7 Connected, Complex, Compromised (Murthy & Ghaffari)
Abbreviations
AIS – Automated Identification System
ARPA – Automatic Radar Plotting Aid
ATIS – Automatic Transmitter Identification System
DSC – Digital selective calling
ECDIS – Electronic chart display and information system
EDR – Endpoint Detection and Response
EGC – Enhanced Group Call
EPIRB – Emergency positioning indicator and response beacon equipment
GMDSS – Global Maritime Distress and Safety System
GPS – Global Positioning System
HF – High frequency 3 – 30 MHz
HMI – Human machine interfaces
IBS – Integrated Bridge Systems
ICS – Internal Communication Systems
ICT – Information and Communication Technology
IMO SOLAS – International Maritime Convention for Safety of Life at Sea
ITU – International Telecommunication Union
LF – Low frequency < 300 HZ for sound, 30-300 kHz for radio, and 1Hz to 100 kHz for electronic and magnetic fields
LRIT – Long-Range Identification and Tracking
MF – Medium frequency 300 kHz – 3 MHz
MiTS – Maritime Information Technology Standard
MRCC – Maritime Rescue Coordination Centers
MSI – Maritime safety information
NAVTEX – Navigation Telex automated one-way communication system for maritime safety information (MSI)
NFV – Network function virtualization
NLP – Natural language processing
OCPN – a widely used open-source navigation software
OSP – Open Simulation Platform
PA – Public address systems
RF – Radio frequencies
SATCOM – Satellite Communications
SBCN – Shipboard communication and network system
SDN – Software-defined network
SDR – Software-defined radio
SMCP – Standard Marine Communication Phrases
SSAS – Ship Security Alert System
STCW – Standards of Training, Certification, and Watchkeeping for Seafarers
UHF – Ultra High Frequency, 300 MHz – 3 GHz
VDES – VHF Data Exchange System
VHF – Very High Frequency, 30-300 MHz Marine radio = 156-174 MHz
VTS – Vessel traffic services
Terminology
System of Systems (SoS): A collection of multiple systems — often independently developed and managed — that interact to deliver capabilities greater than any subsystem alone.
Cyber‑Physical Systems (CPS): Integrated digital and physical systems linking computation, networking, and mechanical processes (e.g., propulsion, navigation, cargo handling).
Socio‑Technical Systems (STS): Systems that combine technology with human operators, organizational processes, and regulatory structures, recognizing that performance and resilience depend on both technical and social factors.
Supervisory Control and Data Acquisition (SCADA): Platforms and software for real‑time monitoring and control of industrial processes, central to shipboard OT management.
Operational Technology (OT): Hardware and software that detect or cause changes through direct monitoring and control of physical devices, processes, and events.
Information Technology (IT): Enterprise computing systems managing data, planning, and communications are increasingly converged with OT in modern ships.
Internet of Things (IoT): A network of connected sensing and control devices, often lightweight and pervasive, extending shipboard system interconnections.
Convergence: Integration of IT, OT, and IoT networks, often leveraging cloud services, virtualization, and software‑defined networking.
Resilience: The ability of maritime systems to anticipate, withstand, recover from, and adapt to disruptions, whether cyber, physical, or organizational.
Student Learning Objectives
After completing this chapter, students will be able to:
- Differentiate between Cyber‑Physical Systems (CPS) and Socio‑Technical Systems (STS) in maritime contexts and explain their convergence within System of Systems (SoS).
- Identify vulnerabilities in shipboard communication, command, and control systems.
- Evaluate the cascading risk of cyber incidents across interconnected networks.
- Apply maritime cybersecurity standards and frameworks to assess system trustworthiness.
- Articulate strategic and technical considerations for designing resilient, secure shipboard systems.
Maritime Communication Systems
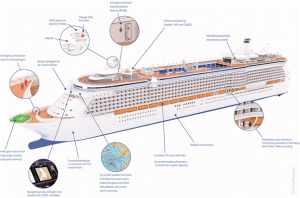
Maritime communication systems play a critical role within the broader maritime Information and Communication Technology (ICT) framework, which encompasses the full spectrum of digital, analog, and hybrid information systems onboard vessels, across port infrastructure, and within operator enterprise networks. Understanding this layered ICT context is fundamental for grasping the structure and function of maritime communications, command, and control systems. Figure 7-1 succinctly highlights key mandated systems such as navigational aids (AIS, ECDIS, radar), satellite and VHF communication, emergency response equipment (EPIRB), and information systems critical for operational safety. This real-world regulatory framework embodies the complexity and criticality of maritime ICT in passenger shipping.
In the last decade maritime industry has undergone a profound digital transformation, with modern vessels increasingly relying on complex shipboard networks to control navigation, propulsion, communication, cargo handling, and crew welfare systems. This integration of Information Technology (IT) and Operational Technology (OT) systems improves efficiency but also expands the attack surface, making ships vulnerable to sophisticated cyber threats. Cyberattacks against shipboard networks can disrupt operations, cause physical damage, and even endanger lives and the environment.
Shipboard Communication, Navigation, and Network Systems
Modern ships operate as complex cyber-physical socio-technical systems where communication, navigation, network infrastructure, and SCADA-based operational technology (OT) are deeply interconnected (see Figure 7-2). This integration delivers efficiency, safety, and situational awareness — but it also creates shared vulnerabilities. Shipboard communication and network systems (SBCN) provide vital connectivity both within a vessel and with the outside world, ensuring safe operation, coordination, and emergency response.
These systems fall into two main categories: internal and external communications.
Internal Communication Systems (ICS) onboard maritime vessels[1] are essential for maintaining operational coordination, safety, and efficient crew interaction. Traditional dial telephones installed throughout the ship’s compartments provide reliable voice contact between different areas, facilitating routine communication among crew members. Complementing these, sound-powered phones operate without requiring external electrical power, making them indispensable for critical communication during power outages or emergencies. The ship’s mission and announcement systems, including public address (PA) systems, enable urgent paging and general broadcasts that keep the crew promptly informed of important operational updates or safety alerts. For more flexible and mobile communication, handheld VHF and UHF radios are used extensively during deck operations, small boat maneuvers, or as backup communication channels. Additionally, intercoms and traditional voice tubes serve as direct communication links in key ship sections, providing immediate and clear voice contact critical for coordination in confined or noisy environments. Together, these systems form an integrated, redundant communications network that supports continuous, reliable internal communication vital to the safe and efficient operation of the vessel.
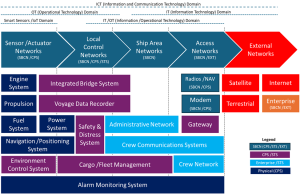
External Communication Systems on maritime vessels constitute the primary means for establishing voice and data contact with other ships, coastal stations, and satellite networks, thereby underpinning navigation safety, operational coordination, and distress signaling. Very High Frequency (VHF) radios remain the principal tool for reliable short-range voice communications, facilitating ship-to-ship and ship-to-shore interactions in coastal and congested waters due to their simplicity and effectiveness. For longer-distance communications, Medium Frequency (MF) and High Frequency (HF) radios are employed, supporting open ocean contact and enabling transmissions of global positioning data as well as distress and safety communications. Modern vessels deploy Satellite Communications (SATCOM) systems, such as Inmarsat FleetXpress and Sealink C/Ku-Band, which provide expansive coverage by enabling global voice, data, and internet connectivity even when beyond the reach of terrestrial networks. Integral to safety and distress operations, the Global Maritime Distress and Safety System (GMDSS) employs an array of terrestrial and satellite communication technologies mandated for commercial vessels, ensuring prompt distress signaling and safety message dissemination worldwide. Additionally, systems such as the Automatic Transmitter Identification System (ATIS) complement VHF usage in certain regions by automatically transmitting ship identification codes, enhancing situational awareness and regulatory compliance. Together, these external systems form a resilient, multilayered communication architecture crucial to the safe and efficient maritime operation in global waters.
Navigation systems integrate advanced electronic sensors and information systems to ensure precise positioning, situational awareness, and safe navigation globally. The gyro compass serves as an electronic heading reference providing accurate directional data unaffected by magnetic interference, essential for autopilot and navigational tasks. Complementing this, GPS integrated with Electronic Chart Display and Information Systems (ECDIS), such as Furuno GP-170, enables real-time, accurate positioning and digital chart plotting, supporting route planning in compliance with International Convention for Safety of Life at Sea (IMO SOLAS) standards. Doppler logs provide vessel speed relative to water for navigation and collision avoidance computations. Radar systems operating on S-band and X-band frequencies (2-4 GHz and 8-12 GHz ranges, respectively) detect nearby vessels, landmasses, and weather, enhancing safety in poor visibility conditions. Direction finding equipment supports signal location and tracking, aiding search and rescue operations, while depth sounders and echosounders, including fathometers and multibeam sonars, measure water depth and profile ocean bottoms to mitigate grounding risks. These systems collectively form an integrated multi-sensor navigation platform essential for modern maritime operations.
Shipboard network systems have evolved into highly sophisticated infrastructures integrating Information Technology (IT), Operational Technology (OT), and emerging communication protocols to support modern maritime operations. These systems interconnect an array of computing resources, sensor arrays, and control devices, forming robust shipboard computer networks that facilitate navigation, operational command, and communication functions. Central to this integration are Integrated Bridge Systems (IBS), which centralize navigation, communications, and monitoring equipment, providing operators with unified situational awareness and control. Operational Technology networks manage vital machinery systems, propulsion, cargo handling, and environmental controls, often interfacing with IT systems to enable vessel digitalization and automation. Wireless technologies, including onboard Wi-Fi and Internet of Things (IoT) networks, augment crew communications and system monitoring, facilitating real-time data exchange across shipboard assets. Complementing internal networks, satellite data links extend operational reach by providing global internet connectivity and remote management capabilities. Given the criticality of these integrated systems, layered cybersecurity architectures and continuous monitoring are imperative to protect against intrusions, system disruptions, and equipment failures, ensuring operational resilience and safety. The combination of technological convergence and stringent cyber defense frameworks defines the contemporary shipboard network landscape, enabling operational efficiency while managing emerging cybersecurity risks.
Supervisory Control and Data Acquisition (SCADA) systems form the backbone of industrial control operations onboard modern vessels by enabling centralized real-time monitoring, data acquisition, and command of critical ship systems. Shipboard SCADA platforms integrate diverse functions such as navigation including Global Positioning System (GPS), Long-Range Identification and Tracking (LRIT), Automatic Identification System (AIS), Automatic Radar Plotting Aid (ARPA), and Electronic Chart Display and Information System (ECDIS)), engine room and propulsion control, cargo management, environmental controls (e.g., HVAC, tank levels, ballast water systems), safety and distress systems (such as the Global Maritime Distress and Safety System [GMDSS] and Ship Security Alert System [SSAS]), along with voyage data recorders and alarm monitoring. These systems provide operators and increasingly remote controllers with comprehensive situational awareness via Human-Machine Interfaces (HMIs), consolidating mechanical, navigational, environmental, and communication data streams into unified control terminals. The convergence of Information Technology (IT) and Operational Technology (OT) on digitized ships means that SCADA networks, traditionally isolated for engine room or ballast tank automation, are now interlinked with onboard IT, passenger internet systems, and vendor maintenance channels, necessitating comprehensive cybersecurity measures to monitor and protect the entire digital ecosystem against disruptions and intrusions. Modern SCADA implementations use open architecture, standardized protocols such as Modbus, OPC-UA, and MQTT, and support remote configuration capabilities, providing scalable, flexible, and secure control solutions that underpin the safety and operational efficiency of contemporary maritime vessels.
Maritime Communication Protocols and Standards
Maritime communication relies on a diverse set of internationally agreed protocols and standards that ensure interoperability, safety, and efficiency of voice and data exchange across shipboard systems, coastal stations, and global satellite networks. These protocols span multiple physical media and operational domains, supporting routine communication as well as emergency distress signaling.
IMO Standard Marine Communication Phrases (SMCP)
The International Maritime Organization (IMO) developed Standard Marine Communication Phrases (SMCP) to establish a simplified, standardized maritime English for use in navigational and safety‑related communications. SMCP addresses the challenge of language barriers on the bridge and during ship-to-shore or ship-to-ship interactions, standardizing safety-related verbal exchange in normal and emergency contexts. Under the International Convention on Standards of Training, Certification, and Watchkeeping for Seafarers (STCW), SMCP proficiency is required for officers on navigational watches.
Global Maritime Distress and Safety System (GMDSS)
The GMDSS framework integrates terrestrial and satellite radio technologies to enable automated distress alerting and safety messaging. Developed cooperatively by IMO and International Telecommunication Union (ITU), it operates on distinct maritime frequency bands (VHF, MF, HF) using digital selective calling (DSC), satellite EPIRBs, and navigational warning broadcast systems such as the Navigation Telex automated one-way communication system for maritime safety information (MSI) / (NAVTEX). The system is constantly evolving, incorporating new satellite constellations and digital data modes to improve global coverage and reliability.
Digital and Radio Protocols
Maritime communication increasingly employs data-rich protocols built upon internet standards, particularly IP-based transport protocols for general communications and control information transfer among shipboard and shore systems. Specialized maritime communication protocols include:
- Automatic Identification Systems (AIS): Broadcasting vessel position, identity, and navigational status to other ships and coastal monitoring stations with mandated global deployment on commercial vessels.
- IEC 61162 Series: Specifies digital communication protocols for interconnected maritime navigation equipment, facilitating data exchange between radars, ECDIS, autopilots, and other bridge systems.
- VHF Data Exchange System (VDES): Enhances AIS capability with higher bandwidth and two-way satellite communications for data-centric applications, including voyage planning and maritime safety services.
Emerging Standards
The maritime industry is actively developing and adopting newer standards for enhanced ship-shore communication, cybersecurity, and data interoperability, such as ISO 16425 for ship communication networks architecture and management. These efforts focus on ensuring secure, reliable information exchange in increasingly complex and converged ICT environments.
Case Studies
Maritime communication systems operate within a complex socio-technical network where diverse technologies, protocols, and human operators interact dynamically. The case studies on communication breakdowns, near-misses, and satellite-based distress response highlight this complexity, revealing how interdependent communication channels and stakeholder roles create potential failure points. The resilience of these systems stems from redundancy, standardized protocols like IMO SMCP and GMDSS, and multilayered defense mechanisms that enable rapid detection, correction, and recovery from disruptions. Concurrently, the increased digitization and integration of shipboard and shore ICT systems expand the attack surface, necessitating robust cybersecurity controls to protect against malicious interference. Thus, complexity, resilience, and security in maritime communications emerge as intertwined system properties essential for safe, reliable, and continuous maritime operations in challenging and evolving environments.
Students can review these case studies to:
- Understand the practical impacts of communication protocol failures and successes. Note that communications involve a combination of spoken languages, their conversational proficiencies, adequate training, and clarity of speech, not just communications technology or the current hype of natural language processing (NLP) through chatbots
- Analyze the role of standardization, language, and technology in maritime safety.
- Explore how modern ICT tools and protocols (e.g., SATCOM, IoT) enable operational resilience.
Case Study 1: Vessel Grounding Caused by Communication Breakdown[1]
Source: Digimar Project
Summary: A bulk carrier runs aground in dense fog after ineffective communication with Vessel Traffic Services (VTS), highlighting language barriers and the critical need for clear, standardized communication protocols. It underscores how an incomplete understanding of safety messages can lead to disasters.
Link /Reference: (Network, 2019; SCENARIOS – Digi Mar – Digital Education for Maritime Communication, n.d.)
Case Study 2: Near-miss between Incoming and Outgoing Vessels due to Miscommunication[2]
Source: Digimar Project
Summary: This case study describes a close-call incident narrowly avoided by two vessels due to ambiguous communication. It examines linguistic and procedural factors influencing maritime safety and the importance of clear, unambiguous standardized phrasing in maritime communications.
Link /Reference: (Reports, 2019; SCENARIOS – Digi Mar – Digital Education for Maritime Communication, n.d.)
Case Study 3: Improving Maritime Communication Skills and Safety – DigiMar Erasmus Program[3]
Source: 10th International Conference on Maritime Transport (MT’24)
Summary: Reviews statistical safety improvements linked to communication training, highlights communication-induced accidents, and advocates for closed-loop communication protocols and crew resource management (CRM) training to boost situational awareness.
Link /Reference: (Brcko Satler & Jurkovič, 2024; Jurkovič & Satler, 2025)
Case Study 4: Inmarsat Government Maritime Case Studies[4]
Source: Inmarsat
Summary: Case studies illustrate how satellite communications provide dependable global coverage for distress response, anti-piracy missions, and tracking, showcasing the critical role of SATCOM in maritime communications.
Link /Reference: (Inmarsat, 2020)
Case Study 5: Maritime IoT Protocols and Real-world Deployments
Source: Sinay.ai
Summary: Explores how emerging IoT communication protocols such as LoRaWAN, NB-IoT, and satellite mesh networks impact maritime operational efficiency and safety, offering case insights for modern data communications onboard vessels and in ports.
Link /Reference: (“Top IoT Protocols in Maritime,” n.d.; Xia et al., 2020)
Maritime ICT Threats and Challenges
The challenges facing maritime SCADA and ICT systems are multifaceted and deeply rooted in the sector’s ongoing digital transformation. The integration and convergence of IT and OT networks onboard ships, while increasing operational efficiency, simultaneously amplify cyber vulnerabilities, especially when crew cyber awareness and training lag behind technological adoption. Legacy protocols like Modbus and OPC-UA, combined with vendor-specific and proprietary interfaces, create a fragmented landscape that complicates unified security enforcement and elevates risk due to insufficient segmentation and outdated technologies. Remote monitoring and configuration, increasingly necessary due to shortages in onboard technical staff, introduce further vulnerabilities where remote access controls are weak or misconfigured, potentially allowing unauthorized intrusion or manipulation. Bandwidth limitations inherent in maritime satellite links often force network architects to implement suboptimal data buffering or reduce network segmentation, which may inadvertently expose SCADA systems to attacks. Importantly, many existing vessels were not originally designed with integrated cybersecurity considerations for their digital ecosystems, leading to architectural mismatches and “bolted-on” solutions that lack comprehensive lifecycle security, thus increasing susceptibility to operational disruptions, safety incidents, or even physical consequences onboard. Addressing these challenges requires a holistic approach combining updated technical architectures, rigorous cybersecurity protocols, continuous crew training, and industry-wide standards to enhance maritime resilience in the face of evolving cyber threats.
COMMON THREATS – A DETAILED VIEW
Threat Brief: GPS Spoofing
Threat Summary: False or manipulated GNSS (e.g., GPS) signals are broadcast to deceive maritime navigation systems, causing a vessel to miscalculate or misreport its true position. This can lead to severe navigational errors, especially in systems that integrate GPS with automatic functions like autopilot or collision avoidance.
Target Systems: Shipboard systems most impacted by GPS spoofing include: ECDIS (Electronic Chart Display and Information System), Autopilot and Navigation Control Systems, AIS (Automatic Identification System – for position reporting), Bridge Integrated Systems (BIS), Voyage Data Recorder (VDR)
Nature of the Threat or Attack: GPS spoofing involves transmitting counterfeit GPS /GNSS signals from a nearby device with stronger signal strength than legitimate satellites. The ship’s GPS receiver locks onto the stronger, false signal and begins reporting a manipulated position. This can be done gradually (meaconing) to mask the change or suddenly to trigger operational disruption. When GPS data feeds into interconnected systems (e.g., ECDIS, AIS, autopilot), false data can cascade across navigation functions.
Indicators of Compromise (IOCs):
- Sudden deviation of position without matching physical movement
- Inconsistent speed-over-ground and course-over-ground readings
- The reported position does not align with radar, visual, or inertial observations
- Autopilot behavior that conflicts with known route plans
- Alerts from GNSS signal integrity checks (if supported)
Indicators of Vulnerability or Exposure (IOVs/IOEs):
- Use of unencrypted civilian GPS signals (L1 C/A)
- Lack of integration with Inertial Navigation Systems (INS) or Radar Overlays
- Absence of GPS /GNSS signal anomaly detection tools or logs
- GPS /GNSS receiver firmware has not been updated to detect spoofing/jamming behaviors
- Use of GPS /GNSS as a single point of truth in integrated navigation systems
Vulnerabilities Exploited:
- Lack of GPS signal authentication or verification
- Over-reliance on GNSS input in ECDIS/autopilot without redundancy
- No cross-verification with radar or inertial navigation data
- Weak crew awareness or procedural gaps in manual navigation practices
Threat Impact /Risks:
- Vessel strays off course, enters restricted or dangerous waters
- Collision risk or grounding due to navigational inaccuracies
- Potential legal/military ramifications (e.g., breaching territorial waters)
- Disruption of voyage schedule or commercial operations
- Loss of trust in autonomous or automated bridge systems
Containment and Mitigation Actions:
- Enable GNSS cross-checks with radar overlays and INS on the bridge
- Regular manual position fixes using visual bearings and paper charts
- Ensure autopilot can be overridden manually with bridge procedures in place
- Train bridge officers to recognize spoofing symptoms and conduct immediate audits
- Notify fleet operations and maritime authorities if spoofing is suspected
- Maintain navigation incident logs for forensic analysis
- Consider using anti-spoofing GNSS receivers with signal authentication features (e.g., GPS L5, Galileo OS-NMA)
Notable /Known Incidents:
- Black Sea, 2017 – Multiple ships reported inaccurate GPS data, placing them inland; believed to be caused by deliberate GPS spoofing
- China Coastal Regions, 2019–2020 – AIS tracks showed vessels circling or appearing at incorrect positions, suspected GPS spoofing
Threat Brief: GPS Jamming
Threat Summary: GPS jamming is the deliberate transmission of high-power radio frequency (RF) signals to overwhelm GPS receivers, causing a denial or severe degradation of satellite navigation signals. This disruption leads to loss of positioning information critical for maritime navigation and control.
Target Systems: Affected shipboard systems typically include Electronic Chart Display and Information System (ECDIS), Autopilot and navigation control systems, Automatic Identification System (AIS) (if reliant on GNSS timing/position), Bridge Integrated Systems (BIS), Voyage Data Recorder (VDR) (in some cases)
Nature of the Threat or Attack: The attacker uses a high-power RF transmitter to saturate the GPS receiver’s antenna with noise, effectively blocking the reception of authentic GPS signals. Unlike spoofing, jamming causes a loss or degradation of signal, leading to navigation systems losing their positioning capability altogether. Jamming can be localized or wide-area and can be intentional (hostile actor) or accidental (interference).
Indicators of Compromise (IOCs):
- Sudden loss of GPS signal or repeated GPS signal degradation alarms across navigation consoles
- Multiple simultaneous GPS receiver alarms across the bridge systems
- ECDIS or autopilot switching to backup or manual navigation modes unexpectedly
- Radar and visual navigation are showing no corresponding position updates from GPS
- Crew reports of GPS signal loss or degradation during voyage
Indicators of Vulnerability or Exposure (IOVs/IOEs):
- Single GNSS constellation dependency (e.g., GPS-only receivers)
- Lack of fallback or redundant navigation systems (e.g., inertial navigation, radar overlays)
- Poor RF shielding or antenna placement is vulnerable to interference
- Inadequate crew training on non-GPS navigation procedures
- Integrated systems that rely exclusively on GPS without cross-checks
Vulnerabilities Exploited:
- Absence of GNSS signal authentication or integrity checking
- Lack of multi-constellation/multi-frequency GNSS support to mitigate jamming
- Over-reliance on GPS as a sole source of navigation information
- Insufficient physical and technical protections of antenna and receiver hardware (ex, Poor RF shielding)
Threat Impact /Risks:
- Loss of automated navigation and position fixing capability
- Increased workload and stress on the bridge crew to navigate manually or with degraded systems
- Elevated risk of collision, grounding, or navigational errors, especially in poor visibility or congested waters
- Potential disruption to vessel scheduling and logistics
- Reduced situational awareness and increased vulnerability to further attacks
Containment and Mitigation Actions
- Switch to Dead Reckoning (DR) and radar-based navigation methods immediately
- Power down or isolate jammed GPS receivers to avoid confusing false alarms
- Activate alternate GNSS systems (GLONASS, Galileo) with dual/multi-constellation receivers
- Maintain visual lookout and manual navigation procedures as per bridge resource management protocols
- Report incidents to fleet operations and maritime authorities for situational awareness
- Review antenna placement and improve RF shielding and filtering hardware
- Conduct crew training drills on GPS denial scenarios and recovery procedures
Notable /Known Incidents
- Gulf of Oman, 2019 — GPS jamming incidents suspected to be part of regional tensions, impacting commercial shipping navigation.
Threat Brief: Ransomware
Threat Summary: Ransomware is malicious software that infects shipboard computer systems, encrypting data and critical operational files. Attackers demand payment (usually in cryptocurrency) to restore access. This can severely disrupt maritime operations and compromise safety.
Target Systems: Bridge administration systems (e.g., navigation, communication), Cargo and manifests management systems, Engine control and monitoring systems (in some advanced ships), Shipboard IT networks and enterprise resource planning (ERP) systems
Nature of the Threat or Attack: Ransomware typically enters the ship’s IT ecosystem via phishing emails, infected USB drives, or vulnerabilities in outdated software. Once activated, it encrypts files and displays ransom demands with instructions for payment. The encryption prevents crew and operators from accessing essential systems or data until the ransom is paid or systems are restored.
Indicators of Compromise (IOCs):
- Sudden inaccessibility of critical files or systems (admin tools, manifests, cargo databases)
- Presence of ransom notes, often in common directories (desktop, root folders)
- File extensions appended with unusual suffixes like .locked, .enc, .crypt
- Unusual outbound network traffic (to ransomware command-and-control servers)
- Alerts from endpoint detection and response (EDR) or antivirus solutions
Indicators of Vulnerability or Exposure (IOVs/IOEs):
- Outdated or unpatched operating systems and applications
- Lack of endpoint protection solutions (antivirus, EDR) or disabled protections
- Crew members using external USB devices without scanning
- Inadequate cybersecurity awareness and phishing training
- Poor network segmentation allows malware lateral movement
Vulnerabilities Exploited:
- Known software vulnerabilities or zero-day exploits in shipboard IT
- Social engineering tactics trick the crew into executing malicious payloads
- Insufficient backup policies or untested backup recovery procedures
- Lack of multi-factor authentication on critical systems
Threat Impact /Risks:
- Loss of access to critical shipboard systems (navigation, admin, cargo manifests)
- Disruption of voyage planning, port clearance, and cargo handling operations
- Potential immobilization of the vessel if key control systems are affected
- Financial losses due to operational downtime, ransom payments, and recovery costs
- Legal and regulatory consequences if a data breach or loss of control affects safety or compliance
Containment and Mitigation Actions:
- Immediate disconnection from shore-side and external networks to prevent spread
- Isolation or shutdown of infected nodes and critical systems
- Restoration of systems from verified secure backups
- Notification of the incident to the ship cybersecurity team, company management, and relevant authorities (e.g., coast guard, port authorities)
- Preservation of forensic evidence through imaging of affected devices for root cause analysis
- Crew cybersecurity training on phishing avoidance and USB device hygiene
- Implementation of network segmentation and least-privilege access controls
- Regular patch management and endpoint protection updates
Notable /Known Incidents:
- Maersk Ransomware Attack, 2017 — The NotPetya ransomware attack disrupted Maersk’s global shipping operations for weeks, causing estimated losses of up to $300 million
- COSCO Shipping Ransomware Incident, 2018 — Network disruption caused significant delays and operational challenges
Threat Brief: AIS Spoofing
Threat Summary: AIS (Automatic Identification System) spoofing involves broadcasting falsified AIS signals to create phantom vessels, duplicate identities, or misleading ship positions. This undermines situational awareness and maritime safety by confusing ship traffic management and radar correlation.
Target Systems: AIS transceivers (shipboard and shore-side), Vessel Traffic Services (VTS) systems, Bridge navigation and situational awareness systems relying on AIS data, Maritime Domain Awareness (MDA), and port authority monitoring systems
Nature of the Threat or Attack: Attackers generate counterfeit AIS messages with false Maritime Mobile Service Identities (MMSIs), positions, and ship details. This can create “ghost ships” or duplicate legitimate vessel identities. The attack exploits the fact that AIS transmissions are unencrypted and unauthenticated. AIS receivers, both onboard and onshore, can be fed misleading data, which can be used to mask illegal activities, confuse traffic, or cause collisions.
Indicators of Compromise (IOCs):
- Detection of duplicate MMSI numbers on AIS displays
- Unusual or impossible routes, such as vessels showing movement on land or at unrealistic speeds
- Presence of phantom vessels on AIS without corresponding radar or visual contact
- Abrupt changes in vessel identity or characteristics inconsistent with known ship data
- Alerts or flags raised by AIS data validation or anomaly detection systems
Indicators of Vulnerability or Exposure (IOVs/IOEs):
- AIS protocol lacks encryption or authentication of transmitted messages
- Heavy reliance on AIS data for collision avoidance and situational awareness without cross-validation from radar or visual means
- Lack of integration between AIS and other sensor systems onboard (radar, ECDIS overlays)
- Absence of anomaly detection software or real-time monitoring of AIS data integrity
Vulnerabilities Exploited:
- Inherent protocol design limitations: no message encryption or sender authentication
- Overreliance on AIS without cross-checking radar, visual lookouts, or VHF radio communication
- Use of inexpensive AIS spoofing devices readily available on the black market
- Insufficient crew awareness or training regarding AIS limitations and potential threats
Threat Impact /Risks:
- Operational confusion and increased risk of collision or navigational errors
- Potential use of spoofed AIS for illegal activities, including smuggling, piracy, or evading detection
- Regulatory and reputational damage to shipping companies and port authorities
- Disruption to maritime traffic management and emergency response coordination
Containment and Mitigation Actions:
- Cross-validate AIS targets with radar, visual bearings, and VHF radio communications
- Report detected anomalies to port authorities, Vessel Traffic Services (VTS), and maritime domain awareness centers
- Reboot AIS transceiver units to clear potential corrupted buffers or settings
- Conduct forensic audits of AIS logs and investigate the source of suspicious signals
- Train bridge officers on AIS spoofing risks and response protocols
- Implement anomaly detection and multi-sensor fusion systems where possible
Notable /Known Incidents:
- Baltic Sea Incident, 2024 — Multiple phantom vessels appeared on AIS near conflict zones, misleading commercial and naval ships
- Singapore Strait, 2020 — AIS spoofing used to mask the true identity of vessels involved in illegal fishing activities
Threat Brief: Phishing & Social Engineering
Threat Summary: Phishing and social engineering attacks use deceptive communications—often emails or messages—to trick crew members into revealing credentials, clicking malicious links, or executing malware, thereby compromising shipboard systems or networks.
Target Systems: Shipboard administrative and management systems, Crew portals and email accounts, IT infrastructure and internal networks, Navigation support and communication systems (via indirect compromise)
Nature of the Threat or Attack: Attackers craft convincing emails or messages that appear legitimate, often mimicking trusted sources. These messages contain malicious attachments, links to fake websites, or requests for sensitive information. Successful phishing enables attackers to gain unauthorized access, deploy malware, or steal sensitive data. Social engineering extends beyond email, exploiting human psychology through phone calls or in-person deception.
Indicators of Compromise (IOCs):
- Emails with suspicious attachments or mismatched sender domains
- Credential reuse warnings from security monitoring tools
- Unusual or abnormal login times and locations for crew accounts
- Unexpected password reset requests or account lockouts
- Reports from the crew about phishing attempts or suspicious communications
Indicators of Vulnerability or Exposure (IOVs/IOEs):
- Lack of regular and updated cybersecurity training for crew and staff
- Use of personal (non-secure) email accounts on shipboard or critical devices
- Absence of email security measures such as sandboxing, anti-phishing filters, or link scanning
- Weak or reused passwords across ship systems and services
- Lack of multi-factor authentication (MFA) on critical accounts
Vulnerabilities Exploited:
- Human factors: trust, curiosity, and lack of awareness
- Technical gaps: absence of email filtering, anti-malware, and network segmentation
- Weak credential policies and the absence of MFA
- Poor device hygiene (e.g., usage of personal devices or unregulated USB usage)
Threat Impact /Risks:
- Unauthorized access to shipboard administrative systems or crew portals
- Introduction of malware or ransomware into internal networks
- Potential data theft or exfiltration of sensitive voyage or cargo information
- Disruption of ship operations and increased risk to safety and compliance
- Financial loss due to remediation, operational delays, and possible ransom payments
Containment and Mitigation Actions:
- Quarantine suspicious emails and related artifacts for forensic analysis
- Immediately reset compromised passwords and invalidate session tokens
- Isolate affected user accounts and devices from the network
- Conduct regular awareness training and phishing simulation exercises post-incident
- Implement robust email security solutions (sandboxing, domain verification, link scanning)
- Enforce strong password policies and deploy multi-factor authentication
- Monitor network and user behavior for signs of lateral movement or further compromise
Known Incidents:
- Maersk Phishing Incident, 2017 — Part of the NotPetya outbreak initially spread via phishing emails, causing global disruption
- COSCO Shipping Email Compromise, 2018 — Spear-phishing led to credential theft and internal network infection
Threat Brief: USB-Based Malware
Threat Summary: Malware can infiltrate shipboard systems through infected USB devices, often introduced unintentionally by engineers or crew using personal USB drives. This vector bypasses network defenses and can lead to severe operational disruptions.
Target Systems: Electronic Chart Display and Information System (ECDIS), Engine monitoring and control systems, Propulsion and automation systems, Shipboard IT, and network infrastructure
Nature of the Threat or Attack: Malicious software is introduced via USB drives containing infected executables or scripts. Once plugged into critical systems, malware can modify system settings, falsify telemetry data, corrupt files, or spread laterally to other connected systems, leading to degraded or compromised ship functions.
Indicators of Compromise (IOCs):
- Unexplained new USB connection logs shortly before system anomalies or instability
- Unexpected changes in system registry entries or new unknown processes starting
- Antivirus or endpoint security logs flagging known malware signatures linked to USB devices
- Sudden system crashes or abnormal behavior following USB device usage
Indicators of Vulnerability or Exposure (IOVs/IOEs):
- Lack of USB port control, monitoring, or device whitelisting
- Absence of endpoint antivirus or endpoint detection and response (EDR) tools on critical ship systems
- Routine use of personal or unverified USB drives by engineers or crew for diagnostics or data transfer
- Lack of formal USB usage policies and malware scanning procedures on board
Vulnerabilities Exploited:
- Physical access to critical systems, allowing USB insertion
- Lack of network segmentation and endpoint security controls
- Absence of user awareness regarding the risks of using untrusted removable media
- Inadequate patching and security hygiene on endpoint devices
Threat Impact /Risks:
- Compromise of navigation, engine control, or propulsion systems with safety implications
- Corruption or falsification of critical sensor and telemetry data
- Spread of malware to other shipboard or enterprise-connected systems, escalating operational risk
- Potential operational downtime and financial costs for remediation and recovery
Containment and Mitigation Actions:
- Physically isolate affected terminals immediately to prevent malware spread
- Reimage infected systems using trusted backups or clean installation media
- Implement strict USB usage policies restricting use to approved devices only
- Deploy endpoint protection tools, including antivirus and Endpoint Detection and Response (EDR) solutions, with USB device monitoring
- Conduct crew training on risks of removable media and secure data handling practices
- Monitor USB connection logs and anomalous process executions for early detection
Notable /Known Incidents:
- COSCO Shipping Malware Infection, 2018 — Malware introduced via USB was a suspected vector for network infection, impacting port operations
- Nuclear-Powered Submarine USB Malware Case — Publicly reported incidents (in non-military contexts) highlight the risk of USB vectors in critical control systems
Threat Brief: SATCOM Exploits
Threat Summary: Unauthorized access or hijacking of satellite communication (SATCOM) terminals due to exposed management services, default or weak credentials, and outdated firmware can severely disrupt ship-to-shore communications and compromise sensitive data.
Target Systems: Shipboard SATCOM terminals and modems, Satellite management interfaces (web-based or CLI), Network infrastructure bridging SATCOM with ship IT and OT systems
Nature of the Threat or Attack: Attackers exploit exposed management ports or use default/hardcoded credentials to gain unauthorized access to SATCOM terminals. This allows them to alter terminal configurations, intercept, or block communications, exfiltrate sensitive information, or pivot into internal networks. Firmware vulnerabilities may also be leveraged to install persistent malware.
Indicators of Compromise (IOCs):
- Unexpected changes in SATCOM terminal configuration settings
- Unrecognized login attempts originating from external or suspicious IP addresses
- Unexplained bandwidth spikes, sudden communication outages, or degraded link performance
- Alerts from intrusion detection/prevention systems monitoring SATCOM traffic
Indicators of Vulnerability or Exposure (IOVs/IOEs):
- Use of default, weak, or hardcoded passwords on SATCOM devices
- Management interfaces (e.g., web portals, SSH, Telnet) accessible from untrusted networks or the internet
- Firmware versions known to have security vulnerabilities or lacking recent patches
- Lack of network segmentation between SATCOM and internal IT/OT systems
Vulnerabilities Exploited:
- Poor credential management and a lack of password rotation policies
- Exposure of critical management services due to misconfigured firewalls or remote access
- Outdated firmware with unpatched security flaws
- Insufficient network segmentation and monitoring
Threat Impact /Risks:
- Loss or disruption of critical ship-to-shore communications, impacting navigation, safety, and operations
- Exposure of sensitive ship traffic, cargo, or crew information to adversaries
- Potential lateral movement by attackers from SATCOM into critical internal IT or OT networks, increasing the risk of broader compromise
- Operational delays and increased costs due to incident response and recovery
Containment and Mitigation Actions:
- Temporarily disconnect or cut off the SATCOM link if a compromise is suspected
- Immediately reset passwords and enforce strong credential policies
- Update the SATCOM device firmware with the latest security patches
- Implement strict network segmentation between SATCOM systems and other shipboard networks
- Conduct a comprehensive credential and access audit on all SATCOM terminals
- Monitor the SATCOM network traffic continuously for anomalies and unauthorized access attempts
- Employ multi-factor authentication (MFA) where supported by SATCOM management interfaces
Notable /Known Incidents:
- Merchant Vessel SATCOM Hijacking, 2019 — Attackers gained access to the ship’s SATCOM via default credentials, causing communication blackouts and data interception
- Maritime Cyberattack Report, 2021 — Multiple SATCOM vulnerabilities exploited due to exposed management interfaces and unpatched firmware
Threat Brief: ECDIS Hacking
Threat Summary: Malicious actors manipulate Electronic Chart Display and Information System (ECDIS) data or exploit vulnerabilities in ECDIS devices to alter navigation charts or ship routes, risking severe navigational errors.
Target Systems: ECDIS units on the ship’s bridge, connected network infrastructure supporting ECDIS data transfers, and Remote management interfaces of ECDIS devices
Nature of the Threat or Attack: Attackers exploit unpatched software vulnerabilities or gain unauthorized network access to ECDIS devices. They may manipulate digital chart data or inject malicious files that cause erroneous route plotting, system crashes, or false alarms, potentially leading to course deviations.
Indicators of Compromise (IOCs):
- Error messages indicating invalid or corrupted chart data when loading files
- Unexpected or unintended course corrections or alarms triggered by ECDIS
- Application crashes or freezes when opening specific charts or data files
- Unusual network traffic to/from ECDIS devices, especially via remote ports (e.g., Telnet, FTP)
Indicators of Vulnerability or Exposure (IOVs/IOEs):
- Use of outdated or unpatched ECDIS software versions
- Remote access services are enabled without strong authentication or encryption
- Lack of network segmentation separating ECDIS from general IT networks
- No regular digital signature or integrity checks on chart files and firmware updates
Vulnerabilities Exploited:
- Software vulnerabilities in ECDIS operating systems or applications
- Weak or missing authentication on remote access ports
- Unsecured network configurations allow lateral movement or unauthorized access
- Lack of digital verification for chart data integrity
Threat Impact /Risks:
- Course deviation potentially leading to grounding, collision, or entry into restricted waters
- Loss or degradation of reliable route planning and navigation capabilities
- Disruption to bridge operations and increased workload on navigational officers
- Regulatory and legal consequences stemming from navigation failures
Containment and Mitigation Actions:
- Revert immediately to manual navigation methods using paper charts or radar-based fixes
- Reinstall ECDIS software from verified, trusted media to ensure system integrity
- Disable all remote access ports permanently unless strictly required and secured
- Implement and routinely perform digital integrity checks on electronic chart data and firmware updates
- Keep ECDIS software and firmware updated with the latest patches from vendors
- Segment ECDIS devices on separate secure networks to prevent unauthorized access
- Train the bridge crew to recognize ECDIS anomalies and report suspicious behavior promptly
Notable /Known Incidents:
- Port of Rotterdam ECDIS Compromise — Unauthorized manipulation of chart data caused temporary route confusion; mitigated before incident escalation
- Various Reported ECDIS Vulnerabilities — Vendor advisories highlight frequent vulnerabilities exploitable via open ports and unpatched software.
Threat Brief: Engine / Propulsion System Attack
Threat Summary: Adversaries exploit Operational Technology (OT) vulnerabilities to manipulate or disrupt engine control and ballast systems remotely, risking ship performance, stability, and safety.
Target Systems: Engine control systems and Programmable Logic Controllers (PLCs), Ballast water management and control systems, OT network infrastructure connecting propulsion and control devices, Vendor remote maintenance interfaces
Nature of the Threat or Attack: Attackers leverage unsecured or exposed PLCs, weak authentication, or unsegmented OT/IT networks to gain unauthorized access to critical propulsion and ballast control systems. Remote sessions, including those from vendors, can be hijacked or abused to manipulate engine RPM, ballast settings, or sensor inputs, causing unsafe operational conditions.
Indicators of Compromise (IOCs):
- Sudden or unexpected changes in engine RPM or ballast levels without operator command
- Abnormal sensor readings or overridden control commands detected by monitoring systems
- Unauthorized login attempts or unusual access patterns in the engine PLC logs
- Alerts or unusual traffic from vendor remote maintenance tools
Indicators of Vulnerability or Exposure (IOVs/IOEs):
- PLCs accessible remotely with default or weak credentials
- Lack of network segmentation between OT and IT environments
- Absence of continuous monitoring of vendor remote access sessions
- Unpatched PLC firmware and outdated OT software components
Vulnerabilities Exploited:
- Poor password hygiene and default credentials on PLCs and control devices
- Unsegmented network architectures allow lateral movement from IT to OT systems
- Insufficient monitoring and logging of remote maintenance activities
- Outdated or unpatched firmware and control software
Threat Impact /Risks:
- Altered engine performance, causing reduced maneuverability or mechanical stress
- Ship instability due to unauthorized ballast water adjustments, risking capsizing or grounding
- Increased safety and environmental hazards, including potential mechanical failures or pollution
- Potential delays, costly repairs, and regulatory non-compliance
Containment and Mitigation Actions:
- Activate emergency overrides and manual engine controls immediately to regain safe operations
- Disconnect compromised or affected control systems from the network to contain the attack
- Conduct thorough physical and system inspections of ballast and propulsion components post-incident
- Reassess and strengthen firewall rules and network segmentation to isolate OT systems
- Enforce strong authentication and credential management for PLC and vendor access
- Implement continuous monitoring and audit logging of remote sessions
- Regularly patch and update OT firmware and control software
- Conduct cybersecurity training for crew and vendors on secure maintenance practices
Notable /Known Incidents:
- COSCO Shipping OT Cyber Incident— Remote manipulation of engine systems suspected after vendor maintenance access was exploited
- Maersk Ransomware Attack, 2017 — Highlighted risks of unsegmented OT/IT networks allowing malware propagation to control systems
Threat Brief: Cargo System Manipulation
Threat Summary: Adversaries tamper with cargo manifests, control systems, or sensor data to cause cargo discrepancies, enabling smuggling, fraud, or operational disruptions.
Target Systems: Cargo management systems and manifest databases, Automated container handling and tracking systems, Web-based cargo portals and remote access interfaces, Sensors and IoT devices monitoring container status
Nature of the Threat or Attack: Attackers exploit weak authentication, poor encryption, or insufficient access controls to manipulate cargo data or system configurations. This can result in mismatches between actual and reported cargo, unauthorized modifications of manifests, or sensor data falsification.
Indicators of Compromise (IOCs):
- Cargo manifest discrepancies were detected during port inspections
- Unauthorized logins or file access events in the cargo system logs
- Reports of missing, duplicated, or untracked containers
- Alerts from anomaly detection in cargo sensor data
Indicators of Vulnerability or Exposure (IOVs/IOEs):
- Web-based cargo portals are lacking multi-factor authentication (MFA)
- Weak or incomplete audit trails and access controls
- Data-at-rest is stored without strong encryption
- Use of legacy or unsupported cargo management software
Vulnerabilities Exploited:
- Insufficient identity and access management (IAM) on cargo systems
- Lack of encryption and secure communication channels
- Poor logging and monitoring enable stealthy manipulation
- Vulnerabilities in IoT sensors or container tracking devices
Threat Impact /Risks:
- Smuggling or illegal cargo movement leading to customs violations
- Delays in cargo offloading cause operational and financial losses
- Reputational damage and regulatory penalties for the shipping company
- Potential security threats due to untracked hazardous materials
Containment and Mitigation Actions:
- Conduct manual reconciliation of cargo manifests with physical inventory checks
- Alert port authorities, customs, and all affected stakeholders immediately
- Apply security patches and software updates to cargo management systems
- Reset and enforce strong access credentials and enable multi-factor authentication
- Implement secure logging with real-time alerting for unauthorized access attempts
- Harden IoT and sensor security, including regular firmware updates and network segmentation
Known Incidents:
- Port of Antwerp Cargo Data Manipulation— A Cyberattack led to smuggling through falsified manifests, detected by a customs official’s
- Maersk Cargo System Disruption— Ransomware attack impacted cargo handling and manifest accuracy, delaying shipments worldwide
Defense Strategies
Network Segmentation: Separating IT (information technology) and OT (operational technology) networks through granular “at the resource” firewalls and VLANs is essential to isolate critical shipboard systems, thereby minimizing the risk that a compromise in one network spreads laterally and affects others. Proper segmentation helps protect sensitive operational assets such as navigation and propulsion from less secure networks like crew or guest Wi-Fi, raising the overall cybersecurity posture.
Endpoint Protection: Installing antivirus and Endpoint Detection and Response (EDR) software on administrative and bridge systems offers proactive defense by detecting and blocking malware, ransomware, and unauthorized software execution, which are common vectors for cyberattacks onboard ships. These tools are vital because endpoints serve as the frontline of defense where user interactions occur, making them frequent targets.
Access Control: Implementing strong password policies, multi-factor authentication (MFA), and enforcing least-privilege access restricts unauthorized individuals from accessing critical ship systems. This control reduces risks by verifying user identities and minimizing permissions to only those necessary, limiting the potential impact of compromised credentials or insider threats.
Incident Response: Maintaining robust incident response (IR) plans, comprehensive logs, backups, and conducting regular response drills enables rapid detection, containment, and recovery from cyber incidents. These preparation activities ensure the crew is ready to act efficiently during attacks, minimizing operational disruption and damage.
Crew Training: Regular cybersecurity training on topics such as phishing recognition and basic cyber hygiene empowers crew members to avoid common attack vectors targeting human error. Given that cyber defenses can be bypassed by social engineering, well-trained personnel are a critical layer of security.
Vendor Vetting: Thoroughly assessing and monitoring third-party vendors and their maintenance activities prevents supply chain compromises and hidden vulnerabilities. Given the complexity of maritime ICT systems, vendor risks must be managed rigorously to avoid introducing unsecured devices or configurations onboard.
Compliance Standards: Aligning shipboard cybersecurity practices with internationally recognized frameworks such as IMO MSC-FAL.1/Circ.3, NIST guidelines, and the ISM Code help ensure comprehensive governance and continuous improvement. These standards provide structured approaches to risk management and help vessels maintain regulatory compliance.
Emergent Properties in Maritime ICT
The fusion of highly heterogeneous networks, protocols, and stakeholder roles creates emergent complexities:
- Systemic Interdependence: Failures or cyber compromises in one subsystem can propagate across the shipboard SoS, impacting safety, operational continuity, and regulatory compliance.
- Multi-domain Integration: Communications span physical (radio waves, satellites, cables), protocol (IP, industrial, maritime-specific), and human/organizational domains, requiring robust interoperability and cybersecurity strategies.
- Cyber-Physical and Socio-Technical Dimensions: Maritime ICT is not only technical but socio-technical—human operators, procedures, and regulatory bodies interact continuously with cyber-physical systems, adding resilience challenges and vulnerabilities beyond purely technical issues.
Let us illustrate this with an example from the MiTS framework. The Maritime ICT (Information and Communication Technology) architecture, as conceptualized by the Maritime Information Technology Standard (MiTS) and related maritime digitalization efforts, provides a layered blueprint for the complex system of systems that integrates shipboard, shore, and enterprise infrastructures. MiTS describes the architecture across several abstraction layers:
- Physical/Transport Layer (communication and network protocols): Includes the physical communication media and network protocols connecting ships and shore—spanning satellite, VHF/AIS radio, cellular networks (4G/5G), Wi-Fi, and shipboard wired data networks.
- Information Layer (data models and standards): Standardized data models such as the IMO Reference Data Model and IHO S-100 framework ensure consistent exchange, interpretation, and processing of nautical, operational, and regulatory data.
- Functional and Process Layer (business process management, service orchestration): The orchestration of business processes, navigational workflows, fleet management, and control systems is supported by service interfaces and process management standards.
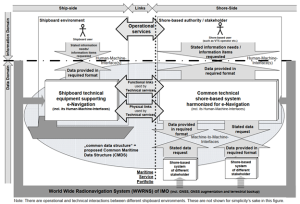
The Maritime ICT w-Navigation architecture (see Figure 7-3) embodies a complex, multilayered system that integrates shipboard ICT systems with shore-based infrastructures, providing a dynamic, real-time connection between vessels and onshore operational centers. Figure 7-2 depicts a block diagram capturing these layers onboard the ship and their interconnection to shore-based networks. This representation aligns closely with the MiTS architecture schematic, emphasizing the system-of-systems nature and the critical role of standardized communication and data function integration.
While the ship and shore systems operate as a tightly coupled system-of-systems (SoS), each individually operates with a defined purpose (navigation, propulsion control, cargo handling onboard; fleet management, logistics, compliance ashore). Together, their interactions create behavior and capabilities greater than their parts, enabling coordinated decision-making and optimization across extended maritime operational domains.
The architecture also shows real-time, bidirectional communications enabling continuous feedback loops. For example:
- Onboard sensors and control systems generate data sent ashore for condition monitoring and predictive maintenance.
- Shore-based operators analyze data streams and send back optimized route changes, software updates, or emergency commands to the vessel.
This dynamic interconnection supports adaptive operations but also creates vulnerabilities where failures or cyber events in one domain can cascade across the whole SoS.
The MiTS architecture also supports seamless data exchange and operation between the ship’s onboard systems and shore-based support facilities, thus enabling remote monitoring, operational control, situational awareness, and compliance management. The interplay of shipboard and shore ICT systems yields distinct emergent behaviors and properties:
- System-of-Systems Complexity: The marine domain functions as a distributed network of autonomous yet interdependent subsystems. Individually optimized vessel systems (navigation, propulsion, cargo) gain extended operational and safety capabilities when integrated with shoreside decision centers, logistics hubs, and regulatory authorities.
- Dynamic Feedback and Adaptation: Continuous, bidirectional data flows create real-time feedback loops. Ships relay sensor and performance data, which informs shore-based predictive maintenance and voyage optimizations; shoreside commands and alerts guide vessel operations, potentially modifying course or system states.
- Heterogeneous Technologies and Protocols: The coupling of various physical media, communication protocols, and service standards creates complexity in interoperability and system assurance. Managing standardization while accommodating regional and vendor differences is an ongoing challenge.
- Resilience and Security as Emergent Properties: Cybersecurity threats, communication failures, or procedural lapses in either domain can cascade through the entire ecosystem, emphasizing resilience as a property that arises only through combined technical safeguards, organizational processes, and human factors coordination.
The ship-shore connection spans a wide diversity of communication technologies (satellite, VHF, AIS, 4/5G cellular) and protocols (industrial control networks, IP-based data networks, proprietary maritime messaging standards). This heterogeneity demands interoperability frameworks and complex data translation layers (partially addressed by evolving standards such as IHO S-100 for nautical information).
The integration introduces a new attack surface: cyber threats, intentional or accidental failures can propagate swiftly between ship and shore, risking operational safety and environmental harm. Resilience must thus be considered as an emergent property of the whole ICT ecosystem, requiring coordination across organizational, technical, and regulatory layers.
Technology interaction alone does not account for system behavior. Human operators, organizational procedures, and regulatory mandates interact with technical components in tight loops, shaping the overall system’s reliability and adaptability. For example, shore-based decision centers (Remote Operations Centers) monitor and support vessels but depend on stable connectivity and timely data for accurate situational awareness.
Tools for Student Further Exploration
For a practical understanding of these architectures and emergent phenomena, students are encouraged to engage with:
- The Open Simulation Platform[6] (OSP) offers open-source maritime system models and co-simulation frameworks. It enables practical exploration of complex system-of-systems integration, cyber-physical interactions, and network virtualization concepts.
- OpenCPN[7] (OCPN), a widely used open-source navigation software offering live AIS and chart plotting capabilities to explore real-time maritime communication data flows.
Core Challenges
The biggest challenge in shipboard communications for maritime transportation systems is maintaining robust, secure, and integrated connectivity across complex systems. These digitalized networks are highly vulnerable to cyber threats and operational disruptions. These can be summarized as:
Connectivity & Coverage: Ships travelling through remote ocean regions or polar routes often experience unreliable or limited network coverage, impacting navigation, reporting, and crew safety.
Cybersecurity Threats: Increasing digitalization and interconnected systems expose vessels to sophisticated cyberattacks, including AI-powered threats, ransomware, and operational technology vulnerabilities. Shipboard networks often lack full encryption and proactive defenses, making them prime targets.
Data Overload & Integration: Modern ships generate massive operational, safety, and navigation data, but managing and sharing it without overwhelming crews—or leaving critical gaps—is challenging. Integration with legacy systems complicates this further.
Environmental Conditions: Harsh marine weather (fog, ice, storms) disrupts both radio and digital signals, threatening real-time updates and emergency communications.
Bandwidth & Latency Limitations: Satellite links, despite advances, still suffer from limited bandwidth and significant latency, hampering real-time operations and diagnostics.
Addressing these challenges necessitates coordinated industry-wide strategies, substantial investment in resilient and secure technologies, and the advancement of regulatory frameworks to ensure that future shipboard communication systems are secure, efficient, and adaptable to the evolving demands of global maritime transportation. The following sections will examine a subset of the threats facing shipboard networks and the Global Maritime Distress and Safety System (GMDSS), alongside a concise overview of recent cybersecurity incidents that have impacted maritime communication infrastructures.
Shipboard Networks: Attacks and Defenses. As maritime vessels become increasingly digitized and interconnected through advanced shipboard networks, they face a growing array of cyber threats that target critical operational technology (OT) and information technology (IT) systems. These attacks—ranging from ransomware and malware infections to sophisticated state-sponsored intrusions—pose significant risks to navigation, propulsion, communication, and cargo management systems, jeopardizing both vessel safety and global supply chains. The complexity of shipboard network architecture, comprising legacy protocols, heterogeneous devices, and constrained satellite communications, creates vulnerabilities that adversaries actively exploit. Defensive strategies must therefore encompass multilayered cybersecurity measures, including network segmentation, real-time intrusion detection, rigorous access control, and continuous crew training to strengthen resilience against increasingly sophisticated cyberattacks. Understanding the evolving threat landscape and deploying adaptive defenses are essential to safeguarding maritime operations in today’s digital age.
Global Maritime Distress and Safety System (GMDSS)
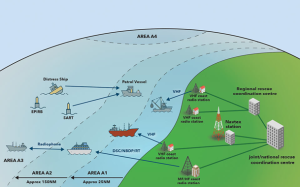
The Global Maritime Distress and Safety System (GMDSS) is a standardized system for maritime safety that is mandated by the International Maritime Organization (IMO) under the SOLAS (Safety of Life at Sea) convention. It delivers automated communication for distress alerts, search and rescue coordination, navigational warnings, and maritime safety information. The system operates using terrestrial and satellite networks, such as Inmarsat, Iridium, NAVTEX, Digital Selective Calling (DSC), and the Cospas-Sarsat satellite constellation.
Although GMDSS enables consistent communication for vessels in distress, its use of interconnected digital and radio systems may introduce vulnerabilities to cyber exploitation. Like other shipboard technologies, GMDSS components can be targeted for disruption, deception, or denial of service.

Technical Overview and Attack Vectors
GMDSS combines satellite communications, VHF/MF/HF radio, and digital alerting systems (see Figure 7-5). This configuration provides redundancy and increases the overall system’s exposure to potential threats. Potential vulnerabilities include:
- Signal Jamming and Interference: Adversaries may jam VHF or satellite uplinks, preventing distress signals from being transmitted to search and rescue authorities.
- Spoofed Alerts: The transmission of fraudulent digital selective calling (DSC) messages or false NAVTEX broadcasts can create fabricated distress calls, resulting in the misallocation of rescue resources and erosion of operational trust.
- Unauthorized Access: Inadequately protected terminals may be subject to remote access, which can lead to alarm deactivation, message suppression, or injection of malicious code.
- Supply Chain Weaknesses: Vulnerabilities stemming from compromised firmware or outdated software in satellite terminals or Enhanced Group Call (EGC) receivers may be exploited, disrupting critical communication continuity.
Real-World Incidents and Risks
Although few reported cyberattacks have directly targeted GMDSS, incidents involving GPS spoofing, AIS manipulation, and satellite jamming indicate the potential for such threats. For instance:
- Satellite Interference Events (Eastern Mediterranean, Black Sea, etc.): Multiple GPS interference incidents have been documented in the Eastern Mediterranean Sea, particularly near Cyprus, Port Said, the Suez Canal, and Jeddah, affecting navigation and communications systems—including satellite services. Such events demonstrate the vulnerability of space-based maritime systems like GNSS and potentially GMDSS components (2018-014-Eastern Mediterranean Sea-GPS Interference | MARAD, n.d.; ELECTRONIC INTERFERENCE IN MEDITERRANEAN, n.d.)
- False Distress Signals via VHF Spoofing: Documented cases exist of hoax distress calls being transmitted over VHF Channel 16, the designated emergency frequency. For instance, the U.S. Coast Guard has investigated several false Mayday transmissions in the Northeastern United States. These incidents have resulted in considerable expenditure of rescue resources and clearly illustrate the impact that false alarms, even those sent via analog means, can have on safety operations.
- Risks from IP-Enabled GMDSS Terminals (OT/IT Integration): As GMDSS adopts more advanced, networked setups, IP-enabled terminals are increasingly used on vessels. This shift brings potential vulnerabilities similar to those observed in IT/OT integrations, including remote exploits, malware introduced through removable media, and unauthorized access over networked systems.
Impact of a GMDSS Compromise

Given GMDSS’s central role in maritime safety, any breach could catalyze significant shifts in global compliance. A successful attack on GMDSS could have severe consequences:
Safety of Life
A disruption of GMDSS distress communications—whether via jamming, spoofing, or manipulation—could delay or prevent rescue efforts. Ships rely on digital distress alerts, such as EPIRB signals, DSC calls, and NAVTEX broadcasts, to automatically summon assistance. If these systems fail, crews must resort to slower, less reliable manual methods, putting lives at risk.
Moreover, a threat to COSPAS‑SARSAT and EPIRB systems has profound implications. Recent research has highlighted vulnerabilities in EPIRB protocols, including susceptibility to replay and spoofing attacks, suggesting that even satellite-based distress messaging can be compromised.
Operational Disruption
False distress alerts, such as those from spoofed DSC or EPIRB messages, can occupy the resources of Maritime Rescue Coordination Centers (MRCCs) and reduce their ability to respond to actual emergencies. Similarly, a denial‑of‑service attack caused by jamming GMDSS frequencies could prevent genuine alerts from being transmitted. While direct instances of such attacks on GMDSS are limited, analyses of maritime communications systems highlight potential risks. According to an industry advisory, integrating new technologies may increase vulnerabilities, and jamming or interference can disrupt emergency communications and affect operations.
Strategic Risk
In areas affected by conflict, adversaries may exploit vulnerabilities within the GMDSS to obscure ship positions or disrupt distress communications. For example, intentional interference or spoofing could be employed to mask vessel movements, thereby facilitating covert naval or commercial operations. While there are limited documented cases of direct attacks on the GMDSS, extensive research into maritime system vulnerabilities—including GNSS spoofing and related navigation system threats—demonstrates the potential for strategic manipulation of GMDSS components.
Reputational and Regulatory Consequences
If GMDSS systems are compromised, stakeholders may lose confidence in the reliability of international maritime safety mechanisms. This could trigger regulatory changes, demanding stricter cybersecurity frameworks across distress communication systems.
Research on maritime cybersecurity warns that attacks can erode trust, cause financial and operational damage, and necessitate revisions to standards and audits.
Mitigation and Defense Strategies
Building resilience into GMDSS requires both technical and procedural safeguards:
- Multi-layer Communications: Vessels and MRCCs should use alternative channels, such as HF radio, satellite, or AIS Safety-Related Messages, to verify alerts.
- Authentication and Encryption: Cryptographic verification of DSC and NAVTEX messages can mitigate spoofing; relevant standards are progressing toward these measures.
- Hardening Endpoints: Shipboard terminals can be secured by applying patches, enforcing access controls, and physically protecting control consoles.
- Redundancy and Drills: Regular testing of manual distress protocols and crew preparedness supports continued operations if automated GMDSS systems are disrupted.
- International Coordination: Information sharing regarding interference incidents and cyber threats among IMO, ITU, satellite providers, and flag states may be strengthened.
GMDSS plays a critical role in safeguarding lives at sea by providing worldwide, automated emergency communication capabilities. However, as the system transitions to next-generation IP-based infrastructures, it also becomes susceptible to cyber threats inherent in modern digital environments. The platform’s primary advantage—global interoperability—means that potential vulnerabilities can quickly affect multiple fleets and regions. Achieving cyber resilience within GMDSS is not solely a technical concern; it is a matter of the safety of life at sea. Maritime stakeholders need to recognize that protecting distress communication systems is equally vital as upholding vessel seaworthiness.
Case Study: The Maersk NotPetya Attack (2017)The 2017 NotPetya cyberattack on A.P. Moller–Maersk is considered a major event in maritime cybersecurity. Maersk, one of the world’s largest container shipping companies, operates on major trade routes with port terminals worldwide and has a digital fleet. The company’s reliance on integrated IT systems boosted operational efficiency but also heightened risk. The NotPetya incident highlighted the vital importance of cybersecurity in the maritime industry.

Background and Attack Vector
On June 27, 2017, NotPetya was deployed. Although it appeared to be ransomware, it functioned as a destructive wiper, with no mechanism for file recovery even upon payment of ransom. The initial infection vector was the compromised update process of MEDoc, an accounting software extensively used in Ukraine. As Maersk operated in Ukraine, it was among the initial organizations affected. Subsequently, the malware propagated rapidly within the company’s internal networks.
NotPetya leveraged leaked NSA tools EternalBlue and EternalRomance to exploit vulnerabilities within the Windows Server Message Block (SMBv1) protocol. Additionally, it used Mimikatz, a credential-harvesting utility, to enable lateral movement across networks. Insufficient network segmentation and the use of shared credentials contributed to its rapid spread, leading to widespread system disruptions on a global scale.
Technical Behavior and Systems Affected
Unlike traditional ransomware, NotPetya encrypted the master boot record (MBR), rendering systems inoperable and causing a complete loss of functionality. The malware was designed for rapid dissemination, scanning both local and remote networks to identify and exploit vulnerable endpoints.
Maersk experienced significant repercussions as a result. Terminal operating systems, email servers, ERP platforms, and vessel management systems were all affected. This led to the suspension of port activities, breakdown of customs clearance, and failure of automated scheduling. While manual procedures were implemented as a contingency, they were insufficient to manage the demands of global container logistics.
Operational and Financial Impact
The incident had a considerable impact. Maersk’s global operations experienced several days of disruption, affecting seventy-six ports worldwide. As a result, vessel schedules were delayed, cargo processing was hindered, and overall supply chain timelines were compromised.
Financial losses are estimated to be between $200 million and $300 million; however, the reputational damage and exposure of systemic vulnerabilities may have had even more significant implications. According to the Columbia University case study, the estimated cost was approximately $1 billion. This event highlighted how a single cyber incident can have far-reaching effects on the global economy, serving as a key example of supply chain vulnerability.
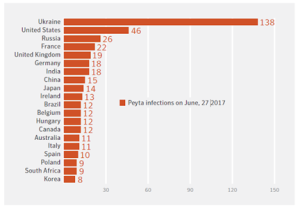
Response and Recovery
Maersk initiated its crisis response by isolating its network to impede the spread of malware. Collaborating with leading cybersecurity firms such as Microsoft, the company proceeded to analyze the malware and devise effective countermeasures.
The recovery process required the reinstallation of thousands of servers and endpoints. Following the compromise or inaccessibility of many backups, Maersk depended on a domain controller located in Ghana that remained intact due to an unexpected power outage. The incident began when NotPetya impacted Maersk’s global IT infrastructure, erasing both servers and backups. A notable aspect of the recovery was the preservation of a single domain controller (DC) in Ghana. Within Microsoft Active Directory environments, a DC is essential for user authentication, security policy enforcement, and managing access credentials. The absence of at least one DC makes restoring enterprise IT systems impossible. This particular controller survived because it was offline during the attack due to a local power interruption, which inadvertently protected it from the malware. Upon restoration of power, Maersk used this domain controller to reconstruct its entire Active Directory environment globally, establishing a foundation for reinstating authentication and access controls throughout the organization.
This event exposed both the robust and vulnerable aspects of Maersk’s contingency plans.
In the aftermath of the attack, Maersk strengthened its patch management protocols, implemented network segmentation, and broadened its incident response capabilities. These actions were designed to mitigate future risks and enhance organizational resilience.
The NotPetya malware incident highlighted the significance of timely patching. The attack exploited unpatched SMB (Server Message Block) vulnerabilities (notably EternalBlue) for which Microsoft had already provided updates months earlier. SMB is a network file-sharing protocol built into Microsoft Windows. It lets computers on a network share files, printers, and other resources. For example, if one computer on a company network accesses a shared folder on another, that connection often uses SMB. Following this event, Maersk revised its patch management procedures to prevent similar oversights. This revision involved implementing centralized patch management systems that could automatically test and deploy updates across servers and endpoints.
Additionally, risk-based prioritization was introduced, ensuring that vulnerabilities with active exploits or high exploitability were patched immediately, regardless of regular maintenance schedules. Regular patch audits and compliance tracking were also established to confirm that updates were applied consistently throughout global operations. These changes shifted Maersk’s approach from a reactive and fragmented process to a more structured and proactive patch management lifecycle, aligning with enterprise security best practices.
Maersk began strengthening its implementation of network segmentation after NotPetya’s propagation exploited a flat network design, where many IT systems were interconnected with limited internal separation. This structure enabled the malware to move laterally across regions, business units, and functional areas. In response, Maersk introduced network segmentation by dividing its network into smaller, isolated zones based on function and sensitivity. For instance, operational technology (OT), such as vessel management systems, was previously separated from enterprise IT systems, including email and Enterprise Resource Planning (ERP). Segmentation within IT included regional networks, terminals, and business-critical applications. Firewalls, VLANs, and access control lists were deployed to strictly regulate traffic between these zones, while the principle of least privilege allowed only essential communications. As a result, a breach in one segment could be contained and prevented from spreading widely throughout the organization.
Lessons Learned
Several enduring lessons emerged from this event:
- Patch Management – Delays in addressing known vulnerabilities significantly contributed to the propagation of NotPetya. This attack could have been prevented if patches had been applied as soon as they were published.
- Network Segmentation – The absence of segmented networks allowed the malware to move laterally without restriction.
- Preparedness and Backups – While Maersk achieved recovery, this incident highlighted the necessity of well-practiced incident response plans and robust backup strategies.
- Supply Chain Risk – The infection via MEDoc illustrated the increasing risks associated with software supply chain compromises.
- Human Awareness – Maintaining vigilance against credential misuse and phishing remains essential to reducing organizational attack surfaces.·
Industry-Wide Impact
In addition to the impact on Maersk, the NotPetya incident elevated maritime cybersecurity to a matter of board-level importance. The International Maritime Organization (IMO) expedited its development of guidelines for managing cyber risks, prompting shipping companies globally to review and strengthen their defense-in-depth approaches. Practices such as thorough supplier vetting, rigorous patch management, and enhanced cybersecurity hygiene have become fundamental to industry standards.
IMO took the following actions and guided after the NotPetya attack:
- Adoption of Formal Cyber Risk Management Guidelines (2017–2018): In the wake of the NotPetya attack, the IMO recognized the growing risk that cyber incidents pose to maritime safety. In July 2017, the IMO’s Maritime Safety Committee adopted Resolution MSC.428(98), which called for cyber risks to be addressed within existing Safety Management Systems under the ISM Code. IMO also published Guidelines on Maritime Cyber Risk Management (MSC-FAL.1/Circ 3), offering high-level recommendations for integrating cyber risk management into the daily operations of ships and shore facilities (IMO, 2018)
- Integration into Safety Management Systems (Ongoing Implementation): These guidelines are currently the only comprehensive maritime cybersecurity regulation that is enforceable worldwide. They guide administrators and operators in incorporating cyber risk management into their safety protocols and operational rules—effectively making cybersecurity a part of maritime “seaworthiness” standards. (n.d.-a)
- Updated Guidance with Greater Specificity (2023–2025): Building on the initial framework, the IMO issued enhanced cyber risk guidance in mid-2025. This iteration expanded expectations significantly:
o Companies must conduct regular cyber risk assessments for both shipboard and shore systems.
o They must develop and exercise incident response plans.
o It mandates scrutiny of third-party vendors and their cyber posture.
o It requires training of crew and shore staff on cyber hygiene, phishing awareness, and system integrity.
o These updates are designed to be integrated into the Safety Management Systems outlined in the ISM Code. The IMO strongly recommends that shipping operators meet these standards by 2025, aligning with SMS audit cycles.

This pivotal event underscored the fact that cybersecurity within maritime operations extends beyond traditional IT concerns, representing a crucial aspect of global trade security. NotPetya thus functioned both as a warning and as a catalyst that drove significant systemic change throughout the sector.
These IMO directives effectively elevated maritime cybersecurity to the level of board and regulatory importance. They required shipping companies and regulators to:
- Integrate cybersecurity into core safety management processes,
- Require supplier/vendor vetting and cybersecurity readiness,
- Implement rigorous patch management as part of risk assessment and system resilience.
- Improve cyber hygiene training for both crew and shore-based staff.·
Summary
The Maersk NotPetya incident underscores the substantial risks that cyberattacks pose to critical infrastructure. In addition to causing significant financial losses for an individual company, this event emphasized the importance of the shipping industry to prioritize cyber resilience alongside physical safety and seaworthiness. The lessons learned from this incident continue to shape maritime policy, refine incident response protocols, and guide investment in digital security measures. Notably, this incident may have been avoided had the affected systems been updated with vulnerability patches released by Microsoft prior to the attack.
Impact of Emerging Technologies
Emerging technologies are profoundly reshaping maritime ICT, offering unprecedented capabilities while introducing new cybersecurity and operational challenges.
Satellite Communications enable real-time, high-throughput data transmission from ships to shore and cloud platforms, facilitating advanced analytics, remote vessel control, and fleetwide coordination. However, this connectivity broadens the attack surface for SCADA and related systems, raising risks if effective network segmentation and security controls are not implemented.
The rollout of 5G /6G technologies promises ultra-low latency and massive IoT sensor connectivity onboard, supporting next-generation workflows such as predictive maintenance and remote operation. Yet, these advances increase exposure if IoT devices and gateways lack stringent authentication, access control, and patch management.
AIS (Automatic Identification System) integration with SCADA enhances navigation and vessel tracking but is vulnerable to spoofing and manipulation, potentially causing critical misdirection or concealment of illicit activities.
IoT Platforms proliferate environmental, machinery, and crew monitoring sensors, from environmental sensors to engine vibration, cargo conditions, and crew wearables, multiplying potential cyber entry points and necessitating robust endpoint security.
Role of SDN, Network Virtualization, and Cloud Computing
Software Defined Networking (SDN) separates the control plane (network decision-making) from the data plane (actual packet forwarding), enabling centralized, programmable network management through software controllers. This flexibility facilitates dynamic network configuration, resource optimization, and enhanced fault tolerance — all critical for complex maritime environments where adaptability is key. With Network Virtualization, creating multiple virtual networks (slices) over a shared physical infrastructure, network virtualization supports isolating critical OT/SCADA traffic from general IT or IoT traffic. This isolation improves control and security but requires sophisticated management. SDN and network virtualization introduce sophisticated capabilities to centrally and programmatically manage dynamic maritime networks, isolating OT, IT, and IoT traffic for enhanced security and fault tolerance.
SDN and virtualized networks can dynamically adapt shipboard network topologies, enabling efficient segregation of OT (SCADA, machinery control), IT (crew and administration), and IoT (sensors, devices) traffic, minimizing attack surface overlaps. These technologies support mixed connectivity environments like satellite, 5G/6G, and traditional radio networks in shipboard communications, creating a more manageable and resilient fabric.
However, the complexity of hybrid satellite, radio, and terrestrial links requires distributed SDN architectures to manage latency, reliability, and resilience challenges. At the same time, centralized SDN controllers must be secured under zero-trust paradigms to prevent compromise. Cloud-based network and SCADA management promise orchestration and agility, but at the cost of creating high-value attack targets and vulnerability to connectivity disruption; hybrid edge-cloud models balancing local autonomy and remote control are essential for operational resilience. This multifaceted technological convergence demands comprehensive cybersecurity frameworks, continuous monitoring, and adaptive access policies to maintain safe and resilient maritime ICT ecosystems amid evolving threat landscapes.
Maritime environments face heterogeneous, multi-domain infrastructures combining satellite, maritime radio, and terrestrial links, demanding distributed and hierarchical SDN architectures to cope with latency variability and resilience needs.
SDN /NFV (Network function virtualizations) centralized control paradigms promoted in cloud-based network management can introduce security risks if controllers are compromised or connectivity to them is lost. Distributed trust models and zero-trust architectures are needed to secure these control layers.
Cloud-centric network management promises simplified orchestration, rapid deployment, and unified control of shipboard networks and SCADA systems. However:
- Security Risks: Centralization creates high-value attack targets; a breach in cloud controllers or management platforms could cascade severe impacts to shipboard OT/IT networks.
- Connectivity Dependence: Shipboard networks often rely on intermittent and bandwidth-limited satellite links. Overdependence on cloud control can lead to degraded network control or failures if these links experience disruption.
- Data Privacy and Sovereignty: Transmitting sensitive operational and control data offshore to cloud providers raises compliance and trust issues, critical in regulated maritime environments.
Potential Mitigation Strategies include:
- Hybrid control models combining localized network control with cloud orchestration can balance resilience and agility.
- Encryption, strong authentication, and anomaly detection must be embedded both onboard and in cloud management platforms.
- Policies enforcing least privilege and segmented access to cloud and shipboard resources reduce risks.
Conclusions
This chapter promotes a systems-thinking perspective on shipboard communication by encouraging students to view maritime technologies through the lenses of Cyber-Physical Systems (CPS), Socio-Technical Systems (STS), and enterprise systems. It emphasizes how the convergence of Information Technology (IT), Operational Technology (OT), and the Internet of Things (IoT) gives rise to deeply interconnected systems—where physical operations, digital infrastructure, and human decision-making are inseparably linked. Within this context, maritime communication systems function as System-of-Systems (SoS), in which secure and resilient communication depends on recognizing and understanding the complex interplay across technical and socio-organizational dynamics. Through case studies and threat analyses, the chapter identifies how vulnerabilities—ranging from linguistic factors, legacy protocols, and inadequate authentication to procedural lapses—manifest across these interdependent layers.
This framing leads to a central realization: modern maritime systems are connected, inherently complex, and therefore increasingly compromised. Recognizing this triad is essential for developing security strategies that reflect the realities of contemporary shipboard environments. Students are challenged to move beyond compartmentalized thinking and embrace a holistic, integrated approach to system design, risk management, and maritime operational governance.
References
2018-014-Eastern Mediterranean Sea-GPS Interference | MARAD. (n.d.). Retrieved September 2, 2025, from https://www.maritime.dot.gov/msci/2018-014-eastern-mediterranean-sea-gps-interference
admin. (2019, December 25). GMDSS (Equipment and Procedures). Knowledge Of the Sea. https://knowledgeofsea.com/gmdss-equipments-and-procedures/
Akpan, F., Bendiab, G., Shiaeles, S., Karamperidis, S., & Michaloliakos, M. (2022). Cybersecurity Challenges in the Maritime Sector. Network, 2(1), 123–138. https://doi.org/10.3390/network2010009
Alcaide, J. I., & Llave, R. G. (2020). Critical infrastructures, cybersecurity, and the maritime sector. Transportation Research Procedia, 45, 547–554. https://doi.org/10.1016/j.trpro.2020.03.058
AMPLYFI. (2025, May 26). CTIME Analysis: Comprehensive Review of Maritime Cybersecurity Vulnerabilities. AMPLYFI. https://amplyfi.com/blog/ctime-analysis-comprehensive-review-of-maritime-cybersecurity-vulnerabilities/
Androjna, A., Brcko, T., Pavic, I., & Greidanus, H. (2020). Assessing Cyber Challenges of Maritime Navigation. Journal of Marine Science and Engineering, 8(10), 776. https://doi.org/10.3390/jmse8100776
Ben Farah, M. A., Ukwandu, E., Hindy, H., Brosset, D., Bures, M., Andonovic, I., & Bellekens, X. (2022). Cyber Security in the Maritime Industry: A Systematic Survey of Recent Advances and Future Trends. Information, 13(1), 22. https://doi.org/10.3390/info13010022
Brcko Satler, T., & Jurkovič, V. (2024). Solving maritime communication challenges with Digimar: A practical approach. 10. https://doi.org/10.5821/mt.12873
Bronk, C., & deWitte, P. (2022). Maritime Cybersecurity: Meeting Threats to Globalization’s Great Conveyor. In M. Lehto & P. Neittaanmäki (Eds.), Cyber Security: Critical Infrastructure Protection (pp. 241–254). Springer International Publishing. https://doi.org/10.1007/978-3-030-91293-2_10
Cruise Ship Safety. (2015, November 26). CruiseMapper. https://www.cruisemapper.com/wiki/751-cruise-ship-safety
Diaz, R., Smith, K., Bertagna, S., & Bucci, V. (2023). Digital Transformation, Applications, and Vulnerabilities in Maritime and Shipbuilding Ecosystems. Procedia Computer Science, 217, 1396–1405. https://doi.org/10.1016/j.procs.2022.12.338
ELECTRONIC INTERFERENCE IN THE MEDITERRANEAN. (n.d.). Shipping.Nato.Int. Retrieved September 2, 2025, from https://shipping.nato.int/nsc/operations/news/2019/electronic-interference-in-mediterranean.aspx
Ellingsen, O., & Aasland, K. E. (2019). Digitalizing the maritime industry: A case study of technology acquisition and enabling advanced manufacturing technology. Journal of Engineering and Technology Management, 54, 12–27. https://doi.org/10.1016/j.jengtecman.2019.06.001
GMDSS for Vessel Operators: Challenges & Solutions. (n.d.). Limitac. Retrieved September 2, 2025, from https://www.lmitac.com/articles/implementing-gmdss-challenges-for-vessel-operators
Hagen, J. E., et al. (2011). DEVELOPMENT OF AN E-NAVIGATION STRATEGY IMPLEMENTATION PLAN (Report of the Working Group No. NAV 57/WP.6; p. 17). International Maritime Organization (IMO). https://docs.iho.int/mtg_docs/com_wg/CPRNW/S100_NWG/2014/NAV_57-WP.6.pdf
IMO Standard Marine Communication Phrases. (n.d.). Retrieved September 3, 2025, from https://www.imo.org/en/ourwork/safety/pages/standardmarinecommunicationphrases.aspx
IMSO – What is the GMDSS? (n.d.). IMSO. Retrieved September 3, 2025, from https://imso.org/our-work/gmdss/what-is-the-gmdss/
Inmarsat. (2020). Inmarsat Global Government Maritime Case Studies. https://www.inmarsat.com/content/dam/inmarsat/corporate/documents/government/solutions-services/Inmarsat_Global_Government_Maritime_Case_Studies_August_2020_EN.pdf.coredownload.inline.pdf
Jurkovič, V., & Satler, T. B. (2025). Advancing navigational safety: Digimar’s project focuses on routine maritime communication. Transportation Research Procedia, 83, 349–356. https://doi.org/10.1016/j.trpro.2025.02.046
Li, M., Zhou, J., Chattopadhyay, S., & Goh, M. (2024). Maritime Cybersecurity: A Comprehensive Review (No. arXiv:2409.11417). arXiv. https://doi.org/10.48550/arXiv.2409.11417
Machaka, V., Figueroa-Lorenzo, S., Arrizabalaga, S., Elduayen-Echave, B., & Hernantes, J. (2025). Assessing the impact of Modbus/TCP protocol attacks on critical infrastructure: WWTP case study. Computers and Electrical Engineering, 126, 110485. https://doi.org/10.1016/j.compeleceng.2025.110485
Mednikarov, B., Tsonev, Y., & Lazarov, A. (2020). Analysis of Cybersecurity Issues in the Maritime Industry. Information & Security: An International Journal, 47(1), 27–43. https://doi.org/10.11610/isij.4702
Meland, P. H., Bernsmed, K., Wille, E., Rødseth, Ø. J., & Nesheim, D. A. (2021). A Retrospective Analysis of Maritime Cyber Security Incidents. TransNav, International Journal on Marine Navigation and Safety Od Sea Transportation, 15(3), 519–530. https://doi.org/10.12716/1001.15.03.04
Mileski, J., Clott, C., & Galvao, C. B. (2018). Cyberattacks on ships: A wicked problem approach. Maritime Business Review, 3(4), 414–430. https://doi.org/10.1108/MABR-08-2018-0026
MiTS – Maritime Information Technology Standard. (n.d.). Retrieved September 2, 2025, from https://www.mits-forum.org/architecture.html#ENAV
Murray, G., Johnstone, M., & Valli, C. (2017). The convergence of IT and OT in critical infrastructure. Australian Information Security Management Conference. https://doi.org/10.4225/75/5a84f7b595b4e
Network, M. N. (2019, September 18). Real Life Incident: Loss Of Power And Inadequate Communication Leads To Grounding. Marine Insight. https://www.marineinsight.com/case-studies/real-life-incident-loss-of-power-and-inadequate-communication-leads-to-grounding/
Nganga, A., Nganya, G., Lützhöft, M., Mallam, S., & Scanlan, J. (2023). Bridging the Gap: Enhancing Maritime Vessel Cyber Resilience through Security Operation Centers. Sensors, 24(1), 146. https://doi.org/10.3390/s24010146
Niknami, N., Srinivasan, A., St. Germain, K., & Wu, J. (2023). Maritime Communications—Current State and the Future Potential with SDN and SDR. Network, 3(4), 563–584. https://doi.org/10.3390/network3040025
Radiocommunications for keeping ships and people safe at sea. (n.d.). ITU. Retrieved September 3, 2025, from https://www.itu.int:443/en/mediacentre/backgrounders/Pages/Radiocommunications-for-keeping-ships-and-people-safe-at-sea.aspx
Raymaker, A., Kumar, A., Wong, M. Y., Pickren, R., Chhotaray, A., Li, F., Zonouz, S., & Beyah, R. (2025). A Sea of Cyber Threats: Maritime Cybersecurity from the Perspective of Mariners. https://doi.org/10.1145/3719027.3744816
Reports, M. (2019, April 1). Real Life Incident: Lack of Communication Leads To a Close Quarters Situation Between Two Vessels. Marine Insight. https://www.marineinsight.com/case-studies/close-quarters-situation-between-two-vessels/
SCENARIOS – Digi Mar – Digital Education for Maritime Communication. (n.d.). Retrieved September 2, 2025, from https://digimar.si/category/scenarios/
Schäfer, G., Waclawek, H., Riedmann, S., Binder, C., Neureiter, C., & Huber, S. (2024). IT/OT Integration by Design. INCOSE International Symposium, 34(1), 337–352. https://doi.org/10.1002/iis2.13150
Symes, S., Blanco-Davis, E., Graham, T., Wang, J., & Shaw, E. (2024). Cyberattacks on the Maritime Sector: A Literature Review. Journal of Marine Science and Application, 23(4), 689–706. https://doi.org/10.1007/s11804-024-00443-0
Tijan, E., Jović, M., Aksentijević, S., & Pucihar, A. (2021). Digital transformation in the maritime transport sector. Technological Forecasting and Social Change, 170, 120879. https://doi.org/10.1016/j.techfore.2021.120879
Top IoT Protocols in Maritime: LoRa, NB-IoT & Satellite Mesh. (n.d.). Https://Sinay.Ai/. Retrieved September 2, 2025, from https://sinay.ai/en/maritime-iot-protocol-wars-lora-vs-nb-iot-vs-satellite-mesh-in-real-world-deployments/
Tucci, A. E. (2017). Cyber Risks in the Marine Transportation System. In R. M. Clark & S. Hakim (Eds.), Cyber-Physical Security: Protecting Critical Infrastructure at the State and Local Level (pp. 113–131). Springer International Publishing. https://doi.org/10.1007/978-3-319-32824-9_6
Xia, T., Wang, M. M., Zhang, J., & Wang, L. (2020). Maritime Internet of Things: Challenges and Solutions. IEEE Wireless Communications, 27(2), 188–196. https://doi.org/10.1109/MWC.001.1900322
Endnotes
[1] We use maritime vessels and ships interchangeably
[2] The report is available at https://digimar.si/wp-content/uploads/2025/03/3-Vessel-Grounding-Caused-by-Communication-Breakdown.pdf
[3] The report is available at https://digimar.si/wp-content/uploads/2025/02/2-Near-miss-due-to-Miscommunication.pdf
[4] The report is available at https://upcommons.upc.edu/bitstreams/b50e24ec-5094-40fe-9f42-60355511666b/download
[5] The report is available at https://www.inmarsat.com/content/dam/inmarsat/corporate/documents/government/solutions-services/Inmarsat_Global_Government_Maritime_Case_Studies_August_2020_EN.pdf.downloadasset.pdf
[6] OSP is available at https://opensimulationplatform.com with its free open source repository at https://open-simulation-platform.github.io, providing open-source ship system co-simulation models and IT /OT integration frameworks
[7] OpenCPN (OCPN) is available at https://opencpn.org. It provides a freely accessible marine navigation software platform, allowing students to engage with real-time chart plotting, AIS data, and vessel tracking, connecting theory with practical navigation and communication system usage
[1] The report is available at https://digimar.si/wp-content/uploads/2025/03/3-Vessel-Grounding-Caused-by-Communication-Breakdown.pdf
[2] The report is available at,https://digimar.si/wp-content/uploads/2025/02/2-Near-miss-due-to-Miscommunication.pdf
[3] The report is available at ttps://upcommons.upc.edu/bitstreams/b50e24ec-5094-40fe-9f42-60355511666b/download
