8
Chapter 8 Outline:
8.1 Communication Privacy
8.2 Data Privacy
8.3 Tips for Protection
Introduction
This chapter will discuss the last two domains, communication and information privacy, identified in the previous chapter. Indeed, these two domains form an integral part of what consumers think about (or not) when privacy comes to mind. Unlike some areas of law, consumers do have an enormous amount of control over what data companies use by controlling the amount of data the consumers give in the first place. Consumers are however, in some ways at the mercy of what data is collected and how that data is used. As was indicated in the previous chapter, privacy laws with respect to data in the United States are not always adequate to protect the privacy of consumers. In the absence of adequate legal protections, companies continuously develop novel ways of collecting data, sometimes with troubling consequences.
While individual data points, like whether an individual prefers Coke over Pepsi or scented over unscented lotion, are not particularly useful as single data points, but when multiple data points are combined and manipulated, corporations can create more individualized (yet sometimes creepy) predictions. For example, Target developed an algorithm to predict which stage of pregnancy a woman was in to send them targeted advertising. When customers purchased large amounts of prenatal vitamins that signaled they were usually within the first twenty weeks. If customers purchased large amounts of soap, cotton balls, hand sanitizer, and washcloths, that meant they were nearing their delivery date. Target would then send those women coupons for those items they might need in their near future. In 2011, a father became upset at a Target manager when his daughter had received ads targeted for pregnant women. The father later apologized to the manager after he found out that his daughter, as Target had predicted, was actually pregnant.
8.1 Communication Privacy
Learning Objectives
By the end of this section, you should be able to:
- Understand the importance of communication privacy
- Describe the function of the Electronic Communications Privacy Act
The third domain of communication privacy refers to workplace email monitoring, phone call recording, and wiretapping. Generally, employees do not have much expectation of privacy when on company grounds and using company equipment (i.e. computers, cell phones, etc.). In other words, employees should expect their emails to be read by management or their supervisors.
The Electronics Communications Privacy Act of 1986 (ECPA) updated the Federal Wiretap Act if 1968, which addressed the interception of hardline telephone conversation, but did not address electronic forms of communications. The ECPA contained three provisions. The first provision, referred to as the Wiretap Act prohibits intentional, actual, or attempted interception, use or disclosure or procurement of any wire, oral, or electronic communication. Keeping the 4th amendment in mind, the Supreme Court has assumed that individuals do have a reasonable expectation of privacy in in stored messages, and have found that individuals also have a reasonable expectation of privacy in private messages. However, courts have also found that employers generally do not violate the ECPA when they listen in on employees’ communications.
The second provision, called the Stored Communications Act, protects information stored by service providers. The third provision addresses pen registers (a device that captures the dialed numbers and related information to which outgoing calls or communications are made by the subject) and/or a trap and trace (a device that captures the numbers and related information from which incoming calls and communications coming to the subject have originated). Many states have also passed laws that are based on the federal ECPA.
8.2 Data Privacy
By the end of this section, you should be able to:
- Describe the importance of data privacy
- Understand how a data breach notification law works
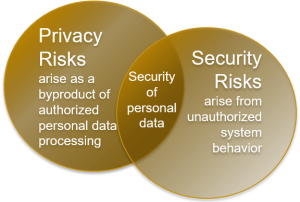 The fourth domain is data privacy. It goes without saying that the collection of consumers’ data is ubiquitous, and it follows that security of that data is of critical importance to consumers. FTC Commissioner Edith Ramirez noted in 2014, “if companies do not protect the personal information they collect and store, that information could fall into the wrong hands, resulting in fraud, identify theft, and other harm, along with potential loss of consumer confidence in the marketplace.” While data security (and in turn privacy) is more important than ever, more data breaches have occurred than ever before. Data breaches numbered nearly 1,300 in 2021, up from just over 1,100 in 2020.
The fourth domain is data privacy. It goes without saying that the collection of consumers’ data is ubiquitous, and it follows that security of that data is of critical importance to consumers. FTC Commissioner Edith Ramirez noted in 2014, “if companies do not protect the personal information they collect and store, that information could fall into the wrong hands, resulting in fraud, identify theft, and other harm, along with potential loss of consumer confidence in the marketplace.” While data security (and in turn privacy) is more important than ever, more data breaches have occurred than ever before. Data breaches numbered nearly 1,300 in 2021, up from just over 1,100 in 2020.
These data breaches fuel cybercrime and can impact millions of people. In 2016, Yahoo announced that 3 billion accounts were impacted by a data breach in 2013. In June 2021, the professional social network LinkedIn saw data associated with 700 million accounts posted on the dark web impacting 90% of its user base. Facebook has also suffered breaches with the most recent in 2019 with information from 553 million people published on a hacking forum.
Data breach notification laws
When a data breach occurs, victims of that breach must be notified. All 50 states have passed laws requiring private businesses and sometimes government entities to notify consumers when a data breach involves their personally identifiable information (PII). Specific requirements and timelines vary from state to state. Some states merely say the consumers must be notified within a reasonable time, while others give a specific number of days. The Illinois Personal Information Protection Act defines personal information as an individual’s first initial or full name and last name, social security number, driver’s license or ID number, account number or credit card number and password, medical information, health insurance information, username or email addresses and passwords, and unique biometric data (to include fingerprints, measurements, retina or iris image, or other digital representations of biometric data).
Data collectors must inform Consumers and the state attorney general at no charge if there has been a breach “in the most expedient time possible and without unreasonable delay.” That notice must include toll-free numbers and addresses for consumer reporting agencies, the FTC, and a statement that the consumer can obtain information from these sources about fraud alerts and security freezes. Data collectors include: the government, private and public universities, privately and publicly held corporations, financial institutions, retail operators, or any other that handles personal information. The consequences of a violation can be substantial. The attorney general can impose civil penalties and impacted individuals can file class action lawsuits with verdicts that can add up to millions of dollars in damages.
8.3 Tips for Protection
Learning Objectives
By the end of this section, you should be able to:
- Understand what steps consumers should take to protect themselves before and after a breach
- Describe some tips to prevent being a victim of a cyber crime
While it may seem that consumers are helpless and at the mercy of companies and the government when it comes to data security, consumers can proactively take steps to protect themselves. Global cyber security and privacy company, F-Secure makes the following recommendations on consumers can protect themselves before and after a breach:
- Make the effort to use strong, unique passwords.
- Do not volunteer private information.
- Whenever possible, go beyond passwords with 2-factor authentication.
- Monitor the integrity of personal information by using a trusted service to keep track of whether your data has been exposed online.
- Stay on top of your accounts by checking statements and activating any alerts financial institutions offer.
- Do not underestimate exposure to threats, as accounts are quickly opened and may be forgotten just as quickly.
Some additional tips on how consumers can protect themselves from being victims include:
- Know your data security status. In order to take charge of your data security, check to see if your information (phone number and email addresses) have been included in a breach.
- Do not use public wi-fi. Public wi-fi makes it easy for hackers to obtain information from those on unsecured networks.
- Use a Virtual Private Network (VPN). A VPN masks your IP address and cannot be traced.
- Do not share your phone number unless you have to. Phone numbers can be used to find other PII (like home address, email address, property ownership, criminal records, etc.).
- Consider a password manager. Reusing a password is a bad idea but most do it anyway. A password manager is a program that creates unique passwords for each account and stores them in one place.
- Know how to spot a phishing scam. This kind of scam uses an email or text messages that seems legitimate with the goal of soliciting personal information. Be on the lookout for messages from companies with a public email account (gmail, yahoo, etc.), a message informing you your account has been locked, offers that are too good to be true, messages meant to create a sense of urgency, and messages with typos.
- Be familiar with privacy polices. Though only about 9% of Americans actually read privacy policies, these policies inform consumer how those companies use that data in ways that you may not consent to.
Endnotes
Ashley Stahl, What You Need to Know to Protect Your Data Online, Forbes (2021), https://www.forbes.com/sites/ashleystahl/2021/06/04/what-you-need-to-know-to-protect-your-data-online/?sh=141019e63db5.
Electronic Communications Privacy Act of 1986 (ECPA), Bureau of Justice Assistance (n.d.), https://bja.ojp.gov/program/it/privacy-civil-liberties/authorities/statutes/1285.
Illinois Data Breach Law, Lubin Austermuehle (n.d.), https://www.thebusinesslitigators.com/illinois-data-breach-law.html.
Jason Sattler, How Data Breaches Fuel Cyber Crime for the Whole Family, F-Secure (2021), https://blog.f-secure.com/the-walking-breached/.
Michael Hill and Dan Swinhoe, The 15 Biggest Data Breaches of the 21st Century, CSO (2021), https://www.csoonline.com/article/2130877/the-biggest-data-breaches-of-the-21st-century.html.
