9 Anti-Piracy Countermeasures (Mumm & Malhotra)
Abbreviations
ADS – Active Denial System
AIS – Automatic Identification Systems
BCE – Before Common Era
DID – Decentralized Identifier
GPS – Global Positioning Satellite
IMO – International Maritime Organization
IoT – Internet of Things
LRADS – Long-Range Acoustic Device
MARAD – Maritime Administration
MARSUR – Maritime Surveillance project
OS – Operating System
OT – Operational Technologies
OTA – Over the Air
UNCLOS – United Nations Convention on the Law of the Sea
Student Learning Objectives
The student will gain knowledge of the concepts and frameworks related to historical, current, and future trends in maritime piracy, as well as tactics and techniques to counter piracy activities. This discussion will include the motivations of the pirates and terrorist organizations as they create logistics processes to learn, adapt, and survive in the new era of maritime piracy. This chapter will explore the technological trends that have transformed piracy into a modern-day enterprise, as well as possible solutions to counter this threat to cargo ships, cruise ships, and military vessels.
The Evolution of Maritime Piracy
Maritime piracy has been a persistent threat to seafarers, traders, and empires since the earliest days of human navigation—the earliest records of maritime piracy date back to the 14th century BCE in the Mediterranean Sea. The Sea Peoples, a confederation of naval raiders, disrupted trade and contributed to the collapse of several Bronze Age civilizations, including the Hittite Empire and Mycenaean Greece (Cline, 2021).
Although romanticized in literature and film, piracy is a violent and disruptive crime that has shaped international trade, naval warfare, and maritime law for millennia. The romanticized adventures of pirates have been captured in paintings and on film, as seen in Hollywood movies such as Pirates of the Caribbean.

Piracy has a rich history from its ancient origins through the so-called “Golden Age of Piracy” to the modern resurgence of piracy off the coasts of Somalia and Southeast Asia. Anti-piracy efforts will be explored through the lens of contemporary international efforts to combat piracy and enforce maritime security. Vikings at that time “represent (ed) a form of organized maritime plunder that targeted monasteries, coastal towns, and ships throughout Europe. Vikings were both feared and respected for their seafaring abilities and played a significant role in shaping maritime warfare and trade in Northern Europe” (Konstam, 2011).
Notorious pirates from the Golden Age include Edward Teach (also known as Blackbeard), Bartholomew Roberts, and Anne Bonny. Blackbeard’s “fearsome appearance struck terror into the hearts of those unlucky enough to cross his path. Blackbeard’s career reached its zenith between 1716 and 1718” (Staff, 2023). These pirates attempted to organize and establish a semi-democratic code of conduct aboard their ships. They occasionally created pirate havens, such as Nassau, Bahamas, which operated as a quasi-autonomous pirate republic (Rediker, 2011). Historical artifacts that have been found from the 18th century offer a “glimpse they give of both the everyday pastimes on board a pirate ship, and the surprisingly nuanced political systems the pirates developed to maintain order and secure stable governance on their voyages” (Steven, 2021). These pirate communities organized colonies that challenged European colonial powers and disrupted the flow of colonial wealth and influence.

Governments responded by increasing naval patrols and anti-piracy legislation. The British, for example, began trying pirates in Admiralty Courts and executing them publicly to deter would-be buccaneers. The British 1717 “Act for the More Effectual Suppression of Piracy” (Konstam, 2011) authorized the use of force and incentivized the capture of pirates. Throughout the 1720s, “pirates were increasingly hunted down, bringing the ‘golden age’ to an end. Naval power was deployed to intercept pirate ships and bring crews to harsh justice” (Greenwich, 2025).
Contrary to the belief that piracy is a relic of the past, the 21st century has seen a troubling resurgence. The collapse of central governments and poverty have created fertile ground for modern piracy, particularly off the coast of Somalia. Somali pirates began targeting vessels in the Gulf of Aden and Indian Ocean in the early 2000s, using small skiffs to approach and hijack commercial ships, demanding millions of dollars in ransom. The 2009 hijacking of the MV Maersk Alabama, dramatized in the film Captain Phillips, brought global attention to this crisis.

Unlike their historical counterparts, modern pirates are driven less by ideology and more by economic desperation and organized crime. However, the impact on international trade has been significant. Elsewhere in Southeast Asia, particularly in the Strait of Malacca, piracy remains a persistent issue. Regional cooperation among littoral states has helped reduce incidents; however, challenges persist due to political instability, corruption, and inadequate enforcement capacity. In response, international coalitions, such as Combined Task Force 151, have launched naval patrols and implemented security protocols, including the deployment of onboard armed guards and the provision of convoy escorts (Bueger, 2015).
Anti-Piracy and The Challenges to the Worldwide Maritime Industry
Maritime piracy involves criminal acts committed at sea, including armed robbery, hijacking, and kidnapping. Historically romanticized, modern piracy is a highly organized and violent enterprise, often involving transnational criminal networks. Modern piracy is addressed under international law, particularly the United Nations Convention on the Law of the Sea (UNCLOS), which defines piracy and establishes international jurisdiction for prosecuting those who commit this offense. Article 101 of UNCLOS stipulates that piracy consists of any of the following acts:
(a) any illegal acts of violence or detention, or any act of depredation, committed for private ends by the crew or the passengers of a private ship or a private aircraft, and directed:
(i) on the high seas, against another ship or aircraft, or persons or property on board such ship or aircraft.
(ii) against a ship, aircraft, persons, or property in a place outside the jurisdiction of any State.
(b) any act of voluntary participation in the operation of a ship or of an aircraft with knowledge of facts making it a pirate ship or aircraft.
(c) any act of inciting or of intentionally facilitating an act described in subparagraph (a) or (b).
(United Nations Convention on the Law of the Sea – Part VII, 1982)
If law enforcement is successful in arresting pirates, prosecuting them remains a challenge. Jurisdictional limitations, lack of evidence, and weak legal systems in some countries hinder enforcement. The UN Security Council has passed several resolutions urging states to prosecute piracy, yet many captured pirates have been released without trial due to legal complexities.
Over the years, various technologies have been employed to counter piracy. The range of tools used to thwart pirates includes the simplistic use of a ship’s fire hose to the more sophisticated radar tracking of pirates. Ship captains must be able to harden all of their defenses before the pirates get close. Captains can call in additional naval forces, security personnel, and authorities as needed for assistance before any physical engagement.
The deployment of multinational naval task forces has been effective in reducing piracy. For instance, NATO’s Operation Ocean Shield and the EU’s Operation Atalanta played crucial roles in deterring Somali pirates. The Combined Task Force 151, established by the Combined Maritime Forces, conducts counter-piracy operations and fosters regional cooperation.
The “46 nations that comprise Combined Maritime Forces (CMF) are not bound by either a political or military mandate… Contributions can vary from the provision of a liaison officer at CMF HQ in Bahrain to the supply of warships or support vessels in task forces, and maritime reconnaissance aircraft based on land.” (Combined Maritime Forces: CTF 151, 2025). Shipping companies that leverage technologies such as satellite surveillance, Automatic Identification Systems (AIS), and maritime domain awareness platforms can enhance their threat detection capabilities. Initiatives such as the European Union’s Maritime Surveillance project (MARSUR) and the Indian Ocean Regional Maritime Information Fusion Center facilitate the sharing of real-time information. Satellite surveillance and other tracking activities are part of the Maritime Situational Awareness (MSA), which “is the effective understanding of activities associated with and occurring in the maritime domain that could impact the security, safety, and environment of the European Union and its Member States.” (Maritime Surveillance MARSUR, 2025). The vastness of the world’s oceans and waterways poses a significant challenge in tracking ships, deciphering their intentions, and identifying signs of piracy in time to prevent attacks and enable ships to reach their intended ports. The MSA offers a way to “improve the common “Recognised Maritime Picture” by facilitating exchange of operational maritime information and services such as ship positions, tracks, identification data, chat, or images.” (Maritime Surveillance MARSUR, 2025).
A robust global response is vital to address the complex challenges facing the maritime domain. The international shipping industry has responded by strengthening regional maritime security, enhancing legal and institutional frameworks, creating technological innovations and data sharing, leveraging satellite surveillance, Automatic Identification Systems (AIS), and maritime domain awareness platforms.
Even with all of these anti-piracy efforts from the United States and its’ allies, the world is still struggling to deal with the pirate issue, as “pirate activity on the high seas continues to be a problem: it is estimated that piracy can cost the US maritime industry up to $16 billion every year.” (David, 2015). The US Navy in 2015 filed a patent application for “a method for predicting pirate attack risk… based on intel regarding pirates”, and it might one day help its ships recognise a threat ahead of time (David, 2015). This AI-based approach combines historical, weather, and tactics data. “The model used for the pirate problem is based on a prey/predator game with a learned hunting model for a pirate group as predator.” (David, 2015).

Efforts to combat piracy have undergone significant evolution over the past two decades, including naval patrols, onboard security measures, international legal frameworks, and technological innovations.
The maritime industry is vital to the global economy’s functioning; however, it remains vulnerable to a range of threats, including piracy, geopolitical tensions, cyber risks, and environmental challenges. Climate change and natural hazards are also causing a shift in shipping lanes, as well as piracy attack locations. Rising sea levels, extreme weather events, and shifting ocean patterns all impact shipping routes and port infrastructure. Hurricanes, typhoons, and tsunamis disrupt supply chains and damage assets. The industry must adapt through resilient design, improved forecasting, and insurance coverage.
Although many anti-piracy measures have achieved notable successes in the past, the evolving nature of maritime threats demands continuous adaptation and international collaboration. Continuing to strengthen legal frameworks, investing in technology, and prioritizing human security are essential for securing the seas and ensuring the resilience of global maritime trade.
Piracy Today: Are We Gaining Ground?
According to Statista Research Department, “In 2024, the number of pirate attacks against ships worldwide decreased compared with the previous year. While 120 ships were attacked by pirates in 2023, the number of ships attacked dropped to 116 in 2024.” (Number of pirate attacks against ships worldwide from 2010 to 2024, 2025).
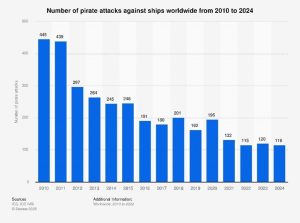
Although this report may initially give the reader the impression that the world is making progress against maritime piracy, it does not tell the whole story. Despite a decrease in attacks and piracy, on April 12, 2025, WorldPorts.org reported that the ICC International Maritime Bureau (IMB) is reporting the rise of “global piracy and armed robbery incidents in the first quarter of 2025. A total of 45 cases of piracy and armed robbery against ships were recorded in the first three months of 2025 – an almost 35% increase compared to the same period in 2024.” (Alexa, 2025).
Larger ships are now transporting enormous amounts of goods in a single trip, making these vessels a lucrative target. Pirates can capture one ship and have the ill-gotten gains of several smaller boats from past days in the industry. The size of these ships is driven by supply and demand from the rapid growth of commerce, changes in ports, canals, and shipbuilders, in an attempt to respond to the demand. In May of 2021, the Panama Canal Authority (PCA) “formally increased the maximum length and beam for ships passing through the waterway to 1,215 feet long and 168.14 feet wide. The previous maximums were 1,205 feet and 161 feet, respectively.” (Staff, 2021).

The shift to larger ships will impact the value of each shipment being delivered. Once the “Panama Canal operates at its full projected capacity following expansion, this could result in an additional $1.25bn or more in insured goods passing through the canal in just one day” (Panama Canal expansion: Impact on shipping and insurance, 2016). This expansion “equates to $460bn a year, significantly increasing risk accumulation in the region” (Panama Canal expansion: Impact on shipping and insurance, 2016).
The worldwide efforts against maritime piracy are yielding positive gains, yet the need for advanced technology, new tactics, and techniques against this threat is desperately needed. In January 2024, Marine Insight published an article titled 18 Anti-Piracy Weapons for Ships to Fight Pirates. In this article, the tried-and-true weapons were discussed, including firehoses/water cannons, tasers/stun guns, and nets deployed to entangle the pirate’s boat propeller. Some of the more interesting weapons deployed were acoustic devices and a dazzle gun. A long-range acoustic device (LRAD) is a non-lethal anti-piracy device that utilizes a high-intensity sound beam to deter pirates. This technology has only been deployed on a limited number of cargo and cruise ships to date.

An anti-piracy laser device “uses a non-lethal laser beam to provide a visual warning to pirates and distract them temporarily. The laser can be used during the day and night, and can be easily operated by the ship’s crew.” (Raunek, 2024).
A dazzle gun that “uses green light to disorient and temporarily blind the pirates. The concentrated blast of green light can be used during the day and night.” (Raunek, 2024).

A pain ray, an electromagnetic wave known as the Active Denial System (ADS), “transmits a narrow beam of electromagnetic energy to heat the skin without causing permanent damage. The wave penetrates the skin, causing an unbearable burning sensation, forcing pirates to run away or jump overboard.” (Raunek, 2024). These weapons illustrate the evolving threat and the necessary response to counter maritime piracy.

Despite considerable investments in resources, technology, and manpower to combat maritime piracy, the results, although positive, still result in significant monetary losses and the loss of life and trust throughout the shipping industry. Additional shifts in tactics, technologies, and international laws are required to see future gains against the pirates.
Cyber and Digital Environment and Its Impact on Maritime Piracy
Digital communication and digital services are playing a bigger role in the maritime industry, whether it be the development of intelligent systems, blockchain, IoT, or automation. These systems can help streamline existing processes, create new business opportunities, transform supply chains, and make communication efficient.
The maritime industry handles 90% of global trade and faces increased levels of cyber threats that extend beyond the digital realm, affecting physical and operational security. With approximately 50,000 merchant ships and 10 billion tons of cargo moved each year, the global maritime industry is highly susceptible to disruptions from cyberattacks that can also impact physical operations. These disruptions ripple across global supply chains, causing delays and financial losses. A 2020 study by Allianz revealed that cyber incidents are the second-largest risk to shipping companies, with potential losses of up to $4 billion annually due to cyberattacks. The following three items are key targeted areas of cyber-physical attacks. (Verma, 2024).
- “Navigational System Attacks: Per the US Coast Guard, over 20% of vessels in certain regions have experienced GPS (Global Positioning Satellite) interference. Attacks targeting navigation systems, such as GPS jamming and spoofing, can lead to disastrous misdirection or collisions. In 2017, several vessels near the Russian Black Sea reported GPS anomalies, with their navigation systems incorrectly placing them miles inland.
- Operational Technologies (OT) System Vulnerabilities: OT systems, which control physical functions on ships and in ports, are becoming prime targets. Research from the Cyber Keel Consultancy shows that up to 80% of onboard OT systems remain unpatched and vulnerable.
- Data and Communication Network Threats: A 2021 study from the International Maritime Organization (IMO) revealed that maritime communication networks, often lacking encryption, are increasingly targeted. Hackers could potentially intercept sensitive data, manipulate cargo manifests, or even silence emergency alerts, which happened in a 2019 incident when hackers compromised a ship’s communication systems, leaving it unable to transmit its current location.” (Verma, 2024).
Additionally, maritime information, including traffic, ship locations, cargo types, ports, and lighthouses, is readily available at a low monthly cost from websites such as www.marinetraffic.com. All this information and these attacks can become an opportunity for pirates and maritime piracy. We will explore some scenarios below –
- Pirates could attack the supply chain management systems and switch the products in a container to fake or bootlegged products.
- Pirates could undermine the supply chain management systems and insert a malicious technology to switch the products in a container to something (such as a communication device) that intercepts or jams the ship operations.
- Pirates could intercept communications to find information on the ship’s location and /or the manifest. Access to such information can lead to coordinated attacks, and if some rare products are being carried, the data could be used to manipulate markets and drive prices higher. Various types of spoofing can be employed to execute man-in-the-middle attacks. A “spoofing attack” is a situation in which a person or program successfully identifies as another by falsifying data to gain an illegitimate advantage. Several different types of spoofing attacks can be carried out based on the desired result in a particular environment. (Balaban, 2020).
- Pirates could block, jam, or spoof GPS signals, sending the ship on a wrong course that leads to danger. Pirates could replace the GPS itself, allowing them to know and control the ship’s location. GPS spoofing is an attack in which a radio transmitter located near the target is used to interfere with a legitimate GPS signal. The attacker could also block data or transmit inaccurate coordinates (Korolov, CSO Online 2019).
- Pirates may present themselves as passengers with fake documents and without proper checks of their identity, ships may end up with nefarious passengers on board.
- Pirates can utilize digital technologies and networks to coordinate attacks and conceal financial transactions.
In September 2020, the United States’ Maritime Administration (MARAD) issued a notice warning of multiple instances of GPS interference in various parts of the world, including the eastern and central Mediterranean Sea, the Persian Gulf, and numerous ports in China. (Gahnstrom, 2024).
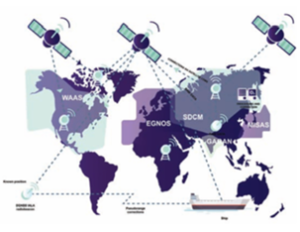
Many of these attacks could be prevented by eliminating the possibility of spoofing and enabling the verification of the authenticity of the source, whether it be a product, signal, DNS, email, component such as GPS, container, or person. Additionally, the storage of information (such as manifests) in large databases must be reduced, as they become prime targets for attacks by hackers/pirates. Several ideas to prevent GPS spoofing were presented in the 2019 CSO Online article by Korolov (Korolov, 2019).
Securing Shipping Manifests and Passenger Authenticity
A recent technological update has led to new ideas of decentralized identity and verifiable credentials. In a decentralized identity system, the issuer of the identity, the holder of the identity, and the verifier of the identity are three distinct entities. The verifiable credential is issued by the issuer and retained privately by the holder. The verifier can authenticate it without the need for the issuer and the verifier to have a direct connection with each other or for the data (trusted credentials) to be stored in a database accessible by both the issuer and the verifier. Figure 9-11 below shows the relationship between the issuer, the holder, and the verifier. The relationship between the three parties is the Verifiable Credential Trust Triangle. (Preukschat & Reed, 2021).
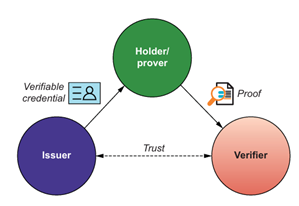
In this data trust model, the authenticity of both the issuer’s and the issued credentials is cryptographically proven to the verifier, along with proof of the actual credential. This also decentralizes information, so the holder’s data is stored in their wallet and not in an extensive external database that could be hacked. This Verifiable Credential Trust Model is a standard practice at the World Wide Web Consortium (W3C), as noted in Chapter 5.
Applying this trust model to scenarios 1-6 above, the products and their components being shipped could have verifiable credentials issued to them, which enables the ship/supply chain to verify the authenticity of the products or the containers, thereby preventing piracy.
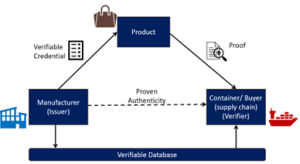
Could man-in-the-middle attacks be prevented between two endpoints, hence removing the scenario of pirates spoofing the GPS signal, as the ship’s system would not connect with sources that are not authentic? Perhaps, a system could be introduced that includes a verifiable credential with a strong signal, allowing the ship’s GPS to distinguish between genuine and spoofed signals and discard any spoofed signals. There could be other iterations on how the system is built, with the end goal of verifying a good, authentic signal and discarding the bad signal.
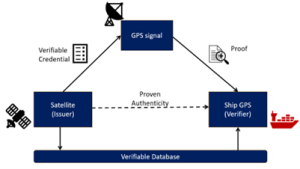
If a hacker attempts to change the onboard system itself by replacing the GPS so that a ship is guided to the wrong place, there could be a system in place that detects the presence of a fake GPS, which in turn will not be able to check in with the ship’s operating system, and therefore becomes unusable. In this scenario, the initialization process would require the operating system (OS) to request proof of an identity credential from the GPS. The GPS must reply with an acceptable proof. The OS would then verify the proof’s cryptographic integrity and use an over-the-air (OTA) process to look up the manufacturer’s DID in a Verifiable database to obtain the public key required to verify the proof. Suppose both verifications pass, and the component’s identity is confirmed. In that case, the OS will then exchange a peer DID with the element, allowing subsequent communications to use a secure private channel known only to the two parties.
On similar lines, a person’s identity could be authenticated as they board the boat, so that people with fake identities, etc., do not board the ship. Individuals with counterfeit identities are likely to have malicious intent. The picture below shows how a person’s identity can be proven authentically.
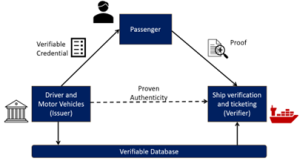
We have explored various scenarios where decentralized identity and verifiable credentials can play a significant role in establishing the authenticity of products, signals, supply chains, and people, hence reducing piracy.
Furthermore, following up on another principle from Chapter 5, the manifests, routes, etc., must not be stored in large databases. Instead, ships should consider how the data can be chunked and distributed so that it cannot be found by hackers/pirates as a singular table or file in a database.
Widely available maritime traffic and location information via websites is recommended to be curbed or restricted based on a need-to-know basis.
Exploring Alternatives to Reduce Maritime Losses Due to Piracy
As noted earlier, larger ships are now transporting enormous amounts of goods in a single trip, making these vessels a profitable target for pirates. Pirates can capture one ship and have the ill-gotten gains of several smaller boats from past days in the industry. However, at the same time, the shipping industry faces financial pressures to increase the amount of cargo that can be transported in one shipment; as a result, it may not be feasible to reduce the size of the ship or cargo volume.
Potentially, suppliers may want to distribute their cargo across various ships, so that a delay or pirate attack on a single vessel does not affect the entire cargo of a given customer, thereby mitigating possible business losses.
Ship companies may also want to consider how they can reduce the cost of sailing by incorporating more automation and mechanization in areas of supply chain management. It would be beneficial for shipping companies to develop autonomous software, perception systems, command and control, hull machinery, electrical systems, and external communications, so that their ships are self-contained and can move from point A to point B while thwarting attacks with minimal intervention. This will not only help reduce the shipping costs but also bring safety to humans who are often put in harm’s way due to pirate attacks and other maritime factors.
Conclusions
From the Sea Peoples of yesterday to the Somali pirates of the 21st century, maritime piracy has evolved in response to shifting geopolitical, economic, and technological factors. Although often romanticized, piracy remains a serious global threat that requires a coordinated legal, naval, and financial response. As international shipping grows and state control in fragile regions fluctuates, the need for sustained vigilance and innovation in maritime security remains paramount.
The maritime industry is the backbone of global trade, responsible for transporting approximately 90% of the world’s goods and services. However, it faces numerous security challenges, with piracy being one of the most persistent and disruptive threats. Despite international efforts and advances in technology, piracy continues to pose significant risks to maritime operations, particularly in high-risk areas such as the Gulf of Guinea and the Strait of Malacca. In addition to piracy, the industry must navigate geopolitical tensions, environmental regulations, labor shortages, and cybersecurity threats. Cyber and digital threats can be highly disruptive, where piracy can manifest or be enabled in the form of pirated goods, fake GPS signals, man-in-the-middle attacks, or failed identity checks for pirates posing as ordinary individuals.
Furthermore, data and manifests can be stolen to disrupt a ship’s operations, thereby unsettling supply chains and markets. At the same time, digital networks could be used to transfer the stolen money without detection. To mitigate all these risks, identity and computing architecture become essential. We must explore new techniques, such as decentralized identity, verifiable credentials, and distributed computing, which can mitigate these risks and lead to an authentic zero-trust architecture that prevents piracy in maritime activities.
Questions
- What are three reasons given for why piracy remains an issue in 2025?
- In what century was it noted as the earliest record of maritime piracy?
- Do you think current anti-piracy efforts are adequate? Why or why not?
- Are there additional methods that pirates could use to take control of a vessel?
- As a ship’s captain, list five risk mitigation strategies you would use to thwart pirates.
References
Alexa, l. (2025). Piracy and armed robbery up: IMB report April 16 16025 / Worldwide. World Ports Org. Retrieved July 13 from https://www.worldports.org/piracy-and-armed-robbery-up-imb-report-16-apr-2025-worldwide/
Balaban, D. (2020). 11 Types of Spoofing Attacks Every Security Professional Should Know About. Security Magazine. Retrieved August 13 from https://www.securitymagazine.com/articles/91980-types-of-spoofing-attacks-every-security-professional-should-know-about
Bueger, C. (2015). Learning from piracy: future challenges of maritime security governance. Global affairs, 1(1), 33–42.
Cline, E. H. (2021). 1177 BC: The year civilization collapsed: Revised and updated.
Combined Maritime Forces: CTF 151. (2025). US Navy. Retrieved July 12 from https://www.cusnc.navy.mil/Combined-Maritime-Forces/
David, N. (2015). The US Navy Is Working on AI That Can Predict a Pirate Attack. Science Alert. Retrieved July 13 from https://www.sciencealert.com/the-us-navy-is-working-on-ai-that-can-predict-a-pirate-attack
Gahnstrom, J. (2024). Recognizing and Dealing with Threats to Marine Navigation Systems. The Nautical Institute. Retrieved July 28 from https://www.nautinst.org/resources-page/free-article-jamming-and-spoofing.html
Greenwich, R. M. (2025). The ‘golden age’ of piracy. In R. M. Greenwich (Ed.), Online. Online: Royal Museums Greenwich.
Konstam, A. (2011). Pirates: The complete history from 1300 BC to the present day. Rowman & Littlefield.
Korolov, M. (2019). What is GPS spoofing? And how you can defend against it. CSO Online. Retrieved July 28 from https://www.csoonline.com/article/567233/what-is-gps-spoofing-and-how-you-can-defend-against-it.html
Malhotra, V. (2025). The edge we can trust, which enables Trust transactions. WOPLLI Technologies. Retrieved August 12 from https://www.woplli.com/
Maritime Surveillance MARSUR. (2025). European Defense Agency. Retrieved JuJuly 12rom https://eda.europa.eu/what-we-do/all-activities/activities-search/maritime-surveillance-(marsur)
Number of pirate attacks against ships worldwide from 2010 to 2024. (2025). Statista Research Department. Retrieved July 13 from https://www.statista.com/statistics/266292/number-of-pirate-attacks-worldwide-since-2006/
Panama Canal expansion: Impact on shipping and insurance. (2016). Allianz. Retrieved July 13 from https://commercial.allianz.com/news-and-insights/reports/panama-canal-expansion.html
Preukschat, A., & Reed, D. (2021). Self-Sovereign Identity
Decentralized digital identity and verifiable credentials. Manning. Retrieved August 12 from https://www.manning.com/books/self-sovereign-identity
Raunek. (2024). 18 Anti-Piracy Weapons for Ships to Fight Pirates. Marine Insight.
Rediker, M. (2011). Villains of all nations: Atlantic pirates in the golden age. Beacon Press.
Staff, P. M. (2021). Panama Canal authorizes transits for larger, wider ships. Professional Mariner. Retrieved July 13 from https://professionalmariner.com/panama-canal-authorizes-transits-for-larger-wider-ships/
Staff, R. (2023). Ahoy! The Golden Age of Pirates and Maritime Art. M.S. Rau Fine Arts. Retrieved JuJune 7rom https://rauantiques.com/blogs/canvases-carats-and-curiosities/ahoy-the-golden-age-of-pirates-and-maritime-art?srsltid=AfmBOorv6ifF2gLKaYu9wuqZomJ58howOpWR6zrWjpMvjLOBlBkrjoPu
Steven, J. (2021). The Pirate Codes. Medium. Retrieved JuJuly 7rom https://stevenberlinjohnson.com/the-pirate-codes-75e0585c36ea
United Nations Convention on the Law of the Sea – Part VII. (1982). New York, New York: United Nations. Retrieved from https://www.un.org/depts/los/convention_agreements/texts/unclos/part7.htm
Verma, D. (2024). Maritime Industry’s Cyber-Physical Security Convergence: Trends and Strategies. Linkedin. Retrieved July 28 from https://www.linkedin.com/pulse/maritime-industrys-cyber-physical-security-trends-strategies-verma-np6sc/
