3 Naval Strategic Importance of Guam and its Defense (Nichols & Diebold)
Abbreviations
ACE- Asia Connectivity Elements, Inc. in Guam
A/D – Attack Defense Scenarios with Risk Analysis of a Target
AAI – In Bangladesh, the Al Qaeda-linked Ansar-al-Islam terrorist organization
AOR- Area of Responsibility
AQIS – Al Qaeda in the Indian Subcontinent
ASEAN – Association for Southeast Asian Nations
AUSNZ – US/Partner Nation Security Force Assistance / SOF Assistance
BN – BN Task Force – Battalion Task Force
CT – Counter Terrorism
Densus 88 – Indonesian special counterterrorism squad Detachment 88
ESSCOM – Eastern Sabah Security Command – Malaysia
FTO – Foreign Terror Organization
GNC – Gateway Network Connections LLC
GTA – Guam Teleguam Holdings, LLC
I-PACOM – United States Indo-PACOM is a unified combatant Command of DoD, the largest geographic area covered by any US combatant command (USINDOPACOM, 2025)[1]
IS – Islamist Extremist
ISD – Singapore’s Internal Security Department
JAK/ JAD – In Indonesia, pro-IS groups Jamaah Ansharud Daulah (JAD) and Jamaah Ansharul Khilafah (JAK)
JI – Jemaah Islamiyah terrorist network
LEO – Law Enforcement Organization
PLAN – People’s Liberation Army Navy
PRC – People’s Republic of China (Navy)
RA – Risk Assessment based on a particular model (Ryan-Nichols, CARVER, MSHARPP, etc.)
SEA-US – Southeast Asia-United States Cable System in Guam
TCA – Trilateral Cooperative Agreement
TTP – Tehreek-e-Taliban Pakistan Terror Group
Student Learning Objectives
In this chapter, we will review and expand our previous chapter analysis. We will look at critical A/D Risk Assessments of the Spratly Islands, Hawaii, and Guam. Next, we will consider a Terrorist/Proxy attack on Piti and Tanguisson Point, Guam, and a Cyber-attack/surveillance of cable traffic routed through Hong Kong. Lastly, we will conclude with a discussion and analysis.
Special Note: It has been said that a picture is worth a thousand words. This chapter uses this maxim liberally. Special thanks to my coauthors Major Carter Diebold and SGT Major Ret. Peter Johnson. Their help and outstanding research were invaluable.
Undersea Cable Problem / Risk Review from Chapter 2.
Overall, there are significant layers of redundancy in the undersea cable networks and planned expansions that bypass the most significant Chinese and Russian threats within the 1st Island Chain. With this redundancy comes access. China has a state-owned interest in nearly every cable system and potential access to data at landing points that are non-US-controlled. It’s likely they already have or could gain a data advantage over the US using just undersea cable access points.
The South China Sea presents a significant issue for international data traffic, and the impact of an attack would be most impactful for Pacific Island nations, but not necessarily for US Operations.
Risk analysis indicates that individual attacks on specific landing points or cables would present few issues. Still, a few coordinated attacks on multiple cable systems in specific locations (i.e., Hawaii and Guam) may limit mission command of US Forces operating in the Pacific. Both China and Russia can do this.
Taiwan is at great risk of being disrupted with only a few landing stations, easily accessible cables, and a determined enemy with the capability to conduct disruptive attacks.
Cyber-attacks would be difficult to employ and achieve little effect. Multiple redundancies and security features obstruct access to full networks, and an attack would need to be extraordinarily widespread to achieve a noticeable effect.
A terrorist attack would have to attack multiple simultaneous targets to have an effect that isn’t covered in redundancy. Their limited presence in Mindanao and small groupings outside of the US make this very unlikely. BUT PRC ships have been seen targeting Manila. (SEALIGHT FOUNDATION, 2025) See Figure 3-1 PRC in the Philippines.
Note: A huge number of ships in the Philippines’ exclusive economic zone today– 17 China Coast Guard & 31 maritime militia visible on AIS (automatic information system), including on both sides of the Batanes islands in the north, nearest Taiwan.
That’s just the ones broadcasting–there are almost certainly more running “dark”. It’s not clear what has prompted Beijing to ratchet up its maritime aggression against Manila at this time.
Underwater submarine cables and landing points in the South China Sea (SCS) and Western Pacific are of serious concern to the mission command of US Forces. So, the issue for RA may be stated:
Issue 1: What cables and landing points have an outsized impact on mission command of US Forces in I-PACOM?
Starting with CARVER RA, we make the following assumptions.
CARVER Perspective: Facts and Assumptions
- Submarine cables can be attacked in international waters
- Guam is more accessible to the Chinese and Russians due to proximity and US Territory (not State) status
- Nodes in non-US-controlled territories have a higher potential for compromise. Treaty nations are less so than non-treaty.
- The risk of Intel Collection is always high.
- Economic impact is far less important than the mission ($ cost of lost financial transactions and cable/parts costs are not as important)
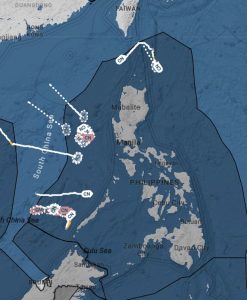
Figure 3-2 shows the CARVER Perspective: What cables and landing points have an outsized impact on mission command of US Forces in I-PACOM? (Nichols, Diebold, & Johnson, Risk Analysis of submarine cables in the Western Pacific -Part 2, 2024)
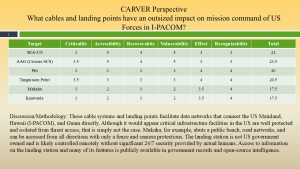
Figure 3-3 shows the CARVER Perspective: What cables and landing points have an outsized impact on mission command of US Forces in I-PACOM? (Nichols, Diebold, & Johnson, Risk Analysis of submarine cables in the Western Pacific -Part 2, 2024)

From Figures 3-2 and 3-3, we see our SCC targets. Let’s explore further. Starting with the Spratly Islands, one of the most contentious real estate in the SCS.
Risk Assessment – Spratly Islands
Issue 2: Problem – What is the risk associated with the Spratly Islands as a chokepoint for attacking undersea cables?
We will use the Ryan-Nichols (RN) qualitative Information RA Model. (Nichols R., Ryan-Nichols Qualitative Information Risk Assessment, 2023) (Nichols & Ryan, Defending Your Digital Assets Against Hackers, Crackers, Spies, and Thieves, 2000) (Nichols R., Kaltura_Capture_recording_-_RN – A-D Analysis -1 (2023_02_06 15_36_17 UTC).mp4″, 2023)
A breakdown of the key variables follows:
The Ryan Nichols Equation Perspective – Spratly Islands R.K. Nichols, Johnson, & Diebold, 2024)
Risk = (Threats X Vulnerabilities X Impact / Countermeasures)
- Accidents
- Fishing
- Commercial Traffic
- Environmental
- State Threat Actors – Russia and China
- Navy Surface Vessels (East Cable 885, South Cable 233, maritime militia, and coast guard)
- Navy Subsurface Vessels (Losharik, Poseidon, Yantar)
- Telecommunication Company Tapping/Intelligence Collection (Huawei Maritime, Big 3)
- Cyber Attack
- Non-State Threat Actors – ISIS, Activist Groups, Criminals
- Physical Attack
The Ryan Nichols Equation Perspective -Spratly Islands R.K. (K Nichols, Johnson, & Diebold, 2024)
- Risk = (Threats X VulnerabilitiesX Impact / Countermeasures)
- Infrastructure
- Landing Points: Physical (Telecommunications Equipment, Power Generation, Batteries, Control Room), Data (Encryption), Control Layers (Routing)
- The Physical Cable
- Repeaters (every 100km)
- Lack of redundancy (i.e., Vietnam, Brunei, Cambodia)
- Grouped Cable Landings – Physical distance
- Politics
- China’s 9 Dashed Line (Restricted access to cables for Non-Chinese)
- Non-US Control of data and physical infrastructure (Interdependence)
- OPSEC – Publicly available information on cables and landing stations
- Capability for Emergency Response (often measured in weeks, heavily reliant on four companies, restricted by China in the SCS)
The Ryan Nichols Equation Perspective -Spratly Islands (R.K.Nichols, Johnson, & Diebold, 2024)
Risk = (Threats X Vulnerabilities X Impact / Countermeasures)
- Banking and Finance
- $10 trillion in daily transactions
- International business and trade are completely reliant on these cables
- Internet traffic
- Roughly 95% of the world’s traffic happens over cables
- Satellites are incapable of handling traffic in the event of a mass disruption (.37%)
- ~1,300 Tbps of data are communicated over trans-Pacific cables as of 2023
- Military Communications and Mission Command
- The Ryan Nichols Equation Perspective -Spratly Islands
Risk = (Threats X Vulnerabilities X Impact / Countermeasures)
- Multi-Cable, Landline, Satellite redundancy
- US Controlled Hubs (Guam)
- New cable routing that does not land in Hong Kong and bypasses SCS (Echo, Bifrost, Apricot)
- Freedom of Navigation (US Navy)
- International Agreements
- Physical – Access Control, Barriers (i.e., fencing, cages, nylon/armor cables, two-person integrity)
- Data – Encryption (NIST, QKD, Post-Quantum Cryptography)
- Control – MARNS, Scans/Screening
Figure 3-4 shows the Ryan Nichols Equation Perspective -Spratly Islands Source: (R.K.Nichols, Johnson, & Diebold, 2024)
From the RN analysis, Issue 2 Spratly as a chokepoint for undersea cables, the Risks to the mission, US forces, and to other Pacific Island Nations are low, even though Threats are likely. Let’s look at the MSHARPP evaluation for Issue 2.
MSHARPP Perspective – Spratly Islands (R.K. Nichols, Johnson, & Diebold, 2024)
Mission: 3 (If attacked, unit/base could carry out its mission with some degradation)
Symbolism: 3 (Associated with economic or production capability for the defender)
History: 6 (Attacks against this type of target have occurred)
Accessibility: 9 (Easily accessible, standoff weapons can be employed)
Recognizability: 5 (Difficult to recognize in bad weather/night, requires some training for recognition)
Population: 1 (No or very few people present, attack causes no or few casualties)
Proximity: 1 (Target is isolated, no chance of unwanted collateral damage)
Total: 26
Under MSHARPP, this RA compares to a normal system component of a BN [2]task force’s infrastructure, despite being a large multinational infrastructure component.
Next, we move to Hawaii and look at its Landing Points.
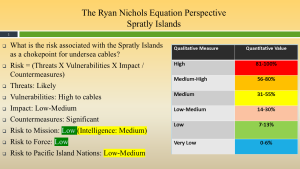
Figure 3-5 shows the Carver Perspective for Hawaii. Source: (Nichols, Diebold, & Johnson, Risk Analysis of submarine cables in the Western Pacific -Part 2, 2024)
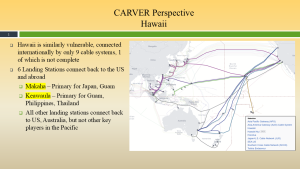
Figure 3-6 shows the CARVER Perspective Makaha Landing Station Source: (Nichols, Diebold, & Johnson, Risk Analysis of submarine cables in the Western Pacific -Part 2, 2024)

Figure 3-7 shows the CARVER Perspective Keawaula Landing Station. Source: (Nichols, Diebold, & Johnson, Risk Analysis of submarine cables in the Western Pacific -Part 2, 2024)

Figures 3-6 and 3-7 show us that both landing points connect directly to I-PACOM HQ.
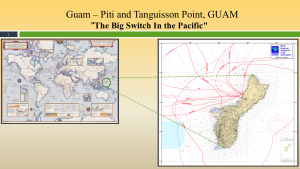
So next on our list is the extremely important Guam. Start with Figure 3-8 Guam – Piti and Tanguisson Point, Guam is known as the “Big Switch in the Pacific.”
Figure 3-8 shows Guam – Piti and Tanguisson Point, Guam, which is known as the “Big Switch in the Pacific.” Source: (Nichols, Diebold, & Johnson, Risk Analysis of submarine cables in the Western Pacific -Part 2, 2024)
Guam: Military Significance – Bullet points to consider:
- Spanish-American War: The Philippines was the objective of Spain & US. Guam was an important stop between the Americas and the Philippines.
- WWII: Japan, the forward line of defense against invasion. The US ran B-29 bombing missions for the rest of the war, the largest single element of the WWII Fleet support in the Pacific.
- Current: “It is now the US’s most critical operating location west of the international dateline,” Adm. Philip Davidson, US Indo-Pacific Command.
- Sovereign US Territory, no host nation requirements, or agreements
- Three US bases (1 of 11 Joint facilities) are the westernmost sovereign United States military installations, located approximately 3800 miles west of Hawaii, 2,800 miles north of Australia, and 1,300 miles east of the Philippines.
- Combined exercises with regional partner nations (Australia, Japan, India, Korea, Singapore, Indonesia)
- Joint Force Projection, ISR, Communications, and Logistical hub for Indo-PACOM
- Increased networking & bandwidth, JADC2, and ISR
- Largest regional fuel and ammunition storage facility
- Andersen Air Force Base: no permanently assigned aircraft, Rotational: Bomber Task Force (~150) and Tanker Task Force (~120)
- Andersen’s two runways, two landing zones, and 7.5 million square feet of ramp, capable of supporting every aircraft in the Department of Defense inventory.
- Andersen has the largest fuel storage and munitions storage capacity in the United States Air Force
- 36th Air Wing: 18 squadrons across five groups and operates out of Andersen AFB in Guam, Diego Garcia in the Indian Ocean, and Singapore
- Naval Base Guam, Apra Harbor (deep water port)
- Sub SQDN 15 (5 x LA Class Attack Subs), 2 x Sub Tenders, Helo SQDN-52 (MH-60’s), Military SEALIFT CMD, EOD MU-5,
- Camp Blaz (USMC’s first new base in 68 years): Provide the Fleet Marine Forces with operational functionality in order to enhance warfighting capabilities, facilitate the strengthening of coalition partnerships and joint region relationships, while projecting forward presence
- MAGTF & III MEF: 1,300 permanently stationed Marines and supports 3,700 additional Marines on rotating assignment
Sources: (NEWSWEEK, 2023); (Nichols, Diebold, & Johnson, Risk Analysis of submarine cables in the Western Pacific -Part 2, 2024); (Maritime Executive, 2023)
There are several views of Guam’s Defenses. See Figures 3-9 to Figure 3-13.
Figure 3-9 illustrates the Guam Department of Defense Facility Geography Source: R.K.Nichols, Johnson, & Diebold, 2024) (CIMSEC, 2023)
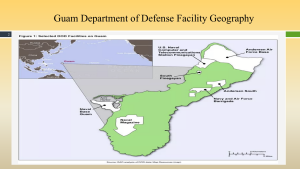
Figure 3-10 shows Guam Military Threats. Source: (Nichols, Diebold, & Johnson, Risk Analysis of submarine cables in the Western Pacific -Part 2, 2024)
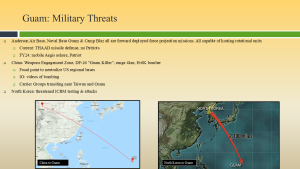
Of note in Figure 3-10 is the Chinese “Guam Killer,” whose focus is:
- China: Weapons Engagement Zone, DF-26 “Guam Killer”, range 4km; H-6K bomber
- Focal point to neutralize US regional bases
- IO: videos of bombing
- Carrier Groups transiting near Taiwan and Guam
Figure 3-11 illustrates China’s Guam Killer. Source: (Nichols, Diebold, & Johnson, Risk Analysis of submarine cables in the Western Pacific -Part 2, 2024)
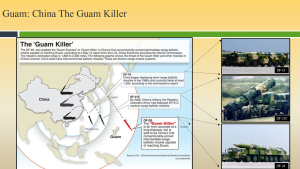
China has a significance military presence concentrating on Guam.
Figure 3-12 is PLAN’s Presence Near Guam. Source: (Nichols, Diebold, & Johnson, Risk Analysis of submarine cables in the Western Pacific -Part 2, 2024)
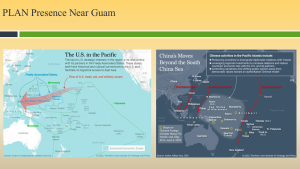
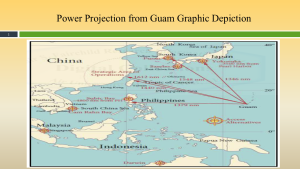
Figure 3-13 demonstrates Guam Power Projections. Source: (Nichols, Diebold, & Johnson, Risk Analysis of submarine cables in the Western Pacific -Part 2, 2024)
SE Asia Terrorist Operations (2014-2021)
Guam: Terror Threat 2021 and beyond – The US must take notice of the continuing Threats to the Guam AOR, to wit:
The Global Islamist Extremist Threat – 2021 and beyond
- Continuing salience of lone actors – In Indonesia, “stabbings were the most preferred tactic, followed by shootings and bombings” by both “pro-IS groups” and “individuals in Indonesia.”
- Involvement of women and family networks in combatant roles – In October 2020, a young Indonesian woman was arrested in Jolo Island in the southern Philippines for involvement in a suicide bombing plot. She was later identified as the widow of a slain Indonesian terrorist. She was also the daughter of an Indonesian husband-and-wife suicide attack team that had bombed a church, also in Jolo, in January 2019, killing at least 23 civilians.
- Challenge of rehabilitating and reintegrating returning foreign fighters and their families – reported that more than 50 Malaysians could be returning home from Syria, prompting discussions about how to properly rehabilitate and reintegrate them, as some returnees were “expected to include battle-hardened jihadists”.
- Role of diasporas – At least 1.1 million Rohingya refugees who fled persecution in Myanmar remain in Bangladeshi camps, vulnerable to exploitation by both criminal and terror networks – 18 radicalization cases within the Bangladeshi diaspora overseas were detected in 2020, of which 16 were in Singapore and two in the US.
- Diversity of terror financing mechanisms – In Bangladesh, the proscribed Allahr Dal extremist network received funding from supporters who provided a percentage of their monthly income to the group. The Central Asian Katibat Imam Al-Bukhari network, meanwhile, employed the hawala system to transfer funds, while other Central Asians engaged in robberies and even murder-for-hire operations. The Uyghur-based TIP terrorist network in Syria reportedly secured funds by plundering and selling public utilities equipment. While supporters of the resurgent Jemaah Islamiyah (JI) network in Indonesia donated 5-10 percent of their monthly salary to the network, JI has also developed legitimate businesses.
- Ideological ecosystems propagating violent Islamist perspectives – Such ecosystems included interconnected networks of social media platforms, online magazines, charismatic influencers, and certain organizational, educational, and religious spaces. For instance, in India in October, IS published a new monthly propaganda magazine, Sawt al-Hind(Voice of India), while Al Qaeda in the Indian Subcontinent (AQIS) rebranded its monthly magazine as Nawa-i-Ghazwat al Hind (Conquest of India). In Pakistan, the Tehreek-e-Taliban Pakistan (TTP) used its “propaganda magazine Mujallah Taliban to articulate its ideological position.” In Bangladesh, the Al Qaeda-linked Ansar-al-Islam (AAI) promoted the Ghazwatul Hind narrative or the eschatological last victorious battle of the Indian subcontinent. AAI also promoted extremist propaganda through Facebook, Messenger, and WhatsApp. In Indonesia, some members of the pro-IS groups Jamaah Ansharud Daulah (JAD) and Jamaah Ansharul Khilafah (JAK), “continued to conduct closed-door sessions for ideologically indoctrinating followers.”
Sources: (DKIAPSS, 2021); (Washington Institute, 2023); (Nichols & Ryan, Defending Your Digital Assets Against Hackers, Crackers, Spies, and Thieves, 2000); (Nichols, Diebold, & Johnson, Risk Analysis of submarine cables in the Western Pacific -Part 2, 2024)
SE Asia Terrorism: Additional Factors & Influences
Terrorism Influencers:
- Foreign Terrorist Organizations (FTOs)
- State sponsors of terrorism
- Lone actors
- Racially and ethnically motivated violent extremists (REMVEs)
FTOs Inspiring Lone Actors
- Since 9/11, there have been 37 attacks in the homeland inspired by al-Qaeda or ISIS
Domestic Violent Extremists
- 2011-2023, all 17 REMVE attacks by actors espousing the superiority of the white race. Online radicalization and inspired by foreign REMVE attackers and their manifestos.
SE Asia Terrorism: Countermeasures are delineated in Figure 3-14.
Figure 3-14 shows SE Asia Terrorism: Countermeasures. Source: R.K. Nichols, Johnson, & Diebold, 2024)

Guam – Piti and Tanguisson Landing Points
After researching the submarine cable network in the western Pacific as a whole and then the Spratly Island chokepoint, are we asking the right question about the target? Perhaps not.
What if Guam, the Intermediate Staging Base, and home to I-PACOM’s bomber fleet, was targeted? What about I-PACOM HQ in Hawaii? What are some of the key components that allow us to exercise mission command over vast distances to our forces inside partner nations like Japan, Korea, the Philippines, Thailand, Australia, New Zealand, etc.? Figures 3-15 to Figure 3-26 explore these two landing points (Piti and Tanguisson Landing Points).
Guam’s Cable System is shown in Figure 3-15.
Figure 3-15 shows Guam’s Cable System. Source: (Nichols, Diebold, & Johnson, Risk Analysis of submarine cables in the Western Pacific -Part 2, 2024)
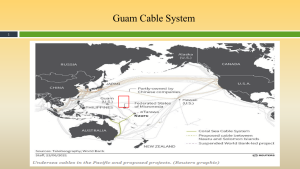
Figure 3-16 shows Guam – Piti and Tanguisson Landing Points. Source: (Nichols, Diebold, & Johnson, Risk Analysis of submarine cables in the Western Pacific -Part 2, 2024)
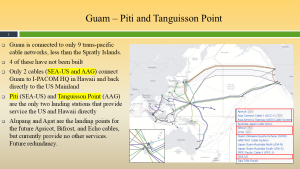
Figure 3-17 illustrates Guam – Piti and Tanguisson Landing Points. Source: (Nichols, Diebold, & Johnson, Risk Analysis of submarine cables in the Western Pacific -Part 2, 2024)
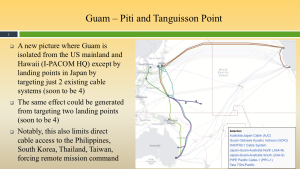
Figure 3-18 shows the Tanguisson Cable Landing Station. Source: (Nichols, Diebold, & Johnson, Risk Analysis of submarine cables in the Western Pacific -Part 2, 2024)
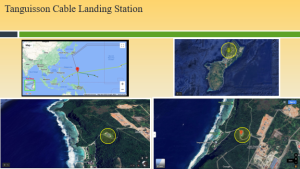
Figure 3-19 shows a different perspective of the Tanguisson Cable Landing Station. Source: (Nichols, Diebold, & Johnson, Risk Analysis of submarine cables in the Western Pacific -Part 2, 2024)
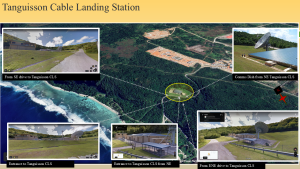
Figure 3-20 is an Analysis: Tanguisson CLS to Military Facility. Source: (Nichols, Diebold, & Johnson, Risk Analysis of submarine cables in the Western Pacific -Part 2, 2024)

Figure 3-21 shows Tanguisson Cable Landing Station – Carver Analysis. Source: (Nichols, Diebold, & Johnson, Risk Analysis of submarine cables in the Western Pacific -Part 2, 2024)

Piti-I Facts
- Piti-I Cable Landing Station is built for the landing of the Southeast Asia-United States Cable System (SEA-US) in Guam, owned by Teleguam Holdings, LLC (“GTA”).
- Piti-1 houses the SEA-US Cable System and the JGA South Cable System.
- Adjacent to GTA’s Piti-I CLS, there is a neutral cable landing station and data center, owned by Gateway Network Connections LLC (“GNC”). GNC is a Guam limited liability company, 51% owned by Asia Connectivity Elements, Inc. (“ACE”), a Guam corporation, and 49% owned by Teleguam Holdings, LLC (“GTA”).
- ACE is 50% owned by Russell Matulich (RTI CEO) and 50% by Choo Wee Tiong (Singaporean and Senior VP of RTI). Mr. Matulich holds a 99% voting and economic interest in RTI Connectivity.
- Although GNC owns the Piti-I CLS, RTI Solutions actually controls it. RTI applied through the FCC to operate Piti, and certified that they are NOT a foreign carrier or affiliated with a foreign country, which is positive.
- The GNC cable landing station is the terminal station for JGA North, JGA South, HK-G (withdrawn), and SxS (pending).
- There is a seamless interconnection between the Piti-I Cable Landing Station and the GNC cable landing station.
- Piti-1/GNC will provide onward connectivity and 24/7/365 technical support as part of a joint venture with RTI.
- GNC will be an 11,800-square-foot Type 3-designed data center with approximately 250 racks of capacity and 2 megawatts of power.
- Engineered to withstand Category 5 Hurricane conditions and tsunami flooding.
Source: R.K.Nichols, Johnson, & Diebold, 2024)
Figure 3-22 shows details of the Piti-I Cable Landing Station Location. Source: (Nichols, Diebold, & Johnson, Risk Analysis of submarine cables in the Western Pacific -Part 2, 2024)
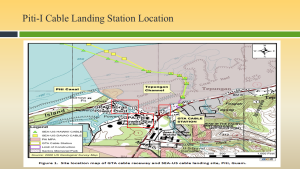
Figure 3-23 shows the Piti-I Cable Landing Station Location Distance to DoD Installations. Source: (Nichols, Diebold, & Johnson, Risk Analysis of submarine cables in the Western Pacific -Part 2, 2024)
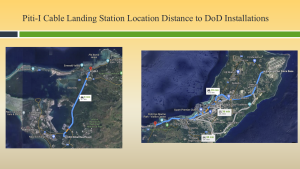
Figure 3-24 shows Guam Police Coverage. Source: (Nichols, Diebold, & Johnson, Risk Analysis of submarine cables in the Western Pacific -Part 2, 2024)
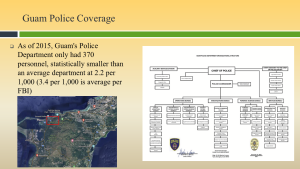
Guam Police Coverage
As of 2015, Guam’s Police Department only had 370 personnel, statistically smaller than the average department at 2.2 per 1,000 (3.4 per 1,000 is average per the FBI). Source: (R.K. Nichols, Johnson, & Diebold, 2024)
Figure 3-25 illustrates the Piti-I Cable Landing Station Power Station Target System. Source: (Nichols, Diebold, & Johnson, Risk Analysis of submarine cables in the Western Pacific -Part 2, 2024)

Figure 3-26 is Piti-I Cable Landing Station CARVER. Source: (Nichols, Diebold, & Johnson, Risk Analysis of submarine cables in the Western Pacific -Part 2, 2024)

Guam Recommendations based on CARVER Analysis and Lack of Local LEOs
- Depth of defense: Air, Land, Sea, Space, Cyber from PLA attacks
- 360 integrated defense – sensors, effectors (kinetic/non-kinetic)
- CT Standoff through partner nations, IA/IC, and CT operations
- Operational capability of additional undersea cables will increase redundancy (Apricot, Echo, Bifrost)
- Add CLS to the Critical Infrastructure list (if not already)
- Increase Physical Security measures at each location
- Add to Defended Asset List
We now shift to a new target, Hong Kong, which the Chinese control. SCC goes through Hong Kong, making intersecting/landing cables subject to cyber intrusion and surveillance.
Hong Kong History and Recent Context
The Hong Kong Island was ceded by China to Britain initially in 1842, after their first war.
A second war between China and Britain, between 1856 and 1860, resulted in the southern part of the Kowloon Peninsula and Stonecutters Islands being annexed after China’s defeat.
Hong Kong’s commercial development increased rapidly in the 1890s. Many Chinese emigrated to the US and built ties with the British-administered Hong Kong.
The New Territories, including the mainland and 235 offshore islands, were formally “leased” from China to Britain for 99 years starting in 1898. Talent from China moved to Hong Kong in the 1900s. Every industry, from medicine to finance, flourished in Hong Kong’s western-style economy and government, only loosely challenged by the Chinese Communist Party’s reform-inspired protests. The New Territories lease expired on June 30, 1997, with Hong Kong transitioning into a Special Administrative Region of China. The modern Hong Kong lives under the “one country, two systems, realizing many of the same benefits of British rule, but with Chinese oversight. China promised to retain the Hong Kong economic and social system for the next 50 years. This was an empty promise. Sources: (AXIOS, 2020) (Demchak, 2018) (US State Dept, 2022) (The Guardian, 2020)
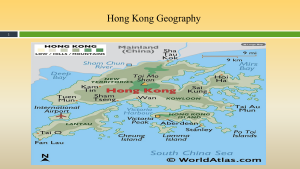
Figure 3-27 shows the Hong Kong Geography. Source: (World Atlas, 2025)
Hong Kong – Cyber Attack/Surveillance of Cable Traffic
This Risk Assessment seeks to address threats to both information collection and cyber-attacks against Hong Kong that will have impacts on the US in competition and conflict.
Hong Kong Specific Threats
How might China’s actions against Hong Kong translate to a threat against US National Security?
- Chinese Telecom Firms – China Telecom, China Mobile, China Unicom
- The Asia-America Gateway
- Lantu Island Landing Stations
- Cable Providers – Huawei Marine Networks (HMT) Technologies
Internet presence in China is the best way to be seen, provided it has access to all three major networks: China Telecom, China Unicom (merged with China Netcom), and China Mobile.
This option is only available if you have a Chinese company and an ICP certification.
The other Chinese internet option is to host your website in Hong Kong. The direct internet connection between Hong Kong and mainland China is costly, around $100 per MB per month. To reduce costs, Hong Kong hosting service providers often route mainland traffic from Hong Kong to mainland China through Japan and Taiwan, and Europe through the USA.
Connectivity with China
Many Chinese companies offer platform services in China, e.g., TMall Global; these services are hosted in Hong Kong with listing links on their Chinese platforms. In TMall Global, the list is called “Trading without borders.” They only use a Hong Kong-based internet presence if it has a connection to mainland China and Europe through the Middle East. If this is not an option, companies use hosting providers in Japan, Taiwan, or the West Coast of North America, USA, or Canada. Companies use Japan and Taiwan to host their internet presence to reduce costs, which is useful for large data volumes. Many corporations use Singapore for access to the South Asia market. This is a poor option for China, as your internet traffic will often travel through Taiwan or Japan before entering China. Singapore does not have a direct link to the mainland.
China. [3] Sources: (chinese-internet/being-seen-on-the-chinese-internet/internet-structure-in-china, 2025) (reuters, 2023) (The Guardian, 2020) (Politico)
AAG Associated Infrastructure with Chinese Interests is:
Submarine Cable Landing Installation in Tong Fuk Lantau for Asia Pacific Cable Network 2 (APCN2) Fiber Optic Submarine Cable System (AEP-069/2000).
• Telecommunication installation at Lot 591SA in DD328, Tong Fuk, South Lantau Coast, and the Associated Cable Landing Work in Tong Fuk, South Lantau for the North Asia Cable (NAC) Fiber Optic Submarine Cable System, Level 3 Communications Ltd (AEP-064/2000).
• Liquefied Natural Gas (LNG) Receiving Terminal and Associated Facilities (AEP 257/2006).
• Proposed 132kV Submarine Cable Route for Airport “A” to Castle Peak Power Station Cable Circuit (AEP 267/2007).
• Hong Kong Electric Co Ltd 132kV Submarine Cable Installation for Wong Chuk Hang – Chung Hom Kok 132kV Circuits (AEP-132/2002).
• FLAG North Asian Loop (AEP-099/2001). The Environmental Permit (EP-064/2000) was granted in June 2001.
• C2C Cable Network – Hong Kong Section: Chung Hom Kok, GB21 (Hong Kong Limited) (AEP-087/2000).
• New T&T Hong Kong Limited: Domestic Cable Route, New T & T (AEP-086/2000).
• East Asian Crossing (EAC) Cable System (TKO) (AEP-081/2000).
• East Asian Crossing (EAC) Cable System (AEP-079/2000).
Source: (CIENA)
Key Takeaways for AAG
- The point of GeoMesh is to eliminate the boundary between terrestrial and undersea cable networks, creating a management system that seamlessly routes traffic. This may bypass security infrastructure at landing stations when it does not facilitate Chinese surveillance goals.
- The AAG is becoming more capable (bandwidth, power, survivability, etc.) in line with modern undersea cables, making it a viable primary data pathway rather than an alternate
- Machine learning APIs have a supervised learning function that users with administrative access, such as Chinese overseers in Hong Kong or Telecom Companies with partial ownership over other landing stations, can influence.
- Without physically disrupting other landing stations, cables, or nodes, a system could be taught to believe that routing through Hong Kong and subsequently over terrestrial PoPs in China is optimal.
- OneControl UMS has visibility over the entire network
- VMWare presents remote risks, bypassing the physical security measures at the landing station.
Source: (CIENA) Also see Figure 3-29
Figure 3-28 is the Ryan Nichols Equation Perspective -Hong Kong Cyber Attack / Surveillance. Source: (Nichols, Diebold, & Johnson, Risk Analysis of submarine cables in the Western Pacific -Part 2, 2024)

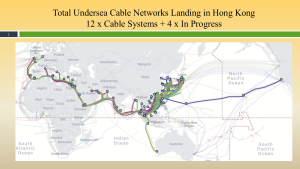
Figure 3-29 shows the Total Undersea Cable Networks Landing in Hong Kong. Source: (CIENA)
The last target of interest is Lantu Island with its connections to SCC and China.
Lantau Island Facts Source: (maps-hong-kong.com/lantau-island-tourist-map, 2025) (WIKI, 2025)
The largest island in Hong Kong
Part of the New Territories
Infrastructure Projects
Lantu Link
Hong Kong International Airport
Hong Kong Disneyland
Ngong Ping 360
Large expat population
Two cable landing stations (Lantau Island and Tong Fuk), but only the Lantau Island Cable Landing Station hosts AAG.
Lantu Island Landing Station Source: (WIKI, 2025)
Located on Tong Fuk Beach, ~6 miles from Hong Kong International Airport
Terminal for
Asia-America Gateway
Asia Pacific Cable Network (1 and 2)
Fiber-Optic Link Around the Globe: Europe, Asia
Figure 3-30 shows Lantau Island. Source: (maps-hong-kong.com/lantau-island-tourist-map, 2025)
Figure 3-31 shows Lantu Island Cable Landing Station Connections. Source: (Nichols, Diebold, & Johnson, Risk Analysis of submarine cables in the Western Pacific -Part 2, 2024)
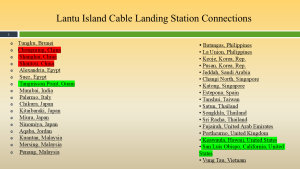
Figure 3-31 is instructive. Hong Kong intercepts the lion’s share of underwater communications in the western Pacific. It represents a huge threat to US interests. Figure 3-32 shows that its influence meansProfitt!
Figure 3-32 demonstrates that SCC equalsProfitt. Source: (Nichols R., “C:\Users\profr\OneDrive\Documents\HYSOL\C2SR Symposium October 28 2022 TOPIC-Cyber Terror CHINA TAIWAN-ECD ANTI-SPOOFING READY REV 12A 03182024.pptx”, 2022)
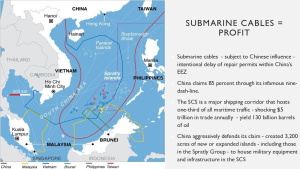
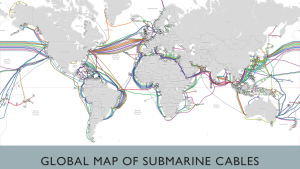
Figure 3-33 shows Global SCC Map (Nichols R. “C:\Users\profr\OneDrive\Documents\HYSOL\C2SR Symposium October 28 2022 TOPIC-Cyber Terror CHINA TAIWAN-ECD ANTI-SPOOFING READY REV 12A 03182024.pptx”, 2022)
Conclusions
Figure 3-33 sums up the global influence of the underwater submarine cable. However, this chapter has concentrated on the Western Pacific and US concerns for the security of the area and its military commands. Landing points and connections with Hong Kong are subject to Chinese surveillance and sabotage. US defense policy makers need to take note, as in the event of an invasion of Taiwan or a limited war with China, the communications structure of the entire Pacific might collapse.
References
AXIOS. (2020, September 9). China’s Spy Agencies Are Coming to Hong Kong — Here’s What That Means. Retrieved from https://www.axios.com/: https://www.axios.com/2020/06/09/china-hong-kong-intelligence
carnegieendowment.org/. (2024, December). baltic-sea-internet-cable-cut-europe-nato-security?lang=en. Retrieved from https://carnegieendowment.org/: https://carnegieendowment.org/emissary/2024/12/baltic-sea-internet-cable-cut-europe-nato-security?lang=en
chinese-internet/being-seen-on-the-chinese-internet/internet-structure-in-china. (2025). Retrieved from https://accesstochina.com/: https://accesstochina.com/chinese-internet/being-seen-on-the-chinese-internet/internet-structure-in-china
CIENA. (n.d.). AAG-Upgrades-Trans-Pacific-Submarine-Cable-Network-with-Ciena_prx.html. Retrieved from https://www.ciena.com/: https://www.ciena.com/about/newsroom/press-releases/AAG-Upgrades-Trans-Pacific-Submarine-Cable-Network-with-Ciena_prx.html
CIMSEC. (2023, February 1). Leaning on the Big Switch in the Pacific: Why The United States Dominates Pacific Telecom. Retrieved from https://cimsec.org/: https://cimsec.org/leaning-on-the-big-switch-in-the-pacific-why-the-united-states-dominates-pacific-telecom-infrastructure/
Demchak, C. U. (2018, June). China’s Maxim – Leave No Access Point Unexploited: The Hidden Story of China Telecom’s BGP Hijacking. Retrieved from https://digitalcommons.usf.edu -Military Cyber Affairs 3, no. 1: https://digitalcommons.usf.edu/mca/vol3/iss1/7/
DKIAPSS. (2021). the-global-islamist-extremist-threat-still-significant-in-2021/. Retrieved from https://dkiapcss.edu/nexus_articles/: https://dkiapcss.edu/nexus_articles/the-global-islamist-extremist-threat-still-significant-in-2021/ Link removed by Trump EO
Give your business visibility in China. (2025). Retrieved from https://services.accesstochina.com/: https://services.accesstochina.com/
Google. (2025). q=what+is+a+BN+Task+Force. Retrieved from https://www.google.com/: https://www.google.com/search?q=what+is+a+BN+Task+Force&sca_esv=61a9cbd74fd411b3&source=hp&ei=TKuWaNWzBMii5NoP4bCz0AU&iflsig=AOw8s4IAAAAAaJa5XA1pULOJlBizeaNX8P583CFQzIYT&ved=0ahUKEwjViaa60PyOAxVIEVkFHWHYDFoQ4dUDCBo&uact=5&oq=what+is+a+BN+Task+Force&gs_lp=
Julie J. C. H. Ryan, & Ryan, &. D. (2005). Proportional Hazards in Information Security. Retrieved from https://onlinelibrary.wiley.com/: https://onlinelibrary.wiley.com/doi/10.1111/j.0272-4332.2005.00573.x
maps-hong-kong.com/lantau-island-tourist-map. (2025). Retrieved from https://maps-hong-kong.com/: https://maps-hong-kong.com/lantau-island-tourist-map
Maritime Executive. (2023, April 25). “Why the U.S. Dominates the Pacific’s Subsea Cable Infrastructure.”. Retrieved from https://maritime-executive.com/: https://maritime-executive.com/editorials/why-the-u-s-dominates-the-pacific-s-subsea-cable-infrastructure.
NEWSWEEK. (2023, April 30). As the US Grows Guam’s Presence to Deter China, Wary Locals Are Denied A Choice. Retrieved from https://www.newsweek.com/: https://www.newsweek.com/us-grows-guam-presence-deter-china-wary-locals-are-denied-choice-1786778.
Nichols, R. (2020). Chapter 14 Maritime Cybersecurity. In R. K. Nichols, & et.al, Unmanned Vehicle Systems & Operations on Air, Sea, Land. Manhattan, KS: NPP Press: https://www.newprairiepress.org/ebooks/35/.
Nichols, R. (2022). “C:\Users\profr\OneDrive\Documents\HYSOL\C2SR Symposium October 28 2022 TOPIC-Cyber Terror CHINA TAIWAN-ECD ANTI-SPOOFING READY REV 12A 03182024.pptx”. Manhattan, KS: KSU.
Nichols, R. (2023). Kaltura_Capture_recording_-_RN – A-D Analysis -1 (2023_02_06 15_36_17 UTC).mp4″. Retrieved from “C:\Users\profr\OneDrive\Documents\COT 680-CYBR 680 CYBER SYSTEMS AND RISK MANAGEMENT SPRING 2023 – 15799\Kaltura_Capture_recording_-_RN – A-D Analysis -1 (2023_02_06 15_36_17 UTC).mp4”: “C:\Users\profr\OneDrive\Documents\COT 680-CYBR 680 CYBER SYSTEMS AND RISK MANAGEMENT SPRING 2023 – 15799\Kaltura_Capture_recording_-_RN – A-D Analysis -1 (2023_02_06 15_36_17 UTC).mp4”
Nichols, R. (2023). Ryan Nichols Qualitative Information Risk Assessment. Class Presentation KSU.
Nichols, R. K. (2022). SUAS/UAS Cyber terror implications/ Cyber Navigation Threats/Chinese UAS Intelligence/Capabilities and Impending invasion of Taiwan. CSR Symposium Keynote, UND. KSU.
Nichols, R. K., Sincavage, S., Mumm, H., Lonstein, W., Carter, C., Hood, J. P., . . . and Harding, T. “(2022). Drone Delivery of CBNRECy DEW Weapons: Emerging Threats of Mini-Weapons. Retrieved from https://newprairiepress.org/ebooks/46/: https://newprairiepress.org/ebooks/46/
Nichols, R., & Ryan, D. &. (2000). Defending Your Digital Assets Against Hackers, Crackers, Spies, and Thieves. Washington, DC: McGraw-Hill.
Nichols, R., Diebold, M. C., & Johnson, &. P. (2024). Risk Analysis of submarine cables in the Western Pacific -Part. Manhattan, KS: KSU.
NPR. (2024, December 31). finland-russia-severed-undersea-cable-shadow-fleet. Retrieved from https://www.npr.org/: https://www.npr.org/2024/12/31/nx-s1-5243302/finland-russia-severed-undersea-cable-shadow-fleet
Politico. (n.d.). justice-department-hong-kong-google-facebook-cable-326688. Retrieved from https://www.politico.com/: https://www.politico.com/news/2020/06/17/justice-department-hong-kong-google-facebook-cable-326688
R.K.Nichols, Johnson, P., & Diebold, M. C. (2024). Risk Analysis in many forms: An analysis of submarine cables in the Western Pacific -Part 1-2. Manhattan: KSU.
Reuters. (2023). investigates/special-report/us-china-tech-cables/. Retrieved from https://www.reuters.com/: https://www.reuters.com/investigates/special-report/us-china-tech-cables/
Ryan, J., & & Ryan, D. J. (2006). https://www.academia.edu/20525921/Expected_benefits_of_information_security_investments. Computer and Security, p. https://www.academia.edu/20525921/Expected_benefits_of_information_security_investments. Retrieved from https://www.academia.edu/20525921/: https://www.academia.edu/20525921/Expected_benefits_of_information_security_investments
SEALIGHT FOUNDATION. (2025, August 8). sealight-foundation_prc-philippines-china-activity. Retrieved from https://www.linkedin.com/posts/: https://www.linkedin.com/posts/sealight-foundation_prc-philippines-china-activity-7359406472092372992-Ivle/
TAIPEI Times. (2025, January 1). Chinese ship cuts cable near Keelung Harbor. Retrieved from https://www.taipeitimes.com/: https://www.taipeitimes.com/News/taiwan/archives/2025/01/05/2003829674
The Guardian. (2020, September 30). big-tech-firms-may-be-handing-hong-kong-user-data-to-china. Retrieved from https://www.theguardian.com/world/: https://www.theguardian.com/world/2020/sep/30/big-tech-firms-may-be-handing-hong-kong-user-data-to-china
The Guardian. (2020, September 30). big-tech-firms-may-be-handing-hong-kong-user-data-to-china. Retrieved from https://www.theguardian.com/: https://www.theguardian.com/world/2020/sep/30/big-tech-firms-may-be-handing-hong-kong-user-data-to-china
US State Dept. (2022). 2022-country-reports-on-human-rights-practices/china/hong-kong/. Retrieved from https://www.state.gov/: https://www.state.gov/reports/2022-country-reports-on-human-rights-practices/china/hong-kong/
USINDOPACOM. (2025, August 8). About-USINDOPACOM/USPACOM-Area-of-Responsibility/. Retrieved from https://www.pacom.mil/: https://www.pacom.mil/About-USINDOPACOM/USPACOM-Area-of-Responsibility/
Washington Institute. (2023). survey-2023-terrorism-threat-landscape. Retrieved from https://www.washingtoninstitute.org/: https://www.washingtoninstitute.org/policy-analysis/survey-2023-terrorism-threat-landscape
WIKI. (2025). Lantau_Island. Retrieved from https://en.wikipedia.org/: https://en.wikipedia.org/w/index.php?title=Lantau_Island&oldid=1150509992
World Atlas. (2025). maps/hong-kong. Retrieved from https://www.worldatlas.com/: https://www.worldatlas.com/maps/hong-kong
Endnotes
[1] USINDOPACOM – “The United States Indo-Pacific Command (USINDOPACOM) Area of Responsibility (AOR) encompasses about half the earth’s surface, stretching from the waters off the west coast of the US to the western border of India, and from Antarctica to the North Pole. There are few regions as culturally, socially, economically, and geo-politically diverse as the Asia-Pacific. The 38 nations comprising the Asia-Pacific region encompass 52% of the earth’s surface, home to more than 50% of the world’s population, 3,000 different languages, several of the world’s largest militaries, and five nations allied with the US through mutual defense treaties. Two of the three largest economies are located in the Asia-Pacific, along with 10 of the 14th smallest. The AOR includes the most populous nation in the world, the largest democracy, and the largest Muslim-majority nation. More than one-third of Asia-Pacific nations are smaller, island nations that include the smallest republic in the world and the smallest nation in Asia.” (USINDOPACOM, 2025)
“Approximately 375,000 US military and civilian personnel are assigned to the USINDOPACOM area of responsibility. U.S. Pacific Fleet consists of approximately 200 ships (to include five aircraft carrier strike groups), nearly 1,100 aircraft, and more than 130,000 Sailors and civilians dedicated to protecting our mutual security interests. Marine Corps Forces, Pacific includes two Marine Expeditionary Forces and about 86,000 personnel and 640 aircraft assigned. U.S. Pacific Air Forces comprises approximately 46,000 airmen and civilians and more than 420 aircraft. US Army Pacific has approximately 106,000 personnel from one corps and two divisions, plus over 300 aircraft and five watercraft assigned throughout the AOR from Japan and Korea to Alaska and Hawaii. Of note, component command personnel numbers include more than 1,200 Special Operations personnel. Department of Defense civilian employees in the Indo-Pacific Command AOR number about 38,000.” (USINDOPACOM, 2025)
[2] “A BN Task Force, short for Battalion Task Force, is a temporary grouping of units, typically led by a battalion commander, formed for a specific operation or mission. “A battalion is a military unit, typically consisting of up to one thousand soldiers. A battalion is commanded by a lieutenant colonel and subdivided into several companies, each typically commanded by a major or a captain. “In the United States Army and United States Marine Corps, a battalion is a unit composed of a headquarters and two or more batteries, companies, or troops. (Google, 2025)
[3] Text is a direct copy from services.accesstochina.com in order to capture the exact recommendations provided for connectivity with China. Source: (Give your business visibility in China, 2025)
