes the signal arrival time measurements. The latter affects the perceived satellite locations. Both influence the calculated receiver location. ECD works with snapshot GPS receivers and is not vulnerable to NDM changes, as they fetch information from other sources like the Internet. ECD deals with modified, wireless GPS signals. (Eichelberger, 2019)
A more detailed discussion of ECD is found in (Nichols R. K., Chapter 14 Maritime Cybersecurity, 2020), (Eichelberger, 2019), and (Nichols R. K., et al., Unmanned Vehicle Systems & Operations on Air, Sea, Land, 2020). Suffice it to say that it represents a very strong countermeasure against the spoofing of aircraft and ships.
NEED FOR NEW CYBER DEFENSE ARCHITECTURE
Since we began to adopt digital-based technologies with the use of the Internet and web, we are spending more of our time and, more importantly, doing more of our operations using digital or cyber. These technologies bring more efficiency, but at the same time, this has given rise to various kinds of cyber risks and security issues. Cybercrime is on the path to becoming a huge USD 13 trillion problem by 2025 unless something is changed. (Morgan, 2023) The Maritime industry is not immune to all this. There are many systems in use in a ship as seen in Figure 5-12 (Akpan & et.al., 2022), and many of them depend on digital or cyber as the basis of their design and communication. Some of the key areas are – (Akpan & et.al., 2022)
- Satellite communication and navigation
- Crew and/or guest network and email systems
- Passenger information system
- Evacuation
- Machinery management
- Power management
- Weather forecasting
All of the above systems are important to Maritime operations. Most of the operations are based on digital or cyber technologies. Hence, it is important that, in order for maritime operations to run correctly and safely, digital and cyber operations run well. However, the current Cyber architecture is too prone to cyberattacks. We must think of new ways of doing things. While people and operations get hurt in our daily cyber interactions, these cyberattacks can really hurt Maritime and the industry.
WOPLLI® Technologies [6] has realized the problem and, as of 2022, created a program at IEEE on Cyber Security for Next Generation Connectivity Systems. (IEEE, 2025) The program has determined the following three areas as the primary causes behind cybersecurity problems. (Malhotra, 2025)
- The information on all of us and our systems is in many systems or databases. This information ends up as the primary target or honeypot for hackers. In a wider context, a person’s information exists in 100+ databases, and these databases work to increase the depth of the information or create a more holistic profile & identity.
- The same databases or the companies owning those databases end up sharing or selling the information further to other organizations, and hence create a more widespread problem.
- As a person or a system, there is no way to determine who and with what we are interacting. (IEEE, 2025)
In 2021, WOPLLI ® Technologies proposed five architecture principles that have also become the basis of the IEEE program ‘Cyber Security for Next Generation Connectivity Systems’. These principles may form the basis of the new architecture. We already see a lot of movement. (IEEE, 2025) (Malhotra, 2025)
- Control in data flow for the person or the originator
- Decentralized identity
- Distributed computing
- Heterogeneous controls and their application
- Self-Healing systems
We will now consider each of these principles in detail and correlate them with the Maritime.
Control in data flow for the person or the originator implies that the originator or person has control of where their data will go and how it will be processed. Before interaction between systems, each side must be able to determine if it is a trustworthy entity with which to interact. Plus, as the data goes into other systems, a person or the originator could pull it back or make it unusable if it fails to meet the person’s or system’s criteria or consent. In Maritime systems, every IoT device, communication device, and or person interacts with others to make communication happen. If the rules of data communication between various parties are established such that boundaries are realized, and if the data happens to travel outside a certain boundary, it could be made unusable; hence, reducing hackers’ ability to get hold of data. An example is a ship’s communication/signaling, where the crew may communicate some important information about port schedules, cargo, etc. If the pirates try to get hold of these signals, they would be in the wrong hands, and hence, the data would become unusable.
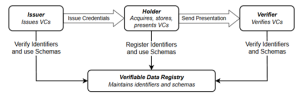
Decentralized identity implies that the three parties in an identity system (issuer, holder, and verifier) are separate and independent from each other. Today, most identity methods are centralized or federated, where two or all three of the parties in an identity system are the same. Everything has an identity in digital systems. Concepts of decentralized Identity have been progressing in various Linux Foundation projects (like Trust over IP Foundation, Decentralized Identity Foundation), and associated concepts such as Verifiable Credentials have been standardized by W3C (World Wide Web Consortium). (W3C, 2025) The consequent Trust Triangle, where a verifier can verify the credentials held in a wallet without having direct connection with the issuer, is progress for the digital industry and web space, with which the identity of a counterparty can be verified by the verifier, without having direct contact (or shared database) with the issuer. In Maritime, these methods can be applied in various systems to remove the vulnerability and risk of breach of centralized systems holding important data to enable that transaction. Along with this, the decentralized identity method can help determine the authenticity of the holder’s verifiable credentials. Examples of applications of decentralized identity methods in the maritime industry could include systems used in communication, ticketing, supply chain, etc.
Distributed computing implies that instead of data being in one place (i.e., large databases, etc.), it is spread out but still able to communicate & interact with the other data, implying distributed computing. In modern architecture, we should not have all assets in a single place, as in medieval times, where high walls and moats were built to protect an asset that was inside the fort. Instead, our architecture should spread out the asset (the data) in different places, which can still work together to bring the system or service together. Still, it cannot be found in a single place when hackers (attackers in medieval times) come looking for it.
Today’s systems work with controls, such as security controls applied to them. Often, when a system fails, i.e., goes down or leaks information, it is due to control failure. Heterogeneous controls imply that controls (if they are programmed) are not sourced from the same place, but rather, there is a failsafe and alternative controls available, possibly from other sources. The failure of a single control system should not lead to the failure of a system.
Self-healing systems imply that when distributed nodes/entities exist and can independently compute and connect, they can form a network based on different criteria, other than the shortest path first. One of the criteria could be the security or the integrity of the next hop. (IEEE, 2025)
Conclusions
In maritime, we should investigate the application of these principles to secure systems. As has been noted, spoofing systems or signals such as the Global Positioning System can be devastating. It can lead to ships veering off their course, crashing, or worse, landing in enemy/pirate territory. A GPS built with methods that can self-heal if the signal is found to be non-authentic (i.e., spoofed) is desirable.
References
Adelaide Students Project. (2025). Attack Sophistication vs Intruder Knowledge. Retrieved from https://www.eleceng.adelaide.edu.au/students/: https://www.eleceng.adelaide.edu.au/students/wiki/projects/images/c/cd/Fig2.png
Akpan, F., & et.al. (2022). Ship Vulnerabilities (renumbered from Figure 1. Automation systems for modern and autonomous ships. Network (pp. 2(1), 123-138; ). https://doi.org/10.3390/network2010009. Retrieved from etwork 2022, 2(1), 123-138; https://doi.org/10.3390/network2010009: https://www.mdpi.com/2673-8732/2/1/9
AMAZON. (2025). Best-Sellers-Kindle-Store-Network-Security/. Retrieved from https://www.amazon.com/: https://www.amazon.com/Best-Sellers-Kindle-Store-Network-Security/zgbs/digital-text/16977293011/ref=zg_bs_pg_2_digital-text?_encoding=UTF8&pg=2
Anonymous. (2025, May 30). World Map of Major Ports. Retrieved from https://3.bp.blogspot.com/: https://3.bp.blogspot.com/-RD2JFkxg2gk/Td-VKr6vgXI/AAAAAAAAACA/m0T6KvtOpM8/s1600/world-sea-ports.jpg
Anonymous. (2014). Timing & Synchronization for LTE-TDD & LTE-Advanced Mobile Networks; Technical Report, Microsemi. Retrieved from Anonymous. (2014). Timing & Synchronization for LTE-TDD & LTE- Advanced Mobile Networkhttps://www.microsemi.com/: https://www.microsemi.com/ document-portal/doc_download/133615-timing-sync-for-lte-tdd-lte-a-mobile-networks
AP / Politico. (2025, May 18). why-did-a-a-mexican-tall-ship-smack-into-the-brooklyn-bridge-00356342. Retrieved from https://www.politico.com/news/: https://www.politico.com/news/2025/05/18/why-did-a-a-mexican-tall-ship-smack-into-the-brooklyn-bridge-00356342
ASSURE 44 Research University Teams. (2023). A11L.UAS.86 – A44 Mitigating GPS and ADS-B Risks for UAS Task 5 Final Report. Washington, DC: US Department of Transportation (Unclassified).
Axelrod, P. &. (2011). Collective Detection and Direct Positioning Using Multiple GNSS Satellites. Navigation, (pp. 58(4): 305-321.).
Bissig, P. &. (2017). Fast & Robust GPS Fix using 1 millisecond of data. 16 ACM / IEEE Int Conf on Information Processing in Sensor Networks (pp. 223-234). Pittsburgh, PA: IPSN.
Burgess, M. (2017, 9 21). When a Tanker Vanishes, all evidence points to Russia. Retrieved from https://www.wired.co.uk/: https://www.wired.co.uk/article/ black-sea-ship-hacking-russia: https://www.wired.co.uk/: https://www.wired.co.uk/article/ black-sea-ship-hacking-russia
carnegieendowment.org/. (2024, December). baltic-sea-internet-cable-cut-europe-nato-security?lang=en. Retrieved from https://carnegieendowment.org/: https://carnegieendowment.org/emissary/2024/12/baltic-sea-internet-cable-cut-europe-nato-security?lang=en
CBF. (2025, June 28). Chesapeake Bay Foundation. Retrieved from https://www.cbf.org/: https://www.cbf.org/about-the-bay/bay-facts.html
CBS NEWS.(2025, February 20). illegal-crossings-u-s-mexico-border-down-94-percent-border-patrol-chief-says/. Retrieved from https://www.cbsnews.com/news/: https://www.cbsnews.com/news/illegal-crossings-u-s-mexico-border-down-94-percent-border-patrol-chief-says/
Center for Advanced Defense Studies (C4ADS). (2019, 12 2). Shanghai GPS Spoofing. Retrieved from https://drive.google.com: https://drive.google.com/file/d/1dTWu7H9JjRyN0uQPZ9HwiUzCFd7cd5pL
Cheong, J. &. (2011). Efficient Implementation of Collective Action. In the IGNSS Symposium (pp. 15-17).
CISA. (2020, March 24). CISA. Retrieved from Critical Infrastructure Sectors -DHS: https://www.cisa.gov/critical-infrastructure-sectors
Cruz, T. H. (2017). cyber-vulnerability-assessment-u-s-navy-21st-century/. Retrieved from https://cimsec.org/: https://cimsec.org/cyber-vulnerability-assessment-u-s-navy-21st-century/
Department of Homeland Security. (2025, May 28). Retrieved from How big is Homeland Security: https://duckduckgo.com/?q=how+big+is+homeland+security&atb=v441-1&ia=web
DIA. (2025). 2025_dia_statement_for_the_record. Retrieved from https://armedservices.house.gov/: https://armedservices.house.gov/uploadedfiles/2025_dia_statement_for_the_record.pdf
DOE. (2025). national-scada-test-bed. Retrieved from https://www.energy.gov/: https://www.energy.gov/oe/national-scada-test-bed
Editorial Team. (2024, 7 11). submarine-and-cyber-warfare/. Retrieved from https://totalmilitaryinsight.com/: https://totalmilitaryinsight.com/submarine-and-cyber-warfare/
Eichelberger, M. (2019). Robust Global Localization using GPS and Aircraft Signals. Zurich, Switzerland: Free Space Publishing, DISS. ETH No 26089.
GOOGLE. (2025, June 28). Dimensions of the Chesapeake Bay. Retrieved from google.com: www.google.com
Hackernet group news. (2025). Cyber tools by category. Retrieved from www.linkedin.com: www..linkedin.com
Harman, T. (2003). Lee’s Real Plan at Gettysburg. Mechanicsburg, PA: Stackpole Books.
Harris, M. (2021, 7 29). Phantom Warships Are Courting Chaos in Conflict Zones. WIRED.. Retrieved from https://www.wired.com/story/: https://www.wired.com/story/fake-warships-ais-signals-russia-crimea/
https://free-printablemap.com/wp-content/uploads/2018/10/inland-waterways-of-the-united-states-wikipedia-with-navigable-waters-of-the-united-states-map.png. (2018, October). Retrieved from https://free-printablemap.com/: https://free-printablemap.com/wp-content/uploads/2018/10/inland-waterways-of-the-united-states-wikipedia-with-navigable-waters-of-the-united-states-map.png
Humphreys, T. &. (2008). Assessing the spoofing threat: Development of a portable GPS civilian spoofer. In Radionavigation Laboratory Conf. Proc.
ICyber Press. (2025). OWASP Top 10 Vulnerabilities. Retrieved from www.linkedin.com: www.linkedin.com
IEEE. (2025). cyber-security-for-next-generation-connectivity-systems/. Retrieved from https://standards.ieee.org/: https://standards.ieee.org/industry-connections/activities/cyber-security-for-next-generation-connectivity-systems/
INFOSEC and INFOWAR Protection of Information Assets and Systems. (2021). ACO CYB 680 / 681 Fall Semester. KSU.
Intermodal-Service-Map. (2017, Aug). Retrieved from https://www.englandlogistics.com/: https://www.englandlogistics.com/wp-content/uploads/2017/08/Intermodal-Service-Map.jpg
Jafarnia-Jahromi, A. (2012). Detection and mitigation of spoofing attacks on a vector-based tracking GPS receiver. ION ITM. , (p. ).
Jandria Alexander, M. G. (2025, June 17). cyberattacks-on-navy-port-supply-operations. Retrieved from https://www.boozallen.com/markets/defense/indo-pacific/: https://www.boozallen.com/markets/defense/indo-pacific/cyberattacks-on-navy-port-supply-operations.html
Jean-Paul-Rodrigue. (retrieved 2025, May). Major-maritime-shipping-routes-and-strategic-passages. Retrieved from https://www.researchgate.net/: https://www.researchgate.net/profile/Jean-Paul-Rodrigue/publication/315398501/figure/fig1/AS:599262685573122@1519886766175/Major-maritime-shipping-routes-and-strategic-passages.png
Julie J. C. H. Ryan, & Ryan, &. D. (2005). Proportional Hazards in Information Security. Retrieved from https://onlinelibrary.wiley.com/: https://onlinelibrary.wiley.com/doi/10.1111/j.0272-4332.2005.00573.x
Kessler, G. C., & Sheppard, &. S. (2020). Maritime Cybersecurity: A Guide to Leaders and Managers. Middletown, DE: Independently Published.
Kessler, G., & Shepard, &. S. (2022). Maritime Cybersecurity: A Guide for Leaders and Managers, 2nd Edition. Middletown, DE: Independently Published.
LINKEDIN. (2025). Cybersecurity Search Engines. Retrieved from www.linkedin.com: www.Linkedin.com
LINKEDIN. (2025). Fake Videos. Retrieved from www.linkedin.com: www.linkedin.com
LINKEDIN. (2025). List of Digital Forensic Tools in Cybersecurity. Retrieved from www.linkedin.com: www.linkedin.com
LINKEDIN. (2025). OT/ ICS Cyber Cheat Sheet. Retrieved from www.linkedin.com: www.linkedin.com
LINKEDIN. (2025). Types of Cyber Attacks. Retrieved from www.linkedin.com: www.linkedin.com
LINKEDIN Feed: 21 Dark Web Tools. (2025). Retrieved from www.linkedln.com/feed: www.linkedln.com/feed
LINKEDIN Feed: Advanced Hackers Kit. (2025). Retrieved from www.linkedln.com/: www.linkedln.com/
LINKEDIN Feed: Cybersecurity Domains. (2025). Retrieved from https://www.linkedin.com/feed/: https://www.linkedin.com/feed/
LINKEDIN feed: Top 100 forensics tools. (2025). Retrieved from www.linkedln.com: www.linkedln.com/feed
LINKEDIN feed: Top 8 Cyber Attacks. (2025). Retrieved from LinkedIn Feed: www.linkedln.com/feed: www.linkedln.com/feed
López-Risueno & Seco-Granados, G. (2005). Cn/sub 0/ estimation and near-far mitigation for GNSS indoor receivers. In 2005 IEEE 61st Vehicular Technology Conf, (pp. V4: 2624-2628).
M.L. Psiaki & Humphreys, T. (2016). GNSS Spoofing and Detection. Proc. of the IEEE, (pp. 104(6): 1258-1270.).
Malhotra, V. (2025, June 26). programs at WOPLLI® Technologies . Retrieved from https://www.woplli.com/programs: https://www.woplli.com/programs
MARAD. (2018-014, November 8). Eastern Mediterranean Sea-GPS Interference, MSCI Advisory 2018-014. Retrieved from https://www.maritime.dot.gov/content/: https://www.maritime.dot.gov/content/2018-014-eastern-mediterranean-sea-gps-interference
Morgan, S. (2023, November 13). cybercrime-damage-costs-10-trillion-by-2025/. Retrieved from https://cybersecurityventures.com/: https://cybersecurityventures.com/cybercrime-damage-costs-10-trillion-by-2025/
Nichols, & Carter, D. D. (2023). CYBER-HUMAN SYSTEMS, SPACE TECHNOLOGIES AND THREATS. Manhattan, KS: New Prairie Press #TBN.
Nichols, & R. K., A. E. (2024). Advanced Technologies for Humanity. Manhattan, KS: New Prairie Press.
Nichols, R. &.-2. (2020). Counter Unmanned Aircraft Systems Technologies and Operations. Manhattan, KS: https://www.newprairiepress.org/ebooks/31/.
Nichols, R. -2. (2022). Drone Delivery of CBNRECy DEW Weapons: Emerging Threats of Mini-Weapons of Mass Destruction and Disruption. (WMDD). Manhattan, KS: https://newprairiepress.org/ebooks/46/.
Nichols, R. (2020). Chapter 14 Maritime Cybersecurity. In R. K. Nichols, & et.al, Unmanned Vehicle Systems & Operations on Air, Sea, Land. Manhattan, KS: NPP Press: https://www.newprairiepress.org/ebooks/35/.
Nichols, R. (2023). COT 684 Fusion Report Self-healing GPS Navigation Signals that have been Jammed, Spoofed, or otherwise Degraded. Salina, KS: KSU .
Nichols, R. (2023). Kaltura_Capture_recording_-_RN – A-D Analysis -1 (2023_02_06 15_36_17 UTC).mp4″. Retrieved from “C:\Users\profr\OneDrive\Documents\COT 680-CYBR 680 CYBER SYSTEMS AND RISK MANAGEMENT SPRING 2023 – 15799\Kaltura_Capture_recording_-_RN – A-D Analysis -1 (2023_02_06 15_36_17 UTC).mp4”: “C:\Users\profr\OneDrive\Documents\COT 680-CYBR 680 CYBER SYSTEMS AND RISK MANAGEMENT SPRING 2023 – 15799\Kaltura_Capture_recording_-_RN – A-D Analysis -1 (2023_02_06 15_36_17 UTC).mp4”
Nichols, R. (2023). Ryan Nichols Qualitative Information Risk Assessment. Class Presentation. KSU.
Nichols, R. -3. (2021). Disruptive Technologies with Applications in Airline, Marine, and Defense Industries (2021). Manhattan, KS: https://newprairiepress.org/ebooks/38/.
Nichols, R. K. (2022). DRONE DELIVERY OF CBNRECy – DEW WEAPONS Emerging Threats of Mini-Weapons of Mass Destruction and Disruption ( WMDD). Manhattan, KS: https://newprairiepress.org/ebooks/46/.
Nichols, R. K. (2022). SUAS/UAS Cyber terror implications/ Cyber Navigation Threats/Chinese UAS Intelligence/Capabilities and Impending invasion of Taiwan. CSR Symposium Keynote, UND. KSU.
Nichols, R. K., Carter, C. M., Drew, J. V., Farcot, M., Hood, J.-P., Jackson, M. J., . . . Ryan. (2023). Cyber-Human Systems, Space Technologies, and Threats. Manhattan, KS: New Prairie Press #52.
Nichols, R. K., Carter, C. M., Drew, J. V., Farcot, M., Hood, J.-P., Jackson, M. J., . . . Ryan. (2023). Cyber-Human Systems, Space Technologies, and Threats”. Manhattan, KS: NPP eBooks. 52.
Nichols, R. K., Carter, C. M., Hood, J.-P., Jackson, M. J., Joseph, S. M., Larson, H., . . . S. (2022). Space Systems: Emerging Technologies and Operations (2022). Manhattan, KS: https://newprairiepress.org/ebooks/47/.
Nichols, R. K., Carter, C. M., Hood, J.-P., Jackson, M. J., Joseph, S. M., Larson, H., . . . Sincavage. (2022). Space Systems: Emerging Technologies and Operations. Manhattan, KS: New Prairie Press #47.
Nichols, R. K., Mumm, H. C., Lonstein, W. D., Ryan, J. J., Carter, C. M., Hood, J.-P., . . . and Jackson, M. J. (2020).Unmanned Vehicle Systems & Operations on Air, Sea, Land. Manhattan, KS: NPP eBooks. 35.
Nichols, R. K., Mumm, H. C., Lonstein, W. D., Ryan, J. J., Carter, C. M., Hood, J.-P., . . . and Jackson, M. J. (2020). Unmanned Vehicle Systems & Operations on Air, Sea, Land. Retrieved from https://newprairiepress.org/ebooks/35/: https://newprairiepress.org/ebooks/35/
Nichols, R. K., Mumm, H. C., Lonstein, W. D., Ryan, J. J., Carter, C., & Hood, J.-P. (2019). Unmanned Aircraft Systems in the Cyber Domain. Manhattan, KS: NPP eBooks. 27.
Nichols, R. K., Mumm, H. C., Lonstein, W., Sincavage, S., Carter, C. M., Hood, J.-P., . . . and Shields, B. (2021). Disruptive Technologies with Applications in Airline, Marine, and Defense Industries (2021). Retrieved from https://newprairiepress.org/ebooks/38/: https://newprairiepress.org/ebooks/38/
Nichols, R. K., Sincavage, S., Mumm, H., Lonstein, W., Carter, C., Hood, J. P., . . . and Harding, T. (2022). Drone Delivery of CBNRECy DEW Weapons: Emerging Threats of Mini-Weapons. Retrieved from https://newprairiepress.org/ebooks/46/: https://newprairiepress.org/ebooks/46/
Nichols, R., et al. (2024). Advanced Technologies for Humanity. Retrieved from https://www.amazon.com/: https://www.amazon.com/dp/B0DBK9ZMPV
Nichols, R., & Carter, D. D. (2023). CHAPTER 10: SPACE ELECTRONIC WARFARE (NICHOLS). In R. Nichols, & e. al., Cyber Human Systems, Space Operations and Threats. Manhattan, KS: NPP Accepted for publication Fall 2023.
Nichols, R., et al. (2024). Advanced Technologies for Humanity. Carlisle, PA: Amazon.
Nichols, R., & Ryan, D. &. (2000). Defending Your Digital Assets Against Hackers, Crackers, Spies, and Thieves. Washington, DC: McGraw-Hill.
Nichols, R., Carter, C., Diebold, C., Drew, J., Farcot, M., Jackson, M., . . . & Toebes, J. (2023). Space Electronic Warfare. In R. Nichols, CYBER HUMAN SYSTEMS, SPACE TECHNOLOGIES AND THREATS (p. Chapter 10). Manhattan: New Prairie Press. Accepted for Publication, 2023; NPP#TBN.
Nichols, R., Diebold, M. C., & Johnson, &. P. (2024). Risk Analysis of submarine cables in the Western Pacific. Manhattan, KS: KSU.
Nichols, R., Sincavage, S., Hood, J., Carter, C., & Mumm, H. (2022). Space Systems: Emerging Technologies and Operations. Manhattan: New Prairie Press.
Nichols-2, R. K., Carter, C. M., Hood, J.-P., Jackson, M. J., Joseph, S. M., Larson, H., . . . Sincavage. (2022). Chapter 2. Satellite Killers and Hypersonic Drones. In W. Slofer, Space Systems: Emerging Technologies and Operations. Manhattan, KS: New Prairie Press #47.
NPR. (2024, December 31). finland-russia-severed-undersea-cable-shadow-fleet. Retrieved from https://www.npr.org/: https://www.npr.org/2024/12/31/nx-s1-5243302/finland-russia-severed-undersea-cable-shadow-fleet
Oceana. (2021, 4). Now You See Me, Now You Don’t: Vanishing Vessels Along Argentina’s Waters. Retrieved from https://usa.oceana.org/: https://usa.oceana.org/wp-content/uploads/sites/4/2021/06/oceana_argentina_mini_report_finalupdated.pdf, DOI: 10.5281/zenodo 4893397
Parker, D. B. (1998). Parker Hexad. Retrieved from https://en.wikipedia.org/wiki/Parkerian_Hexad: https://en.wikipedia.org/wiki/Parkerian_Hexad
Paterson, P. (2008, February). The Truth About Tonkin. Naval History Magazine, 22(1). Retrieved from https://www.usni.org/magazines/naval-history-magazine/: https://www.usni.org/magazines/naval-history-magazine/2008/february/truth-about-tonkin
Peerenboom J, F. R. (2001). Recovering from disruptions of critical independent infrastructures. Presented at the CRIS/DRM/IIT/NSF Workshop on Mitigating the Vulnerability of Critical Infrastructures to Catastrophic Failure, Washington. Sep. Retrieved from https://nap.nationalacademies.org/: https://nap.nationalacademies.org/read/18671/chapter/19#130
R.K..Nichols, Johnson, P., & Diebold, M. C. (2024). Risk Analysis in many forms: An analysis of submarine cables in the Western Pacific. Manhattan: KSU.
R.K.Nichols. (n.d.). CRYPTO-WIZ FOUR WINNS RECREATIONAL CRUISER. Picture (iPhone). Rhodes River, MD.
Ryan, J., & & Ryan, D. J. (2006). https://www.academia.edu/20525921/Expected_benefits_of_information_security_investments. Computer and Security, p. https://www.academia.edu/20525921/Expected_benefits_of_information_security_investments. Retrieved from https://www.academia.edu/20525921/: https://www.academia.edu/20525921/Expected_benefits_of_information_security_investments
SIEM Alerts List Group. (2025). SIEM SOC Checklist. Retrieved from www.linkedin: Www.linkedin.com
Spilker, J. (1996). Fundamentals of Signal Tracking Theory. Prog in Astronautics & Aeronautics, (pp. 163:245-328).
Starr, B. B. (2019, 7 19). Iran Announces Capture of British-Flagged Oil Tanker; US Officials Say Two Ships Seized. CNN.. Retrieved from https://www.cnn.com/2: https://www.cnn.com/2019/07/19/middleeast/british-tanker-seized-iran-intl/
Statista. (2024, June 21). Recreational vessels in the US 1980-2023. Retrieved from https://www.statista.com: https://www.statista.com
STDL. (2025). swiss-territorial-data-lab-stdl_gnss-spoofing-activity. Retrieved from https://www.linkedin.com/: https://www.linkedin.com/posts/swiss-territorial-data-lab-stdl_gnss-spoofing-activity-7335164866665607168-0zl7/
TAIPEI Times. (2025, January 1). Chinese ship cuts cable near Keelung Harbor. Retrieved from https://www.taipeitimes.com/: https://www.taipeitimes.com/News/taiwan/archives/2025/01/05/2003829674
Techsecure. (2025). Figure 5-10 ISO 27001 ISMS Security Architecture Diagram. Retrieved from https://imgur.com/YI6x3ac: https://imgur.com/YI6x3ac
Tippenhauer, N. &. (2011). On the requirements for successful spoofing attacks. Proc. of the 18th ACM Conf. on Computing and Communications Security (pp. 75-86). (CCS).
UNCTAD. (2019 (updated )). United Nations. (2019). Fact Sheet #15: Maritime Transport Indicators. U.N. Conference on Trade and Development (UNCTAD). Retrieved from https://unctad.org/: https://unctad.org/en/PublicationChapters/tdstat44_FS13_en.pdf
USCG. (2024, October). ohss_uscg-maritime-response-activities-report-FY20-23. Retrieved from https://ohss.dhs.gov/sites/: https://ohss.dhs.gov/sites/default/files/2024-10/2024-1011_ohss_uscg-maritime-response-activities-report-FY20-23.pdf
veluvolu, m. (2025, May 22). when-a-ship-crashed-into-a-norwegian-backyard-activity. Retrieved from https://www.linkedin.com/posts/madan-veluvolu: https://www.linkedin.com/posts/madan-veluvolu-039b6b24_when-a-ship-crashed-into-a-norwegian-backyard-activity-7339166691836293120-IHbh?rcm=ACoAABNxO7oBGEAklz43cCOcv19xU0vrwUxTvN8
W3C. (2025). https://www.w3.org/TR/vc-data-model-2.0/. Retrieved from https://www.w3.org/: https://www.w3.org/TR/vc-data-model-2.0/
Weise, E. (2017, September 26). Mysterious GPS Glitch Telling Ships They’re Parked at Airport May Be an Anti-Drone Measure. USA TODAY. Retrieved from https://www.usatoday.com/story/tech/news/7: https://www.usatoday.com/story/tech/news/2017/09/26/gps-spoofing-makes-ships-russian-waters-think-theyre-land/703476001/
Wikipedia. (2025). A joint resolution “To promote the maintenance of international peace and security in Southeast Asia.”. Retrieved from https://en.wikipedia.org/wiki/: https://en.wikipedia.org/wiki/Gulf_of_Tonkin_Resolution
Wikipedia. (2025). Notice to Mariners. Retrieved from https://en.wikipedia.org/: https://en.wikipedia.org/wiki/Notice_to_mariners
Wing, C. (2006, August 29). One-Minute-Nautical-United-States-Squadrons/. Retrieved from https://www.amazon.com/: https://www.amazon.com/One-Minute-Nautical-United-States-Squadrons/dp/0071479236
- Ng & Gao, G. (2016). Mitigating jamming & meaconing attacks using direct GPS positioning. In Position, Location & Navigation Symposium (PLANS) IEEE/ION, (pp. 1021-1026).
Endnotes
[1] Linked Figures 5-2 to 5-10 were run through TinEye Reverse Engine (Tineye.com) to determine the first occurrence. It was not assumed that the poster made an appropriate citation or that LINKEDIN ran its standard policy-required checks for plagiarism. Letters /emails to the original poster or group were sent requesting/confirming the relevant citations. Under our Book 11 Disclaimer, the information supplied is generally believed to be accurate, and additional citation verifications were made. Any errors will be addressed upon formal notification by the managing editor via changes to Pressbooks and an ERRATA sheet.
[2] This response means that the Skipper / XO / COB and at least five (5) watch sailors on
each Naval vessel (roughly 40 – 50 personnel, including bridge staff, plus 130 lookouts on the USS McCain because of ordered watch conditions) have been judged incompetent (Navy Information Office, 2017). Their careers are over, and some will face court-martial and possibly brig time.
[3] A collision occurs when two moving vessels strike each other, while an allision occurs when a moving vessel strikes a stationary object such as a bridge abutment, a vessel made fast, or a dock.
[4]The author has nicknamed it ECD to honor. Manuel Eichelberger’s brilliant doctoral research, ECD, is Dr. Manuel Eichelberger’s advanced implementation of CD to detect and mitigate spoofing attacks on GPS or ADS-B signals
[5]The detailed ECD Navigation model and supporting equations are found in the primary reference (Eichelberger, Robust Global Localization using GPS and Aircraft Signals, 2019)
[6] Full Disclosure: Co-author Vikas Malhotra is the founder and director of WOPLLI® Technologies. No business solicitation is intended, nor is direct/indirect support received from WOPLLI® Technologies. Opinions of the co-author are strictly his own and do not represent IEEE, W3C, or KSU proper.
