16.3 Identification Technologies
Modern supply chains handle millions of products, shipments, and transactions daily, making it difficult to track and manage everything manually. Businesses need a way to automatically capture, store, and process information about products, shipments, and assets across their supply chain. This is where identification technologies come into play. These technologies help businesses identify, track, and manage products efficiently, ensuring that the right items are in the right place at the right time.
Identification technologies work by assigning a unique code or label to an item, allowing companies to scan and retrieve information quickly. For example, when a product arrives at a warehouse, scanning a barcode or RFID tag can instantly update inventory records instead of relying on manual counting and data entry. This reduces errors, improves speed, and ensures that supply chain operations run smoothly. Without identification technologies, businesses would struggle with missing shipments, incorrect stock levels, delays in processing orders, and even fraud.
Before adopting an identification technology, businesses must consider several key factors:
- Cost: Some technologies, like barcodes, are inexpensive to print and use, while others, like RFID, require costly hardware and software.
- Accuracy and Reliability: The technology should minimize errors—barcode scanners need a clear line of sight, while RFID can scan multiple items at once.
- Ease of Use: Employees must be able to operate scanners or readers efficiently to ensure smooth operations.
- Security: Identification technologies must prevent counterfeiting and unauthorized access, especially for high-value goods.
- Scalability: The system should work for both small businesses and large enterprises, handling a growing number of products and transactions as the company expands.
By choosing the right identification technology, companies can streamline inventory tracking, reduce errors, and improve overall supply chain efficiency. The following section explores some of the most widely used identification technologies in supply chain management.
Core Technologies:
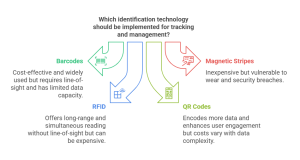
Barcodes: The most widely used identification technology, barcodes consist of a series of lines and spaces representing product information. They were first popularized in grocery stores (like the iconic scan on a pack of Wrigley’s gum in 1974) to streamline checkout and inventory management. Standardization by GS1 ensures global recognition, allowing apps like price scanners on smartphones to identify products across borders. For instance, Amazon uses barcodes extensively in their warehouses. Each item received at an Amazon fulfillment center is scanned, allowing the company to track location, manage inventory levels, and ensure efficient order fulfillment. While cost-effective and versatile, barcodes require direct line-of-sight for scanning. Imagine a scenario where a box full of electronics is packed tightly, and the barcode on a specific item is obscured by another box. Scanning becomes impossible. Additionally, barcodes offer limited data capacity and are susceptible to damage or dirt. Furthermore, their effectiveness relies on accurate databases, which can add maintenance costs. However, the ease of reprinting barcodes also presents a security risk, as counterfeit products with replicated codes could potentially infiltrate the supply chain.
Magnetic Stripes: Commonly found on credit cards and access cards, magnetic stripes store data on a magnetic film. Swiping the card through a reader retrieves the information. Magnetic stripes are inexpensive but vulnerable to wear and tear, data corruption, and security breaches.
Radio Frequency Identification (RFID): This technology uses radio waves to identify and track objects with attached tags. Tags can be passive (powered by the reader’s signal) or active (with their own battery). Passive tags, used for applications like retail inventory tracking, are cheaper but have shorter reading ranges. Active tags, employed for high-value assets like pharmaceuticals or shipping containers, offer longer ranges but are more expensive. RFID offers the advantage of reading multiple tags simultaneously and without direct line-of-sight, overcoming the limitations of barcodes in cluttered environments. For example, clothing giant Zara utilizes RFID tags to track garments throughout their supply chain, from manufacturing to stores. This allows for better inventory management, reduced stockouts, and improved efficiency. However, RFID systems can be expensive to implement and susceptible to interference from metals or liquids.
QR Codes (Quick Response Codes): These two-dimensional barcodes encode significantly more data than traditional barcodes and can be scanned from any angle using smartphones. This characteristic makes them ideal for mobile payments, promotional tracking, and personal identification. The ability to scan QR codes with smartphones fosters interactive marketing and instant access applications, enhancing user engagement. QR codes are becoming increasingly popular in the food and beverage industry. For instance, Coca-Cola uses QR codes on their cans and bottles to link consumers to interactive marketing campaigns or provide nutritional information.
The cost of implementing these technologies varies. Barcodes are the most affordable, while RFID systems require a significant initial investment in tags and readers. QR codes fall somewhere in between, with the cost depending on the complexity of the data encoded.
In conclusion, identification technologies are fundamental tools for managing complex supply chains. Understanding their strengths and weaknesses allows businesses to select the most appropriate solution for their needs, ensuring efficient, secure, and transparent operations.