1 Maritime Transportation Systems (Nichols)
Abbreviations
AI – Artificial Intelligence
ADS – Air Defense Systems
AIS – Automatic Identification System (VHF transponder system)
AMO – Area of Maritime Operations
ATON – Aids to Navigation (lights, markers, lighthouses, etc.)
BeiDou – China’s GNSS system
CAS – Collision Avoidance System
CIS – Critical Infrastructure Sector
CISA – Cybersecurity and Critical Infrastructure Security Agency
CBP- Customs and Border Protection
CUAS- Counter-Unmanned Aircraft System
DHS – Department of Homeland Security
DIA- Defense Intelligence Agency
DOT- U.S. Department of Transportation
ECD- Eichelberger Collective Detection (Anti-spoofing technology)
ECDIS – Electronic Chart and Display Information System
EPIRB – Emergency Position Indicating Radio Beacon
ETA – Estimated time of arrival
FIA – Foreign Intelligence Agencies
FLOATPLAN – A formal plan of activities and locations to be visited or anchored is sent to trusted sources. ETAs are given, and emergency actions/communications are delineated.
Galileo – The European Union GNSS system
GDP – U.S. Gross Domestic Product
GLONASS – Russian Global Navigation System
GNSS – Global Navigation Satellite System
GPS – Global Position System (U.S.)
GUNK HOLE – A small anchorage usually protected from weather on at least two sides, where recreational boats rest, take refuge, fish, or enjoy life. Average depth under keel is 6-10 feet with a favorable anchoring bottom seabed. Rode lengths average 5-7 / 1 per depth under keel, and swing radius is controlled. It is always away from crab pots or crack-of-dawn fishing fleets.
ICE- Immigration and Customs Enforcement
IP – Intellectual Property
IoT- Internet of Things
ML- Machine language
MTS – Maritime Transportation Sector and Subsystems
NOAA -National Oceanic and Atmospheric Administration
PFD – Personal Flotation Device
PII – Personal identifiable information
PLD – Personal Locator Device (Distress beacon to COSPAS-SARSAT 460 MHz satellite system)
PNT – Position, navigation, and timing
POTUS -President of the United States
RA – Risk Assessment
RADAR – Using radio high-pulsing high-frequency electromagnetic waves to detect the presence, direction, distance, and speed of aircraft, ships, and other objects
RN – Ryan – Nichols qualitative information risk assessment
RTB – Return to Base or marina, piers, or ports
SCADA -Supervisory Control and Data Acquisition
SONAR – A system for the detection of objects and for measuring the water’s depth by emitting sound pulses and measuring their return after being reflected
OSINT- Open-Source Intelligence
UAS – Unmanned Aircraft System
UNCTAD – United Nations Conference on Trade and Development
USCG / USCGA -United States Coast Guard / United States Coast Guard Auxiliary
UUV – Unmanned Underwater Vehicle
VHF – Very high frequency device (30 – 300 MHz; 1-10 meters wavelengths)
VTC – Vessel Traffic Control
VTS – Vessel Traffic System
VTM- Vessel Traffic Management
WMD – Weapons of Mass Destruction
Student Learning Objectives
Our opening chapter sets the stage for advanced maritime discussions on sector security across four disciplines of interest:
Students will understand the vastness of the MTS through the (Kessler & Shepard, 2022), A comprehensive vision, and how security is a prime issue. MTS is a critical infrastructure and requires serious protection because its purview is militarily and economically important. (Kessler & Shepard, 2022) apportions most of its MTS description to cybersecurity. However, cybersecurity is not the only threat to MTS.
Students will be challenged to understand two different perspectives of vulnerabilities versus threats to MTS.
MTS attack Vectors and unique/modern threats to MTS will be introduced.
The key to the evaluation of maritime security is Risk Assessment. Several approaches will be introduced.
Chapter 1 sets the stage for our newest educational textbook (Book 11) [1] on Maritime Security associated with the Maritime Transportation Sector and Systems (MTS). MTS is a huge system of systems. The best description of MTS comes from the work of Dr. Gary C. Kessler and Dr. Steven D. Sheppard entitled (Maritime Cybersecurity: A Guide for Leaders and Managers. Kessler & Sheppard, 2020). We will draw heavily on their extensive work and expand their vision beyond cybersecurity, with full credit to their previous works and professionalism. We recommend readers buy the 2nd Edition. [2] (Kessler & Shepard, 2022) MTS is part of the critical infrastructure systems that require protection under DHS. Remember this when we evaluate Threats vs. Vulnerabilities to MTS.
WHAT ARE WE TRYING TO SECURE?
Basically, a huge sector of our lives is associated with transportation over water – the MTS. It is composed of many systems and subsystems of integrated resources. We will look at MTS from three perspectives: A captain’s perspective of a moderate recreational cruising yacht, a massive part of DHS’s critical infrastructure, and finally, the huge maritime DHS subset known as MTS. Maritime Security is different for all three perspectives, and investments are significant to protect them based on size and scale.
THREE PERSPECTIVES
CRYPTOWIZ
The playground is the Chesapeake Bay – one of the most beautiful and historical sailing and power cruising waters in the world. The author is a 40-year experienced Captain [previous experience on two sail and two power boats] of the recreational cruiser known as CRYPTOWIZ, a Four Winns 33.8 feet 2001 built boat that sports advanced safety equipment for cruising the Northern, Eastern, and Western branches of the Chesapeake. [3] See Figures 1-1 and 1-2.
The priorities of the Captain are 1) SAFETY FIRST (Avoid collisions, know where you are, follow USCG and Maryland State Boating Rules; maintain reasonable speeds; know the ATON locations and bottom characteristics; have/distribute a FLOATPLAN); [4] 2) WEATHER – follow Update Notice to Mariners and weather projections. They change rapidly. 3) CREW– Train and protect Crew and regularly practice safety and medical drills with passengers; [5] 4) MAINTENANCE – keep up and log / schedule maintenance on all resources for the boat. By definition, everything breaks or is manufactured under design. Boat equipment repair costs double compared to similar land equipment. [6] Being a Captain on the Chesapeake Bay was a joy and a consternation all wrapped up in a complete control drama. However, the Maritime Security perspective is minimal once RTB docked, the boat was in a locked gated area under special roofing and protected by night security, both by electronics and humans.
According to the Chesapeake Bay Foundation, there are 212,000 registered boats on the Bay. This figure does not include out-of-state or smaller unregistered ships, which brings the number closer to 400,000 (CBF 2025). Compare that to nearly 12 million recreational boats in the U.S. (Statista, 2024). CRYPTOWIZ has a lot of competition to find good “gunk holes” and protected anchorages in its home maritime AMO.
Figure 1-1 CRYPTOWIZ Source: Author (R.K.Nichols)

Figure 1-2 A Night View from CRYPTOWIZ on Eastern Chesapeake Bay Source: Author (R.K.Nichols)

DHS
Let’s take a SpaceX© to a satellite view of the United States. We spy the purview of the Department of Homeland Security. The Department of Homeland Security (DHS) employs over 260,000 people and has an annual budget of approximately $51.672 billion as of fiscal year 2020. It is the third-largest Cabinet department in the U.S. federal government, the Department of Homeland Security (2025)
CISA has identified sixteen Critical Infrastructure Sectors for DHS to Secure CISA (2020). Perhaps the most important, based on size, budget, resources, assets to secure, and activities engaged, is that the Maritime Transportation System (MTS) represents the A-list performer. Maritime represents an integral part of the Transportation Systems Sector. The transportation sector itself comprises maritime, aviation, trucking, railroads, and other forms of ground transportation (Kessler & Sheppard, 2020). All transportation modes interact with each other and track cargo from the point of origin to the final destination. [7]
MTS SIZE, SCOPE, USERS
According to Kessler & Shepard (2022), approximately 90 percent of the cargo travels by ship. There are over 100,000 ships, including intercoastal vessels, engaged in the transport of cargo and passengers; these ships have an asset value of more than $2 trillion and carry more than $20 trillion of cargo annually. (Kessler & Shepard, 2022) [8] 40 percent of all imports come through the Ports of Los Angeles and Long Beach. (Kessler & Shepard, 2022) The MTS contributes over $5 trillion annually to the gross domestic product (GDP), and supports more than 30 million jobs, representing 20 percent of the entire workforce (Kessler & Shepard, 2020)
According to Kessler & Shepard (2022), the federal and private ATONs have 20,000 bridges over water. MTS includes 25,000 miles of navigable channels, 95,000 miles of shoreline, 361 commercial ports, 20,000 bridges over water, more than 3,700 marine terminals, 200 ferry operations, and 238 locks at 192 locations (Kessler & Shepard, 2022). The MTS user community includes thousands of charter fishing boats and over 12 million recreational boats. The entire system of coastal and ocean-based weather ATONS, communication stations, and buoys is shared by military, work boats, dredges, seaplanes, survey vessels, maintenance vessels, fishing vessels, personal power boats and sailboats, drilling platforms, moorings, and fixed-location offshore facilities. (Kessler & Shepard, 2022)
UNCTAD reports that there were nearly 120,000 merchant vessels on the water in 2023, with a transport capacity of 1.5 million gross tons. They ship to more than 4,800 ports in 200 countries. They don’t make money sitting idle, so they are constantly moving cargo. (UNCTAD, 2019 (updated))
Perhaps the best vision of the Maritime Transportation System (MTS) is shown in Figure 1-3, renumbered from (Kessler & Shepard, 2022). It is truly a hierarchical group of interacting / interrelating systems and subsystems pertaining to maritime resources and activities.
Figure 1-3 The MTS Systems of Systems Source: Courtesy of (Kessler & Shepard, 2022), renumbered from
The original Figure 1-2 system of systems
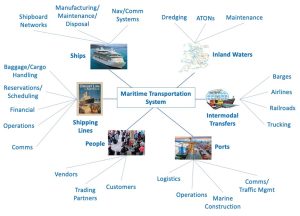
MTS
Exploring the Kessler and Shepard vision (Kessler & Shepard, 2022), the Maritime Transportation System (MTS) is a complex group of systems of subsystems. It comprises six interconnected systems: ships, shipping lines, ports, people, inland waterways, and intermodal transfers. See Figure 1-3: Each of these systems has its unique subsystems. However, the subsystems are independent of each other as well as co-dependent and complexly intertwined (Kessler & Shepard, 2022).
Look at the straightforward priorities of the CRYPTOWIZ above. The life of this recreational cruiser, like a much larger ship, intersects with the life of a marina or port, concerned with the safety of Crew and passengers, and intersects with people and cargo with the ship’s transit from point A to B to C on a FLOATPLAN. The Captain’s concerns are collision avoidance, communications, electronics, bottom characteristics, waves, current, maintenance, ballast, anchoring, weather, RADAR, SONAR, AIS, CAS, charts, emergency procedures, food, potable water, engines, recreation, food stuff, storage, tools, lines and anchor gear, rules, and regulations, costs, whether it is through a small “gunk” hole near Bloody Point Light near Kent Point via ATONs or on to Baltimore Harbor via shipping lanes, intermodal transfers, and /or inland waterways. The larger components require attention to security. (Kessler & Shepard, 2022) The text is dedicated to cybersecurity. Our Book 11 is concerned with a whole range of modern identified threats and countermeasures. Cybersecurity is only one persuasive threat to MTS. [9] [10]
Let us explore the (Kessler & Shepard, 2022) vision and dig into the components/ subsystems.
Ships
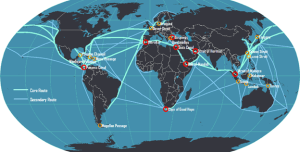
The ship’s subsystem envelops the lifecycle of a vessel, from manufacturing, to maintenance, to operations, to sale or disposal. (Kessler & Shepard, 2022). Ships are essentially floating cities that need to be interconnected in terms of communications, operations, passengers, Crew, entertainment, navigation systems, and other vessel-specific networks. (Kessler & Shepard, 2022). See Figure 1-4 for major shipping routes.
Figure 1-4 Global Shipping Routes Source: Courtesy of (Jean-Paul-Rodrigue, retrieved 2025)
Ports
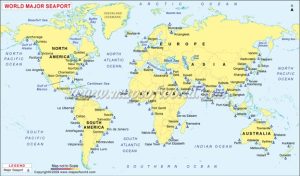
Figure 1-5 shows a world map of major ports – technically, any country with a coastline falls into the MTS of that jurisdiction. However, the U.S. MTS interacts with all of them for cargo movement, joint military operations, civilian construction support, recreational cruises, drug and criminal interdiction, crew investigation, and economic/geopolitical positioning.
The ports subsystem includes the construction and maintenance of the port, logistics within the port, vessel traffic management (VTS), intermodal interactions between carriers that enter and leave the port carrying passengers and cargo, and all aspects of daily port operations. (Kessler & Shepard, 2022) All ports are unique. They have different forms of ownership and management, different mix of civilian and military vessels and operations, and tenants, personnel management, intermodal connections, cargo, traffic patterns and volumes, and supporting operations. (Kessler & Shepard, 2022) Intellectual Property (IP) theft related to port operations and construction is a prime spy target.
People
The people subsystem includes vendors, the entire supply chain, trading partners, customers, Crew, investigators, security, anti-piracy teams, workers, passport control, and colleagues. Proper vetting of all personnel is required, but it is rarely done! Serious concerns include threats to personally identifiable information (PII) and financial information in personnel and passenger databases. (Kessler & Shepard, 2022)
Figure 1-5 World Map of Major Ports Source: Courtesy of (Anonymous, 2025)
Shipping Lines
The shipping lines subsystem comprises the operation and management of the companies that own, manage, and operate ships. It includes handling of passengers and cargo, reservation and scheduling systems, finances, operations, and communications. (Kessler & Shepard, 2022) [11]
Inland Waters
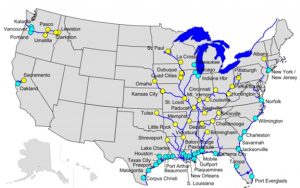
The inland waters subsystem includes the inland waterway system, ATONS, and dredging and maintenance of the waterways. Figure 1-6 shows the inland waters of the U.S. Attacks on inland waterways can cause tremendous havoc in the narrow waterways. (Kessler & Shepard, 2022)
Figure 1-6 Inland-Waterways of the United States Source: Courtesy of: (https://free-printablemap.com/wp-content/uploads/2018/10/inland-waterways-of-the-united-states-wikipedia-with-navigable-waters-of-the-united-states-map.png, 2018)
Intermodal Transfers
The intermodal transfer subsystem describes how the MTS interfaces with other transportation modalities, including the inland barge system, railroads, trucking, aviation, and satellites. (Kessler & Shepard, 2022)[12] This is where the MTS intersects everything else. (Kessler & Shepard, 2022) Like General Lee’s real strategy at Gettysburg, even the best port or ship security and shipping line may be open to oblique attacks by trading partners. (Harman, 2003). See Figure 1-7, an example map of the U.S. intermodal transfers subsystem to the large ports along the intercoastal and coastline of the U.S.
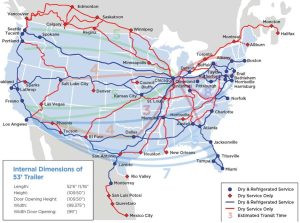
Special Assignments – Interdiction and Customs and Border Protection (CBP) / ICE
The USCG has an incredibly huge/widespread area mission/responsibility of protecting U.S. coastlines. One of their more enviable and dangerous duties is drug enforcement. (SCG, 2024) Other missions are search and rescue, migrant trafficking, law enforcement, marine environmental protection, ports, and waterways security. (SCG, 2024) gives us a detailed look at these activities.
The CBP secures 6,000 miles of the Mexican and Canadian land borders and over 2,000 miles of coastal waters. CBP works closely with U.S. Immigration and Customs Enforcement (ICE) under DHS to enforce immigration laws from illegal entry into the country. Under POTUS’s increased border enforcement measures, illegal crossings at the U.S.-Mexico border have decreased by 94% compared to the same period last year. (CBS NEWS, 2025)
Modern Threats
All the above systems and subsystems must contend with a new generation of Threats to information, navigation, communications, automation, operational technology, the Internet of Things (IoT), artificial Intelligence (AI), smart devices, machine learning (ML), UAS, CUAS, UUV, Spoofing, and more. The maritime stakeholder must integrate these new elements into their security plans and operations, as well as be functional in a legacy environment. (Kessler & Shepard, 2022)
Countermeasures Forgotten?
The author has great respect for the (Kessler & Shepard, 2022) book (Chapter 1) [13] for its brilliant description and MTS organization. (Kessler & Shepard, 2022) concentrates on cybersecurity and relates all his MTS vectors through that lens. However, using similar definitions in the Ryan-Nichols qualitative Information Risk Assessment Model (Nichols & Ryan, Defending Your Digital Assets Against Hackers, Crackers, Spies, and Thieves, 2000) [14](covered below) the (Kessler & Shepard, 2022) the book concludes incorrectly that Vulnerabilities is the Object-de-l’entrée for cybersecurity effects on the MTS vectors (covered in the next section).
On page 239 of (Kessler & Shepard, 2022), quote:
“Vulnerabilities Trump Threats Maxim: If you know the vulnerabilities (weaknesses), you’ve got a shot at understanding the threats (the probability that the weaknesses will be exploited and by whom (sic or what). Plus, you might even be ok if you get the threats all wrong. If you focus mostly on threats, you are probably in trouble.”
Threats are indeed real, and vulnerabilities are weaknesses in the system. Still, threats can act on an information system (cybersecurity is the protection of information) with or without the presence of vulnerabilities. Threats cause real damage and potential death. Vulnerabilities do not. We can identify vulnerabilities, but so what? They are always part of an information system. Flaws exist in every major computer system or network. Fix the bug, and they come back with “kittens.” The Ryan-Nichols RA Model [15] defines Risk = Threats x Vulnerabilities x Impact / Countermeasures. Vulnerabilities are a constant of the system, and Impact is basically a constant accounting number; both drop out with a little calculus. The effective Risk Assessment reduces to Risk ~ f (Threats / Countermeasures). [16] Countermeasures represent an entire spectrum of defenses (electronic, people, resources, change in threat-actor-target, defense, or police response, etc. that mitigate the Threats. DHS uses scenario analysis to analyze the 1000s of different threats to the U.S. Depending on the RA lethality, DHS allocates funds and devotes teams to addressing the top net Threats. Fortunately, cyber threats are not at the top of the list in terms of net RA, lethality, or funding. Cyber threats may affect millions of computers on the scoreboard, but they generally don’t kill like chemical, nuclear, or missile strikes. They represent very low to low-medium values on the RN lethality Legend. They are a big annoyance, but proper countermeasures and backup systems can effectively mitigate/terminate them.
MTS threats are more concerning than simply vulnerabilities in any of the MTS vectors. (Kessler & Shepard, 2022) fails to consider effective countermeasures. A more dangerous Threat – Vulnerability exploitation is in its combination. DHS Critical Infrastructure Sector (CIS) relationships are complex and made more lethal when cyber is added to the mix. See Figures 1-8 and 1-9. Vulnerabilities are only part of the baseline RA evaluation.
Figure 1-8 CIS Relationships Source: Courtesy of (Peerenboom J, 2001)
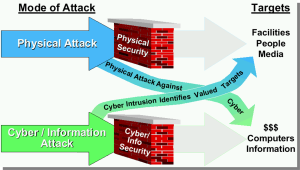
Figure 1-9 CIS Relationships Source: Courtesy of (Peerenboom J, 2001)
To emphasize the point that cybersecurity is only one of the Threat vectors against MTS, not fundamentally just a Vulnerability risk assessment, look at the number of incidents reported for underwater communication, intentional cable cutting by Russian and Chinese-flagged ships. These are intentional threats by a nation-state and not related (or just tangentially) to cyber intrusion. SCC – cut Impact is huge since over 95% of all communications, trades, military instructions, and financial instruments move by underwater cables. [17] (carnegieendowment.org/, 2024) (NPR, 2024) (TAIPEI Times, 2025) MTS is part of the DHS CIS, and that is where focus needs to be returned, especially for Risk Assessment (RA).
MTS VECTORS
Let us return to the (Kessler & Sheppard, 2020) vision and describe MTS vectors that present vulnerabilities to information attacks (cyber, physical, insider, terrorist, asset destruction, or any of the conditions delineated by Parker Hexad and more. (Parker, 1998)[18] Each of the vectors presents opportunities for threats to their information and physical systems. They are symbiotic environments, and affecting one (cyber) may also affect the physical assets. This leverages the attacks and increases the damage possible. [19] (AP / Politico, 2025) There are a multitude of MTS system vectors subject to attacks (cyber and physical). A non-inclusive list includes:
Vessel Operations
All ships are floating computers and data communications networks, which include operational networks controlling ship systems (propulsion, power generation, ballast, anchoring), networks connecting security and cargo management, bridge, navigation and communications, entertainment, weapons control, fire suppression, Bluetooth devices, anti-piracy, lightning arrestor, and docking aids. Every system is interrelated. Cyber (informational computer threat) or fire (real, physical, direct) can compromise these systems. [20] (Kessler & Shepard, 2022) (Nichols, R., Chapter 14 Maritime Cybersecurity, 2020)
Shipping Line Operations
Both cargo and passenger shipping lines have complex outward-facing networks, website presence [21], and internal networks. The internal networks manage vessel communications, passenger and cargo tracking, all the financial management records, legal compliance, and maintenance scheduling. (Kessler & Shepard, 2022)
Port Operations
Ports have their own internal and external communications networks. Ports control cargo, vessels, customers, tenants, security (radioactivity, drugs, microbes, supply chain partners, physical security and surveillance systems, cameras, sensors, terminal headquarters, financial and management systems, logistics, inventory, immigration, Crew, customs enforcement, equipment suppliers, legal authorities, and shipping lines. They also track activity around ATOMs, entry denial, bridge communications, and monitor emergency communications. (Kessler & Shepard, 2022)
Cargo and Shipping
Along with the fundamental connections and users, cargo and shipping networks include many SCADA systems, moving cargo, onloading, and offloading. Cargo security is controlled by computers as well as intermodal transfer–handoffs and necessary linkages to rail, truck, and air carriers. (Kessler & Shepard, 2022)
Manufacturing
Manufacturers have the same MTS information vulnerability vectors as do ports, shipping lines, and cargo firms. However, supply chain management is very important to keep their product lines viable and to mitigate competition and FIA spying. Theft has been a significant issue by rival companies, often enabled by the internet. (Kessler & Shepard, 2022)
Vessel Traffic Control (VTC)
Managing the flow of vessels into ports or inland waterways requires robust communications; position, navigation, and timing (PNT) systems, such as the Global Position System (GPS); situational awareness networks, such as AIS; up-to-date charts and notices to mariners; and other functions that maintain safe and efficient movement of cargo and people. (Kessler & Shepard, 2022). One problem is that not all the military, recreational, and commercial fishing boats have the VTC equipment.
Remote Control and Automation
Remote control ships like UUV, autonomous vessels, docking facilities, drones, trucks, and cranes are all subject to a variety of cyber and physical Threats and Vulnerabilities. The author’s KSU research teams have studied these extensively in their UAS/CUAS/UUV/Space/Marine textbook series. (Nichols R. K., et al., 2021) (Nichols R. K., et al., 2020) (Nichols R. K., et al., 2022)
Legal Environment
There are many rules, regulations, and laws (U.S and International) that guide the maritime industry, plus policies of different nations, ports, and shipping lines. In addition, several maritime organizations publish guidance and procedures related to MTS threats, vulnerabilities, and cybersecurity. (Kessler & Shepard, 2022) One of the best little reminders for small boat owners is from Charlie Wing. (Wing, 2006)
THREATS
Every CIS and MTS specifically is subject to numerous threats. Below are just a few of interest.
The Defense Intelligence Agency 2025 Worldwide Threat Assessment (DIA, 2025) report discusses WMD, missiles, terrorism, unmanned systems, illegal migration, cartels, and drug trafficking from traditional enemies of the U.S – Russia, China, Iran, North Korea, Southeast Asia, the Middle East, and Africa. It discusses the spider-like hands of China in Latin America and other nations. Cybersecurity threats to CIS are not in the top five.
Cyber: Attack Tools
There is literally a plethora of information on cyberattacks, cyber defenses, and cyber structures that are vulnerable. The author decided to reach out to his LINKEDIN colleagues for a small compendium of various Cyber tools. Here is what we found. Figures 1-10 to 1-14 show just a small sample of OSINT. With little effort, we found over thirty of these little cribs in one sitting. Figure 1-10 shows the primary cybersecurity domains and how the military divides them into teams.
Figure 1-10 Cybersecurity Domains Source: (LINKEDIN Feed: Cybersecurity Domains, 2025)

Figure 1-11 presents a hacker’s dream – an advanced hacker’s kit.
Figure 1-11 Advanced Hacker Kit Source: (LINKEDIN Feed: Advanced Hackers Kit, 2025)

Figure 1-12 shows tools used in the dark web – the playground of malicious actors.
Figure 1 -12 21 Dark Web Tools Source: (LINKEDIN Feed: 21 Dark Web Tools, 2025)

Figure 1-13 shows the common cyber-attack vectors.
Figure 1-13 Top 8 Cyber Attacks Source: (LINKEDIN feed: Top 8 Cyber Attacks, 2025)
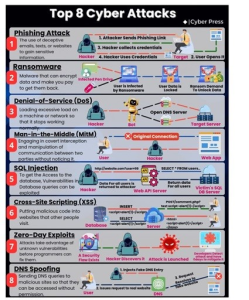
Figure 1-14 shows the top countermeasure forensic tools.
Figure 1-14 Top 100 Forensics Tools Source: (LINKEDIN feed: Top 100 forensics tools, 2025)

GPS and Navigation
In the MTS, so many assets, ships, ports, ATONS, cargo systems, and other vectors depend on PNT and GPS or any one of the four GNSS satellite systems: GPS (U.S.), GLONASS (Russian), Galileo (EU), and Beidou (China’s GPS). Of recent interest to both military and commercial airlines and MTS elements is Spoofing. Spoofing is a potentially deadly technique where attackers manipulate information to deceive individuals or maritime systems. Deception appears to come from a trusted or legitimate source when they are not. Deception is often used to gain authorized access, steal information, or launch other types of attacks. Recently, the Swiss Territorial Data Lab (STDL) showed that Spoofing even works on the more secure GPS bands (STDL, 2025)
There is an effective spoofing countermeasure [especially for ADS] called Eichelberger Collective Detection (ECD) described in (Nichols R. K., 2022). ECD was recommended to the Assure 44 Project for spoof-proof ADS-B. (ASSURE 44 Research University Teams, 2023)
MTS Networks
(Kessler & Shepard, 2022) spends their entire book on this cybersecurity-related subject. A quick search on Google gives literally 1000s of choices and 100’s specific to cybersecurity issues. Amazon’s list of Top Network Security books is instructive (Amazon, 2025)
SCADA
SCADA systems are the guts of every MTS electronic subsystem. SCADA is also a legacy product and, as such, sports many vulnerabilities that can be exploited. STUXNET was a cyberweapon (not a simple virus as reported) designed to exploit the Iranian centrifuges at Natanz by changing the impeller speed on their centrifuges to cause cavitation. STUXNET attacked the SCADA systems’ maintenance code, which was readily available on the internet. The U.S. government has a lab to study SCADA weaknesses and publish guidelines (DOE, 2025)
UAS / UUVS: CBNRECy DEW Weapons
The authoritative work Drone Delivery of CBNRECy – DEW Weapons: Emerging Threats of Mini-Weapons of Mass Destruction and Disruption (WMDD) covers the world of UASs and UUVs. This textbook takes on a whole new purview for UAS / CUAS/ UUV (drones) – how they can be used to deploy Weapons of Mass Destruction and Deception against CBRNECy and civilian targets of opportunity. It is concerned with the future use of these inexpensive devices and their availability to maleficent actors. This work suggests that UASs in the air and underwater UUVs will be the future of military and civilian terrorist operations. UASs/UUVs can deliver a huge punch for a low investment and minimize human casualties (Nichols R. K., et al., 2022). The MTS in its entirety is threatened.
UNDERSEA COMMUNICATIONS CABLES
Undersea cables carry more than 95% of the world’s communications. They are subject to natural movements at the sea bottom. However, recently, China and Russia have been accused of cutting the cables to cause havoc in the South China Sea in anticipation of an invasion of Taiwan and in the Baltic Sea to confuse NATO forces (Nichols R. K., 2022) Detailed studies of the underwater cables cutting and effects on Guam, Hawaii, and vulnerabilities of U.S clear ownership of these cables were presented (R K..Nichols, Johnson, & Diebold, 2024) (Nichols, Diebold, & Johnson, Risk Analysis of submarine cables in the Western Pacific, 2024). These studies are eye-opening warnings to U.S. maritime planners and intelligence professionals.
RISK ASSESSMENTS
Perhaps the best way to evaluate security issues for the MTS is by Risk Assessment (RA). Every agency has its own formalized version of RA or Notice of identifiable problems to its users. Below are some valuable examples/approaches. Many have the same definitions of elements but differ in implementation or emphasis.
Ryan-Nichols (RN) Qualitative Risk Assessment
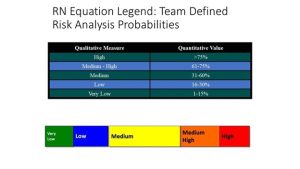
RN looks at Risk as an equal to Threats x Vulnerabilities x Impact / Countermeasures. Threats are real; they may or may not reflect through Vulnerabilities, which are inherent weaknesses in an information system. Vulnerabilities exist in every information system. Impact is an accounting of the damage caused by active Threats. Countermeasures are a whole list of tools/actions/responses to mitigate Risk. However, both Vulnerabilities and Impact are essentially constants in the equation and reduce the effective RN equation to Risk ~ f (Threats / Countermeasures). This means that qualitative information Risk is a clear function of only Threats reduced by appropriate Countermeasures. In the RN Model evaluation, Vulnerabilities have only an initial effect to set a baseline for the system under configuration. RN uses a Lethality Legend to qualitatively measure the various stages of RA based on Threats imposed. (Nichols & Ryan, Defending Your Digital Assets Against Hackers, Crackers, Spies, and Thieves, 2000) (Nichols R., Kaltura_Capture_recording_-_RN – A-D Analysis -1 (2023_02_06 15_36_17 UTC).mp4, 2023) (Nichols R., Ryan Nichols Qualitative Information Risk Assessment, 2023) (INFOSEC and INFOWAR Protection of Information Assets and systems, 2021) Figure 1-15 shows a sample RN Lethality Legend.
Figure 1-15 RN Lethality Legend Source: (INFOSEC and INFOWAR Protection of Information Assets and Systems, 2021)
CARVER
CARVER RA can help with high-risk assets, categorizing and prioritizing, and knowing vulnerabilities and consequences.
Figure 1-16 CARVER Source: (R.K. Nichols, Johnson, & Diebold, 2024)
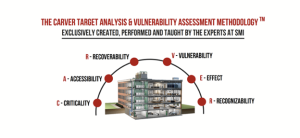
Figure 1-17 CARVER Variables Source: (R.K.Nichols, Johnson, & Diebold, 2024)
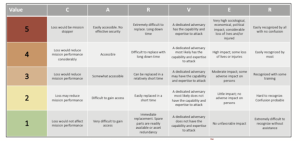
MSHARPP
MSHARPP RA is a targeting analysis tool that is geared toward assessing personnel vulnerabilities, but it can also be applied in conducting a broader analysis.
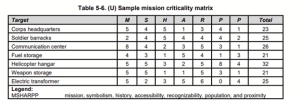
The purpose of the MSHARPP matrix is to analyze likely terrorist targets and to assess their vulnerabilities from the inside out. Consideration is given to local threats, the probable means of attacks, and variables that affect dispositions of potential targets. After developing a list of potential targets, MSHARPP selection factors are used to assist in further refining the assessment by associating a weapon or tactic with a potential target to determine the efficiency, effectiveness, and plausibility of the attack method and to identify vulnerabilities related to the target. The elements are M – Mission. S- Symbolism, H – History, A – Accessibility, R – Recognizability, P – Population, and P – Proximity.
Figure 1-18 MSHARPP Example: Source: (R. K.Nichols, Johnson, & Diebold, 2024)
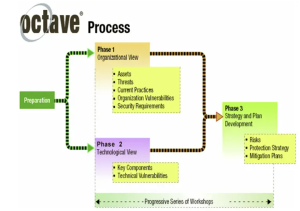
OCTAVE
OCTAVE is an established RA procedure subdivided as follows:
- Operationally Critical Threat, Asset, and Vulnerability Evaluation
- OCTAVE-S – For small organizations with flat hierarchical structures
- OCTAVE Allegro – For large organizations with multi-level structures
- OCTAVE – Build Asset-Based Threat Profile
This is an organizational evaluation. The analysis team determines what is important to the organization (information-related assets) and what is currently being done to protect those assets. The team then selects those assets that are most important to the organization (critical assets) and describes security requirements for each critical asset. Finally, it identifies threats to each critical asset, creating a threat profile for that asset.
OCTAVE – Identify Infrastructure Vulnerabilities
This is an evaluation of the information infrastructure. The analysis team examines network access paths, identifying classes of information technology components related to each critical asset. The team then determines the extent to which each class of component is resistant to network attacks.
OCTAVE – Develop Security Strategies
During this part of the evaluation, the analysis team identifies risks to the organization’s critical assets and decides what to do about them. The team creates a protection strategy for the organization and mitigation plans to address the risks to the critical assets, based on an analysis of the information gathered.
Figure 1-19 OCTAVE Source: (R. K.Nichols, Johnson, & Diebold, 2024)
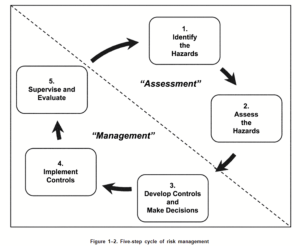
ADRA
Army Deliberate Risk Assessment (ADRA) is a holistic RA conducted by Army Professionals every day on the DD 2977. It is covered in DA Pam 385-30, ATP 5-19. It is a Five-Step Risk Management Cycle.
NOTICE TO MARINERS – A very useful RA tool for Boat Captains
Wikipedia gives a decent description of the Notice of Mariners process.
“A notice to mariners advises mariners of important matters affecting navigational safety, including new hydrographic information, changes in channels and aids to navigation, and other important data. Over 60 countries that produce nautical charts also produce a notice to mariners. Still, one third of these are weekly, another third are bi-monthly or monthly, and the rest are irregularly issued according to need.” (Wikipedia, 2025)
“The U.S. Notice to Mariners is made available weekly by the National Geospatial-Intelligence Agency (NGA), prepared jointly with the National Ocean Service (NOS) and the U.S. Coast Guard. Information in the Notice to Mariners is formatted to simplify the correction of paper charts, List of Lights, United States Coast Pilots, and other publications produced by NGA, NOS, and the U.S. Coast Guard.
Information for the Notice to Mariners is contributed by: the National Geospatial-Intelligence Agency (Department of Defense) for waters outside the territorial limits of the United States; National Ocean Service (National Oceanic and Atmospheric Administration, Department of Commerce), which is charged with surveying and charting the coasts and harbors of the United States and its territories; the U.S. Coast Guard (Department of Homeland Security) which is responsible for the safety of life at sea and the establishment and operation of aids to navigation; and the Army Corps of Engineers (Department of Defense), which is charged with the improvement of rivers and harbors of the United States; in addition, important contributions are made by foreign hydrographic offices and cooperating observers of all nationalities.
The Notice consists of a page of Hydrograms listing important items in the Notice, a chart correction section organized by ascending chart number, a product catalog corrections section, a publications correction section, a summary of broadcast navigation warnings, and a page of additional miscellaneous information. It is the responsibility of users to decide which of their charts and publications require correction. Mariners are requested to cooperate in the correction of charts and publications by reporting all discrepancies between published information and conditions actually observed and by recommending appropriate improvements. A reporting form is provided in the back of each Notice to Mariners.
Issue No. 1 of each year contains important information on a variety of subjects, which supplements information not usually found on charts and in navigational publications. This information is published as Special Notice to Mariners Paragraphs. Additional items considered of interest to the mariner are also included in this Notice. Much of the data in the U.S. Notice to Mariners is obtained from foreign notices.”
Conclusions
MTS is a complex set of maritime subsystems that are interdependent /interactive and composed of many elements/ sub-elements. MTS’s purview is huge. Risk assessment is the key to evaluating security vulnerabilities and threats to MTS. [22 ] Threats to MTS are more important than identified vulnerabilities (although the latter is very useful in identifying initial RA). The key security variable is appropriate Countermeasures, which can be used to mitigate MTS Risk (caused by Threats) to acceptable levels.
References
AMAZON. (2025) best-Sellers-Kindle-Store-Network-Security/. Retrieved from https://www.amazon.com/: https://www.amazon.com/Best-Sellers-Kindle-Store-Network-Security/zgbs/digital-text/16977293011/ref=zg_bs_pg_2_digital-text?_encoding=UTF8&pg=2
Anonymous. (2025, May 30). Old Map of Major Ports. Retrieved from https://3.bp.blogspot.com/: https://3.bp.blogspot.com/-RD2JFkxg2gk/Td-VKr6vgXI/AAAAAAAAACA/m0T6KvtOpM8/s1600/world-sea-ports.jpg
AP / Politico. (2025, May 18). how-did-a-mexican-tall-ship-smack-into-the-brooklyn-bridge-00356342 Retrieved from https://www.politico.com/news/: https://www.politico.com/news/2025/05/18/why-did-a-a-mexican-tall-ship-smack-into-the-brooklyn-bridge-00356342
ASSURE 44 Research University Teams (2023) 1 L.UAS.86 – A44 Mitigating GPS and ADS-B Risks for UAS Task 5 Final Report, Washington, DC: U.S. Department of Transportation (Unclassified).
carnegieendowment.org/ (2024, December) baltic-sea-internet-cable-cut-europe-nato-security?lang=en Retrieved from https://carnegieendowment.org/: https://carnegieendowment.org/emissary/2024/12/baltic-sea-internet-cable-cut-europe-nato-security?lang=en
CBF. (2025, June 28) Chesapeake Bay Foundation. Retrieved from https://www.cbf.org/: https://www.cbf.org/about-the-bay/bay-facts.html
CBS NEWS (2025, February 20) legal-crossings-u-s-mexico-border-down-94-percent-border-patrol-chief-says/. Retrieved from https://www.cbsnews.com/news/: https://www.cbsnews.com/news/illegal-crossings-u-s-mexico-border-down-94-percent-border-patrol-chief-says/
CISA. (2020, March 24) Retrieved from Critical Infrastructure Sectors -DHS: https://www.cisa.gov/critical-infrastructure-sectors
Department of Homeland Security (2025, May 28). Retrieved from How big is Homeland Security: https://duckduckgo.com/?q=how+big+is+homeland+security&atb=v441-1&ia=web
DIA. (2025) 2025_dia_statement_for_the_record. Retrieved from https://armedservices.house.gov/: https://armedservices.house.gov/uploadedfiles/2025_dia_statement_for_the_record.pdf
DOE. (2025) National-scada-test-bed. Retrieved from https://www.energy.gov/: https://www.energy.gov/oe/national-scada-test-bed
GOOGLE. (2025), June 28) Dimensions of the Chesapeake Bay. Retrieved from google.com: www.google.com
Harman, T. (2003). Lee’s Real Plan at Gettysburg. Mechanicsburg, PA: Stackpole Books.
https://free-printablemap.com/wp-content/uploads/2018/10/inland-waterways-of-the-united-states-wikipedia-with-navigable-waters-of-the-united-states-map.png (2018, October). Retrieved from https://free-printablemap.com/: https://free-printablemap.com/wp-content/uploads/2018/10/inland-waterways-of-the-united-states-wikipedia-with-navigable-waters-of-the-united-states-map.png
INFOSEC and INFOWAR Protection of Information Assets and systems (2021) ACO CYB 680 / 681 Fall Semester S1.
Intermodal-Service-Map. (2017, Aug) Retrieved from https://www.englandlogistics.com/: https://www.englandlogistics.com/wp-content/uploads/2017/08/Intermodal-Service-Map.jpg
Jean-Paul-Rodrigue. (Retrieved 2025, May). Major-maritime-shipping-routes-and-strategic-passages. Retrieved from https://www.researchgate.net/: https://www.researchgate.net/profile/Jean-Paul-Rodrigue/publication/315398501/figure/fig1/AS:599262685573122@1519886766175/Major-maritime-shipping-routes-and-strategic-passages.png
Julie J. C. H. Ryan, & Ryan, &. (2005). Proportional Hazards in Information Security Retrieved from https://onlinelibrary.wiley.com/: https://onlinelibrary.wiley.com/doi/10.1111/j.0272-4332.2005.00573.x
Kessler, G. C., & Sheppard, &. (2020) Maritime Cybersecurity: A Guide to Leaders and Managers. Middletown, DE: Independently Published.
Kessler, G., & Shepard, &. (2022). Maritime Cybersecurity: A Guide for Leaders and Managers, 2nd Edition. DE: Independently Published.
LINKEDIN Feed: 21 Dark Web Tools (2025) Retrieved from www.linkedln.com/feed: www.linkedln.com/feed
LINKEDIN Feed: Advanced Hackers Kit (2025) Retrieved from www.linkedln.com/: www.linkedln.com/
LINKEDIN Feed: Cybersecurity Domains (2025) Retrieved from https://www.linkedin.com/feed/: https://www.linkedin.com/feed/
LINKEDIN feed: Top 100 forensics tools (2025). Retrieved from www.linkedln.com: www.linkedln.com/feed
LINKEDIN feed: Top 8 Cyber Attacks (2025) Retrieved from LinkedIn Feed: www.linkedln.com/feed: www.linkedln.com/feed
Nichols, R. (2020) Chapter 14 Maritime Cybersecurity in (R. K. Nichols, & et.al, Unmanned Vehicle Systems & Operations on Air, Sea, Land. Manhattan, KS: NPP Press: https://www.newprairiepress.org/ebooks/35/.
Nichols, R. (2023). Kaltura_Capture_recording_-_RN – A-D Analysis -1 (2023_02_06 15_36_17 UTC).mp4″. Retrieved from “C:\Users\profr\OneDrive\Documents\COT 680-CYBR 680 CYBER SYSTEMS AND RISK MANAGEMENT SPRING 2023 – 15799\Kaltura_Capture_recording_-_RN – A-D Analysis -1 (2023_02_06 15_36_17 UTC).mp4”: “C:\Users\profr\OneDrive\Documents\COT 680-CYBR 680 CYBER SYSTEMS AND RISK MANAGEMENT SPRING 2023 – 15799\Kaltura_Capture_recording_-_RN – A-D Analysis -1 (2023_02_06 15_36_17 UTC).mp4
Nichols, R. (2023). Ryan Nichols Qualitative Information Risk Assessment Presentation. KSU.
Nichols, R. K. (2022) DRONE DELIVERY OF CBNRECy – DEW WEAPONS Emerging Threats of Mini-Weapons of Mass Destruction and Disruption (WMDD) Manhattan, KS: https://newprairiepress.org/ebooks/46/.
Nichols, R. K. (2022). UAS/CUAS Cyber terror implications/ Cyber Navigation Threats/Chinese UAS Intelligence/Capabilities and Impending invasion of Taiwan. Symposium Keynote, UND.
Nichols, R. K., Mumm, H. C., Lonstein, W. D., Ryan, J. J., Carter, C. M., Hood, J.-P., . . . and Jackson, M. J. (2020) Unmanned Vehicle Systems & Operations on Air, Sea, Land. Retrieved from https://newprairiepress.org/ebooks/35/: https://newprairiepress.org/ebooks/35/
Nichols, R. K., Mumm, H. C., Lonstein, W., Sincavage, S., Carter, C. M., Hood, J.-P., . . . and Shields, B. (2021) iDisruptive Technologies with Applications in Airline, Marine, and Defense Industries (2021). Retrieved from https://newprairiepress.org/ebooks/38/: https://newprairiepress.org/ebooks/38/
Nichols, R. K., Sincavage, S., Mumm, H., Lonstein, W., Carter, C., Hood, J. P., . . . and Harding, T. (2022) r ne Delivery of CBNRECy DEW Weapons: Emerging Threats of Mini-Weapons. Retrieved from https://newprairiepress.org/ebooks/46/: https://newprairiepress.org/ebooks/46/
Nichols, R., & Ryan, D. & (2000). Defending Your Digital Assets Against Hackers, Crackers, Spies, and Thieves. Washington, DC: McGraw-Hill.
Nichols, R., Diebold, M. C., & Johnson, &. (2024). Analysis of submarine cables in the western Pacific. Hattan, KS: KSU.
Nichols, R., Sincavage, S., Hood, J., Carter, C., & Mumm, H. (2022). Space Systems: Emerging Technologies and Operations. Manhattan: New Prairie Press.
NPR. (2024, December 31) i land-russia-severed-undersea-cable-shadow-fleet. Retrieved from https://www.npr.org/: https://www.npr.org/2024/12/31/nx-s1-5243302/finland-russia-severed-undersea-cable-shadow-fleet
Parker, D. B. (1998) Parker Hexad. Retrieved from https://en.wikipedia.org/wiki/Parkerian_Hexad: https://en.wikipedia.org/wiki/Parkerian_Hexad
Peerenboom J, F. R. (2001). Recovering from disruptions of critical independent infrastructures presented at the CRIS/DRM/IIT/NSF Workshop on Mitigating the Vulnerability of Critical Infrastructures to Catastrophic Failure, Washington. Retrieved from https://nap.nationalacademies.org/: https://nap.nationalacademies.org/read/18671/chapter/19#130
R.K..Nichols, Johnson, P., & Diebold, M. C. (2024). Analysis in many forms: An analysis of submarine cables in the western Pacific. Manhattan KSU.
R.K.Nichols. (n.d.) CRYPTOWIZ FOUR WINNS RECREATIONAL CRUISER Picture (iPhone) Rhodes River, MD.
Ryan, J., & & Ryan, D. J. (2006) https://www.academia.edu/20525921/Expected_benefits_of_information_security_investments. Computer and Security , p. https://www.academia.edu/20525921/Expected_benefits_of_information_security_investments Retrieved from https://www.academia.edu/20525921/: https://www.academia.edu/20525921/Expected_benefits_of_information_security_investments
Statista. (2024, June 21) Recreational vessels in the U.S. 1980-2023. Retrieved from https://www.statista.com: https://www.statista.com
STDL. (2025) w ss-territorial-data-lab-stdl_gnss-spoofing-activity. Retrieved from https://www.linkedin.com/: https://www.linkedin.com/posts/swiss-territorial-data-lab-stdl_gnss-spoofing-activity-7335164866665607168-0zl7/
TAIPEI Times (2025, January 11) Chinese ship cuts cable near Keelung Harbor. Retrieved from https://www.taipeitimes.com/: https://www.taipeitimes.com/News/taiwan/archives/2025/01/05/2003829674
UNCTAD. 2019 (updated) United Nations (2019) at Sheet #15: Maritime Transport Indicators. Conference on Trade and Development (UNCTAD). Retrieved from https://unctad.org/: https://unctad.org/en/PublicationChapters/tdstat44_FS13_en.pdf
USCG. (2024, October) DHS_uscg-maritime-response-activities-report-FY20-23 Retrieved from https://ohss.dhs.gov/sites/: https://ohss.dhs.gov/sites/default/files/2024-10/2024-1011_ohss_uscg-maritime-response-activities-report-FY20-23.pdf
Wikipedia. (2025) Notice to Mariners. Retrieved from https://en.wikipedia.org/: https://en.wikipedia.org/wiki/Notice_to_mariners
Wing, C. (2006, August 29). One-Minute-Nautical-United-States-Squadrons/. Retrieved from https://www.amazon.com/: https://www.amazon.com/One-Minute-Nautical-United-States-Squadrons/dp/0071479236
Endnotes
[1] Book 11 in the textbook series on UAS/CUAS/UUV/Space/Marine, written by Senior Professor Nichols and his Wildcat author teams.
[2] We highly recommend the purchase of their latest Edition (2nd Edition) (Kessler & Shepard, 2022)
[3] Chesapeake Bay is 4.5 miles to 48 miles wide (2.8 miles at its narrowest point) and 30 miles at its widest; its average depth is 21 feet, with a maximum depth of 174 feet; there are close to 11,684 miles of shoreline; the depth drops precipitously and varies to 5 feet or less (darn close to the Draft of CRYPTOWIZ) Draft is a critical factor in determining a boat’s safe navigation, certainly in shallow waters or when entering harbors. It is measured from the bottom of the hull of a powerboat to the waterline of the surface where the hull may intersect GOOGLE, 2025)
[4] USCGA inspected the cruiser annually. Additional Fortress anchors on board, and one gallon of potable water per Crew member or visitor per day on the cruise is provided. The electronics on CRYPTOWIZ were advanced: AIS, EPIRB, CAS, three Sonars and fish-finder, RADAR – multi-target, two VHF radios, SAT phone, ECDIS, Lightning arrestor; complete raster, vector, and water-protected NOAA charts 2x VCRs; backup electronics panel on gas, plus HVAC system; a HALON system installed in the engine compartment – Fire on board can be a catastrophic experience.
[5] All Crew used advanced PFDs with PLFs, strobes, and survival equipment. CRYPTOWIZ had duplicate electronics radios, sonar, and charts (both electronics and NOAA). Electronics were updated annually.
[6] The bilge pump needed to be replaced, as did the undersized Windlass bow anchor; both were replaced with much larger capacity resources; the anchor with a Delta designed for a 70-foot yacht, and the bilge with a five-times-capacity pump or more drag alarms in the middle of the night.
[7] In Kessler & Shepard (2022), cybersecurity is the only focus. In the current textbook, cybersecurity is an important consideration, but far from the spectrum of modern threats to MTS.
[8] Based on 202 data in 2025, these figures increased significantly.
[9] Check out the TOC for new issues.
[10] Although the author is almost in complete agreement with the cyber principles expressed in (Kessler & Shepard, 2022). We take great distance between the Vulnerability principle and Trumping Threats expressed in his latter chapters. Risk Assessment (Ryan–Nichols INFOSEC Assessments /Equations) shows that Risk is ONLY a practical function of Threats / Countermeasures. Both Vulnerabilities and Impact are essentially system constants and do not reduce Risk. They are system weaknesses that can be exploited or accounted for as defined by calculus and drop out of the overall Risk Assessment initial equation.
[11] A shipping line is a business that is subject to all the threats (cyber and otherwise) and vulnerabilities of every business. Concern is the use of third-party software and systems, and their origin. Control of this software and systems means that management is not always in control of its business; the downstream effects on the MTS can be significant.
[12] The author added the satellite component as it is critical in the modern threat vectors expressed later in this book.
[13] Relied heavily on the content with full attribution to the authors. Students will benefit because of their expansive vision.
[14] Note that (Nichols & Ryan, Defending Your Digital Assets Against Hackers, Crackers, Spies, and Thieves, 2000) was published two decades before (Kessler & Shepard, 2022) and accepted by the military and commercial communities.
[15] The real work behind the RN analysis was performed/developed by my colleagues in two papers: (Ryan & & Ryan, 2006) and (Julie J. C. H. Ryan & Ryan, 2005). We put RN into practice at RSA 2001 (Nichols & Ryan, Defending Your Digital Assets Against Hackers, Crackers, Spies, and Thieves, 2000)
[16] Note the function symbol => f, RA is a function of Threats / Countermeasures. It is not an equality.
[17] Satellites cover less than 5% of communications
[18] “The Parkerian Hexad is a set of six elements of information security proposed by Donn B. Parker in 1998. The Parkerian Hexad adds three additional attributes to the three classic security attributes of the CIA triad (confidentiality, integrity, availability) h Parkerian Hexad attributes are the following: Confidentiality, Possession or Control, Integrity, Authenticity, Availability, and Utility, These attributes of information are atomic in that they are not broken down into further constituents; they are non-overlapping in that they refer to unique aspects of information. An information security breach can be described as affecting one or more of these fundamental attributes of information.” (Parker, 1998)
[19] According to AP, on 5/18/ 2025, “NEW YORK — Federal transportation officials have launched an investigation into why a Mexican navy tall ship hit the Brooklyn Bridge in a collision that snapped the vessel’s three masts, killed two crew members, and left some sailors dangling from harnesses high in the air.
The ship known as the Cuauhtemoc was visiting New York on a global goodwill tour when the accident occurred Saturday evening. The vessel could be seen in multiple eyewitness videos traveling swiftly in reverse toward the bridge near the Brooklyn side of the East River; its three masts struck the bridge and snapped, one by one, as the ship kept moving. The initial investigation shows a failed mechanical system at fault. However, the root cause is still being investigated.
[20] Fire on board is one of the most dangerous threats a ship can encounter. CRYPTOWIZ was equipped with an oxygen depletion HALON system.
[21] Website covers email, public relations, partner portal, reservations, sales, essentially all the business functions for the line.
[22] Only a few examples of RA have been given to show that many of the RA elements are common to each protocol.
Media Attributions
- Figure 1-1 CRYPTO- WIZ
- Figure 1-2 A Night View from CRYPTO-WIZ on Eastern Chesapeake Bay
- Figure 1-3 The MTS Systems of Systems
- Figure 1-4 Global Shipping Routes
- Figure 1-5 World Map of Major Ports
- Figure 1-6 Inland-Waterways of the United States
- Figure 1-8 CIS Relationship 1
- Figure 1-9 CIS no 2
- Figure 1-10 Cybersecurity Domains cropped-1
- Figure 1-11 Advanced Hacker Kit cropped-1
- Figure 1-12 21 Dark Web Tools edited
- Figure 1-13 Top 8 Cyber Attacks cropped -1
- Figure 1-14 Top 100 Forensics Tools cropped-1
- Figure 1-15 RN Lethality Legend
- Figure 1-16 CARVER
- Figure 1-17 CARVER Variables
- Figure 1-18 MSHARPP Example
- Figure 1-19 OCTAVE
